Why Use Virtru's FIPS 140 2 Compliant Encryption?
Virtru's data-centric security approach to a FIPS 140 2 encryption software fits seamlessly into your existing workflows and apps, so you can start sharing secure files and emails right away.


Virtru's data-centric security solutions meet FIPS encryption standards and are FIPS 140-2 validated, providing military-grade protection for sensitive data.
Book a DemoMORE THAN 6,100 CUSTOMERS TRUST VIRTRU FOR DATA SECURITY AND PRIVACY PROTECTION.



Virtru's data-centric security approach to a FIPS 140 2 encryption software fits seamlessly into your existing workflows and apps, so you can start sharing secure files and emails right away.

Virtru's products leverage AES 256 encryption for strong, military-grade data protection. The Trusted Data Format underpinning Virtru's technology, invented by our CTO and Co-Founder during his time at the NSA, is an open standard embraced by ODNI and the intelligence community.
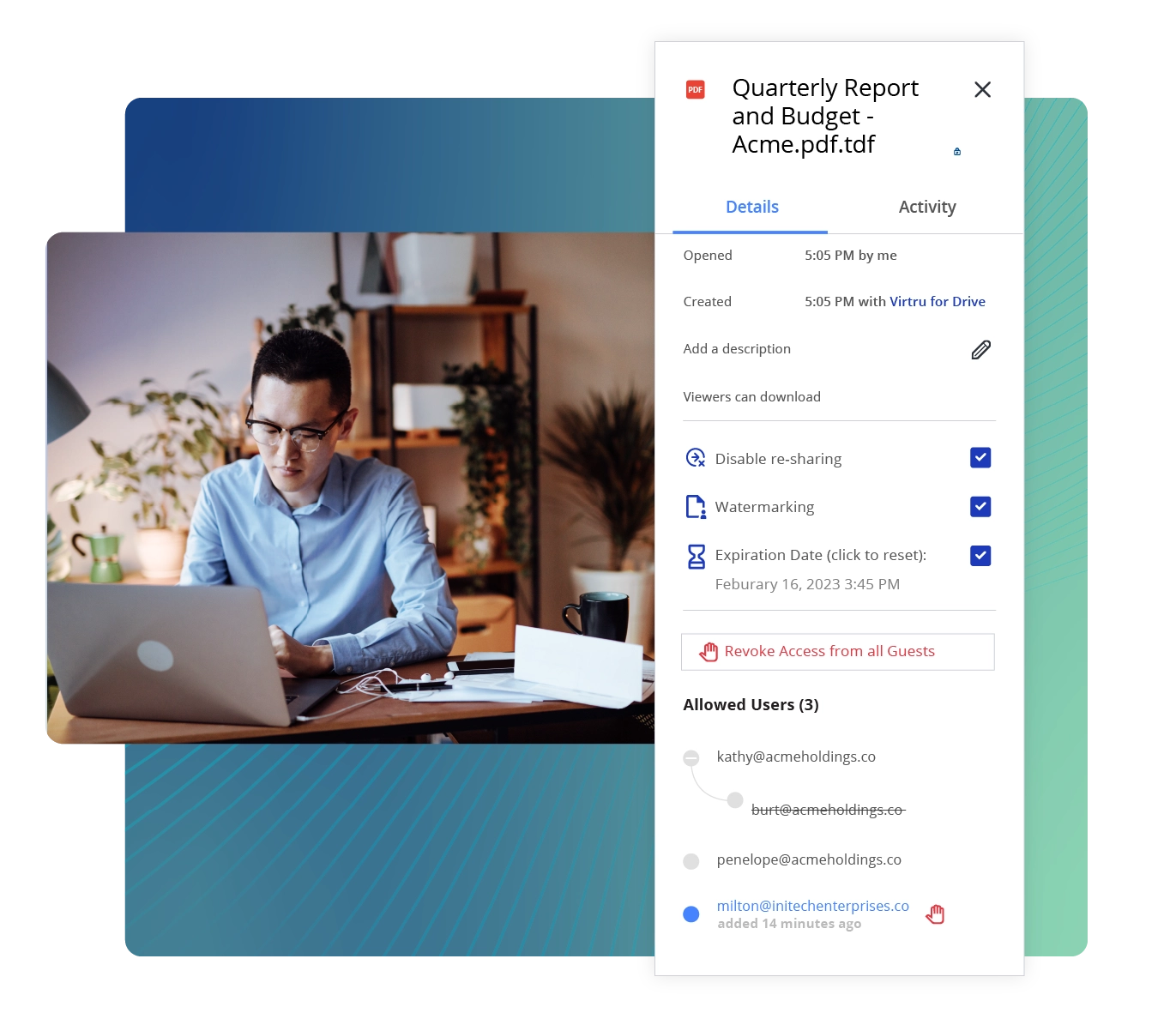
What makes Virtru unique is that it's also incredibly easy to use: Recipients of encrypted data don't have to create new passwords or install any software. And Virtru integrates with the email and productivity apps you already use every day.

With Virtru, it won't take you months to get started on implementing a FIPS encryption software: Deploy our email encryption for Outlook, Gmail, and apps like Zendesk in less than a day — and deploy our Gateway with the help of our exceptional customer support and engineering teams.
Whether you’re sending an email, attachment, large file, or sensor data, Virtru lets you securely collaborate internally and externally.
Control data flowing in and out of your organization, including the ability to revoke access to encrypted content after it's been shared.
Put automated data protection in place, including Data Loss Prevention (DLP) rules, encryption and decryption gateways, and more — with powerful audit visibility.
When you can confidently and securely share information, big things happen: silos disappear, ideas flow, and innovation thrives.


"With Virtru, it's it's been refreshing. I just really wish more of my stuff worked this way because it was a relatively easy experience for a really complex problem."
Karl Jankowski
Information Security and Privacy Manager
WealthForge
Read the Case Study

“AFRL invests in its collaboration tool stack by using the Google Workspace suite to foster that simple, easy-to-use collaboration, along with Virtru’s client-side and server-side data protection to provide additional layers of security for sensitive information.”
Dr. Dan Berrigan
Lead, Collaborative Tools, AFRL Digital War Room
Air Force Research Laboratory
Read the Case Study

“The reason we closed the deal was not just because of the solution. It was because of the way [the Virtru sales and engineering teams] treated us. It's a great partnership.”
Virtru Customer
IT Director
Global Engineering Firm
Read the Case Study


"With Virtru, it's it's been refreshing. I just really wish more of my stuff worked this way because it was a relatively easy experience for a really complex problem."
Karl Jankowski
Information Security and Privacy Manager
WealthForge
Read the Case Study

“AFRL invests in its collaboration tool stack by using the Google Workspace suite to foster that simple, easy-to-use collaboration, along with Virtru’s client-side and server-side data protection to provide additional layers of security for sensitive information.”
Dr. Dan Berrigan
Lead, Collaborative Tools, AFRL Digital War Room
Air Force Research Laboratory
Read the Case Study

“The reason we closed the deal was not just because of the solution. It was because of the way [the Virtru sales and engineering teams] treated us. It's a great partnership.”
Virtru Customer
IT Director
Global Engineering Firm
Read the Case Study