TABLE OF CONTENTS
See Virtru In Action
Sign Up for the Virtru Newsletter



This summer the Virtru Developer Hub was released to help developers implement new ideas to help protect and gain greater control of data. Since then, we have engaged with developers, researchers, and security and privacy advocates and learned many novel use cases where the Virtru SDK can help organizations simultaneously securely share and derive value from even their most sensitive data.
To explore these use cases and to inspire innovative, privacy-preserving data protection solutions, we also introduced a privacy engineering challenge. Today, we are pleased to announce the winner of this challenge. Krish Suchak’s Audit Map submission introduced geolocation features to help prevent unauthorized data access.
Spatial intelligence has helped improve fraud detection and is foundational for many anomaly detection algorithms. If you book a flight, you may immediately get an email informing you that your credit card security will be updated during those dates to reflect the destination location. Use your credit card abroad and receive a text asking for purchase confirmation. But what if you don’t have the resources of a Fortune 500 company, but still want to leverage location data to help detect unauthorized data access? The privacy engineering challenge winner—Audit Map—combines geofencing with the Virtru SDK to leverage location analytics to alert and revoke unauthorized data access.
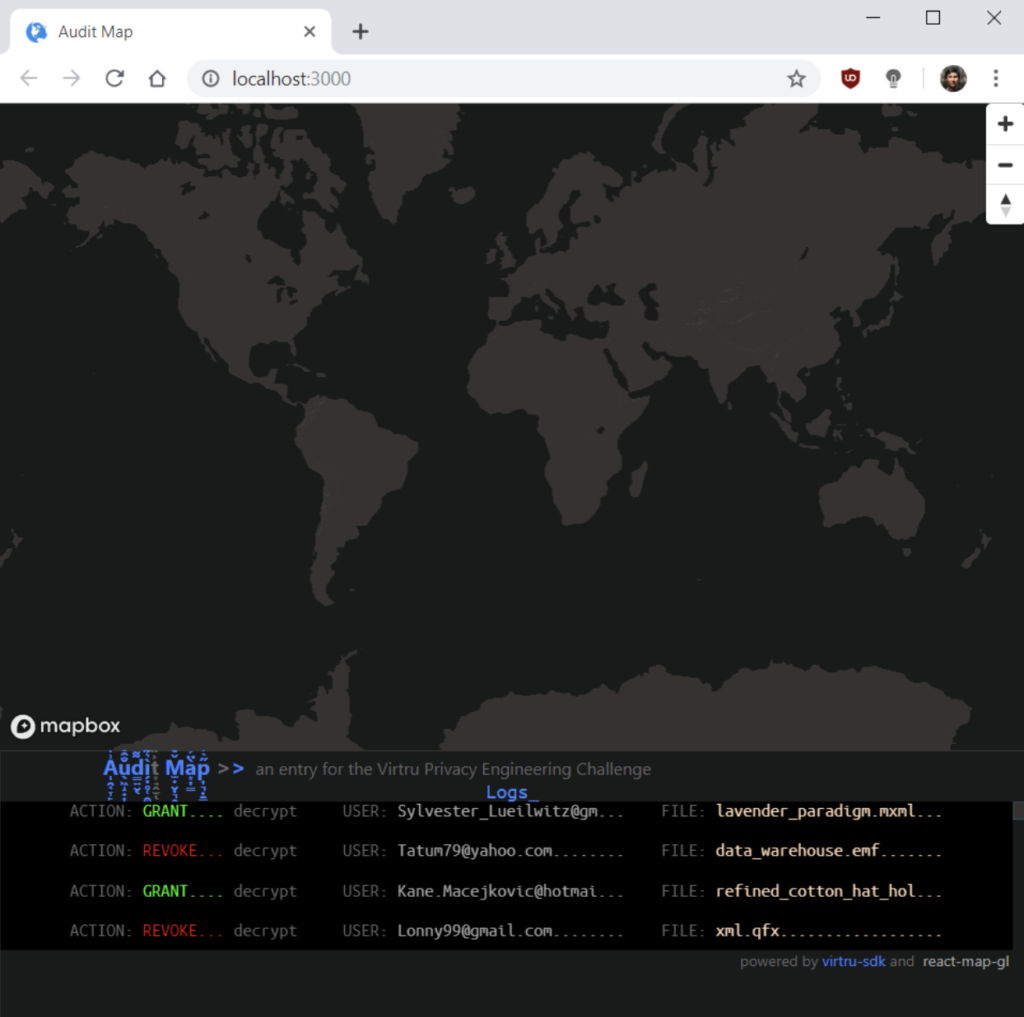
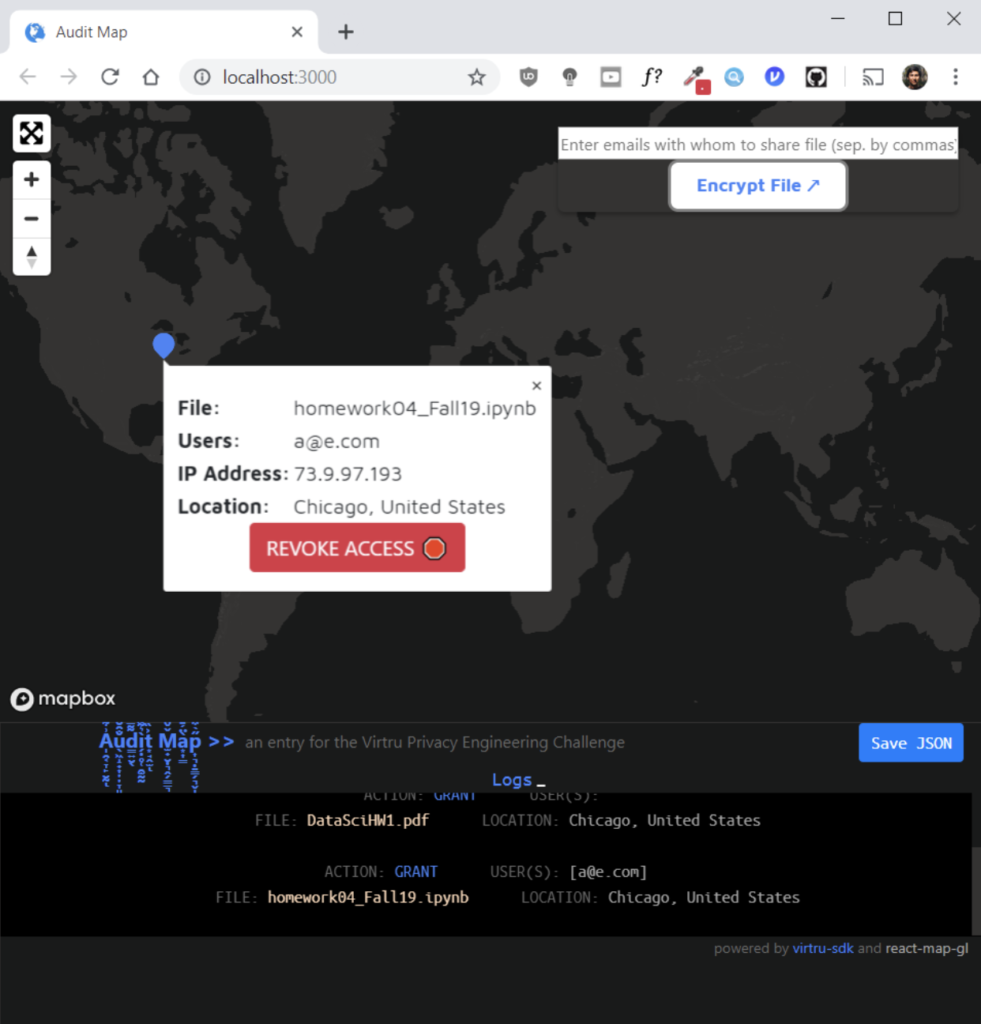
Audit Map integrates MapBox and the Virtru SDK to visually analyze and flag unauthorized data access. By embedding an IP address into the encrypted file, the data owner can audit all of the locations where the file access is attempted. Within the intuitive interface, the data owner can look at the location and determine whether to grant or revoke any access request. The audit log can help data owners determine whether to block specific latitude and longitude coordinates from data access. By adding location intelligence to the protect and track features within the Virtru SDK, Audit Map provides additional information to maintain greater visibility over unauthorized data access.
There is both a regulatory compliance application as well as unauthorized access application. For instance, Export Administration Regulations (EAR) prevent the export of specific information to certain foreign entities. Audit Map can help identify if there is attempted access of information that falls under EAR. At the same time, this visualization can help make audit logs and data accessible and easy to explore, especially if extended to include SIEM data as well.
The Audit Map demonstrates the viability of protecting and sharing data with greater control. Our recently launched technical blog provides deeper technical details on Audit Map as well as additional applications of the Virtru SDK—from securing S3 buckets to securely sharing Google Docs. As a community, we must work together to find innovative ways to control our data and our privacy. We are driven by the belief that greater data protection and control can and must co-exist with data sharing and portability. We look forward to even greater community engagement in 2020 to help empower individuals and organizations with greater data control and privacy.

Will is Virtru's CTO and Co-Founder. Prior to Virtru, Will specialized in cloud analytics and security architecture at the NSA and pioneered the Trusted Data Format - now an open standard and the foundation of Virtru's security suite. He holds 25 patents and is a renowned expert on cryptography, data policy, and analytics.
View more posts by Will Ackerly










Contact us to learn more about our partnership opportunities.