TABLE OF CONTENTS
See Virtru In Action
Sign Up for the Virtru Newsletter


This article was originally published by FireEye.
As the cybersecurity threat landscape continues to evolve and attacks become increasingly sophisticated, security operations center (SOC) teams need to incorporate email and file protection, sharing, and access to event logs that correlate with endpoint and network activity. All of this can provide organizations with comprehensive security intelligence to help strengthen monitoring workflows, quickly flag incidents, trace their impact and enable immediate remediation.
A recent collaboration between encryption company Virtru and FireEye does just that. Mutual customers get persistent protection, control and visibility of sensitive email and file attachments as they travel in and out of customers’ environments. For SOC teams, this means that as content is created and shared in the cloud, they can maintain granular visibility into who has accessed protected data, when and where they did it, and for how long.
Customers can use the Virtru Audit Export API to push telemetry to the FireEye Helix security operations platform. Together, Virtru and FireEye provide customers with advanced user-behavior analytics, a process that utilizes set data loss prevention (DLP) rules to identify abnormal email usage and suspicious or malicious activity and gives insight into who is sharing sensitive data. In the event of a data breach, or if a user’s credentials become compromised, Virtru can immediately disable access via its advanced access control capabilities.
FireEye Helix has more than 70 rules set up for Virtru that generate alerts for SOC analysts to review. These alerts are normal day-to-day activities that Virtru customers would perform such as:
There are five Virtru Dashboards in FireEye Helix that visualize what alerts (Figure 1) are happening in an environment: Email Information, Email Advanced Control Usage, Organizational Events, User Events and User Activations. These dashboards (seen in Figure 2) allow SOC analysts to quickly view key information and take action.
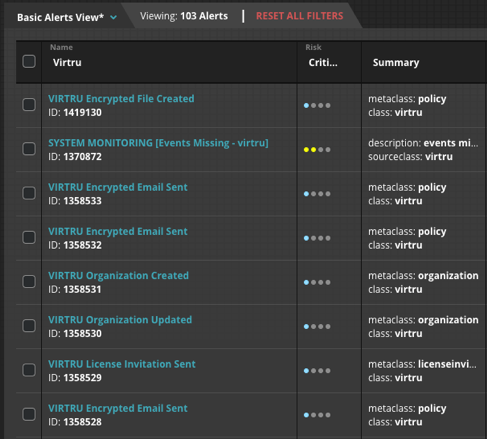
Figure 1: Virtru Alerts In FireEye Helix
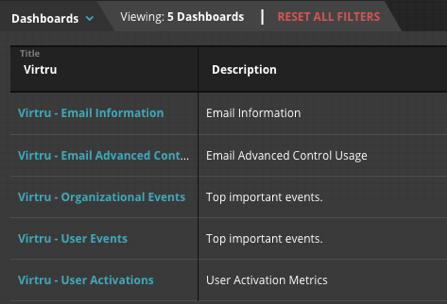
Figure 2: Virtru Dashboards in FireEye Helix
To learn more about this integration visit the FireEye Market and email the contacts listed to get the integration started today. Learn more about Virtru by visiting their website. FireEye and Virtru are also working on FSO Orchestration Plugins to automate the revoke capabilities.

The editorial team consists of Virtru brand experts, content editors, and vetted field authorities. We ensure quality, accuracy, and integrity through robust editorial oversight, review, and optimization of content from trusted sources, including use of generative AI tools.
View more posts by Editorial Team










Contact us to learn more about our partnership opportunities.