TABLE OF CONTENTS
See Virtru In Action
Sign Up for the Virtru Newsletter

When you’re managing data in the cloud, it’s smart to ensure you’re protecting the keys to your private, encrypted information. If you need to comply with regulations like CJIS, ITAR, or EAR, this level of security may be essential. Whether you’re using Google Workspace or Microsoft 365, Virtru offers multiple key management options to safeguard data everywhere it’s created, stored, and shared, preventing third parties from ever accessing unencrypted content.
By implementing a distributed architecture with dual layers of protection, Virtru’s customers can ensure they maintain total control over exactly who can access their encryption keys — and prevent access by their cloud provider.
While Virtru’s customers can entrust their keys to be managed by Virtru, Virtru’s Customer Key Server (CKS) provides an additional layer of security to meet global data protection needs, data residency, and data sovereignty. This option gives Virtru customers complete control over who can access their data. Prevent any third parties from accessing your encryption keys, including security and cloud-hosting vendors, or governments who could subpoena your providers.
Unlike cloud-managed, Bring Your Own Key (BYOK) approaches that force you to trust the vendor, Virtru can never access your private keys. BYOK arrangements are like getting a safety deposit box but then letting the bank store its key. The cloud provider or security vendor can still access the underlying plain-text content. Virtru is the first Zero Trust key distribution service in which no third party can ever access unprotected content or the keys that grant access. 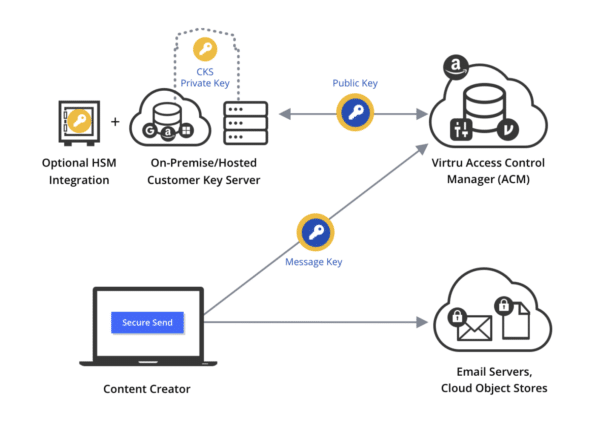
The Virtru CKS creates an additional key pair to protect underlying encryption keys that never leaves your environment for true “hold your own key” security. When you encrypt an email, a message key is generated, which is then encrypted with a public key. The Virtru Access Control Manager (ACM) manages and authenticates key exchanges but cannot access your data at any time. The CKS then hosts a private key that is needed to decrypt the public key and unwrap the message key. This CKS private key never leaves your environment. You can host the key on-premise, in a private cloud, or on any public cloud service and maintain visibility over all encryption key exchanges and policies.
You should consider the Virtru CKS if you’re looking to:
To learn more about how your organization can implement Zero Trust encryption key management with the Virtru Customer Key Server, contact Virtru today to start the conversation.

The editorial team consists of Virtru brand experts, content editors, and vetted field authorities. We ensure quality, accuracy, and integrity through robust editorial oversight, review, and optimization of content from trusted sources, including use of generative AI tools.
View more posts by Editorial Team










Contact us to learn more about our partnership opportunities.