Deploy Easy-to-Use Data Security Across Your Organization
Virtru works seamlessly with data classification tools to provide contextual security for data that must be shared.


Virtru works alongside data classification software and data labeling tools to protect and encrypt sensitive, confidential information — without sacrificing the ability to share it with the right people, at the right time.
Book a DemoMORE THAN 6,100 CUSTOMERS TRUST VIRTRU FOR DATA SECURITY AND PRIVACY PROTECTION.
/Master-Electronics%20copy.webp)

/resource%20-%20forge%20institute/forge%20logo.png)





Virtru works seamlessly with data classification tools to provide contextual security for data that must be shared.

Virtru's data security products integrate effortlessly with the apps you already use every day, so your teams don't have to change anything about the way they work. Virtru combines military encryption standards with remarkable ease of use. From Microsoft 365 and Azure to Google Workspace, Virtru provides military grade encryption and granular access control for emails, files, and more.
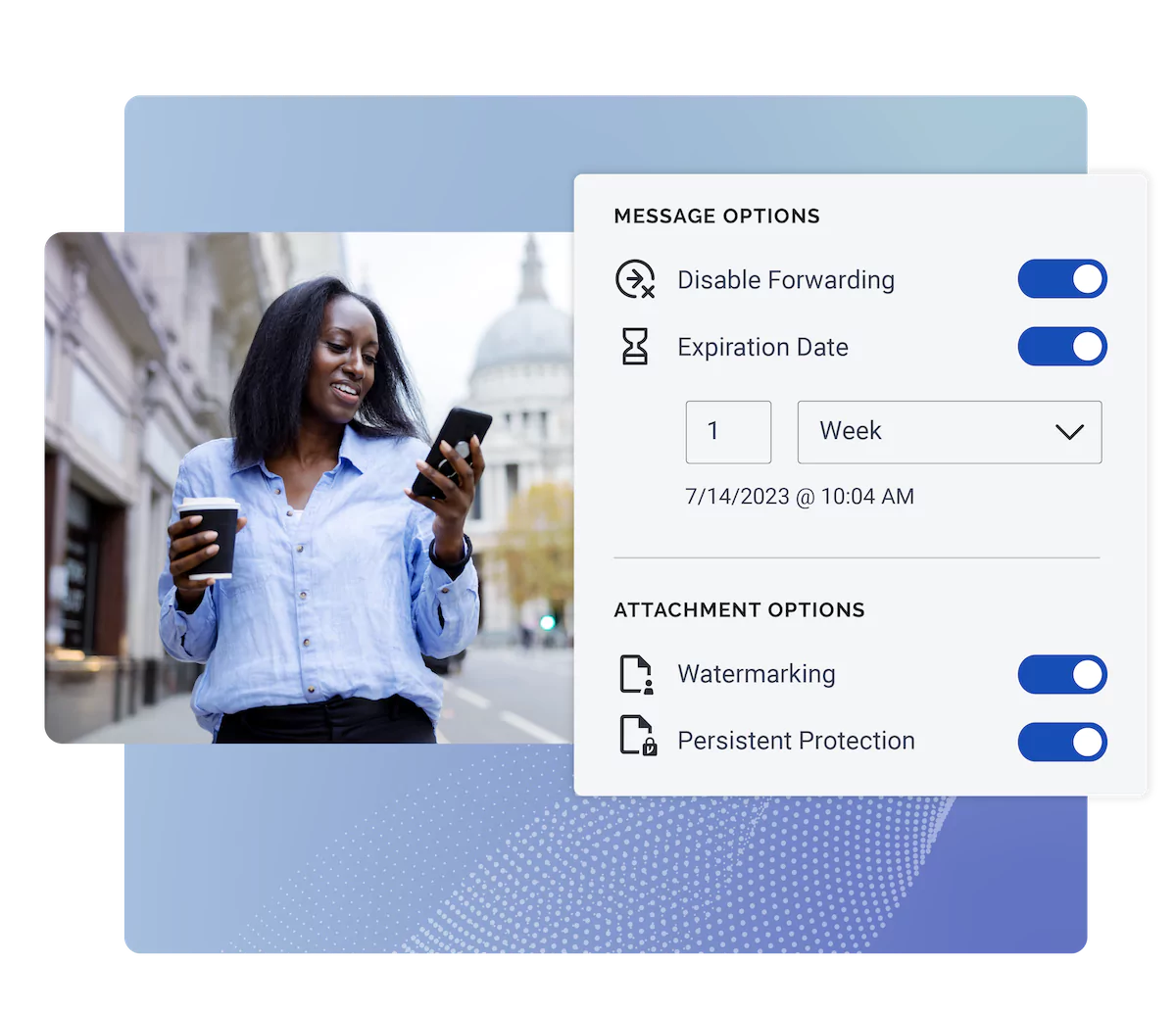
From CMMC to ITAR, CJIS to GLBA, Virtru encryption supports even the strictest compliance requirements without taking you out of the apps you use every day. This includes Microsoft apps like Outlook, Teams, SharePoint, and OneDrive — as well as Google Gmail, Google Drive, and Google CSE. With encryption US based, you also achieve data residency and support ITAR data location requirements.
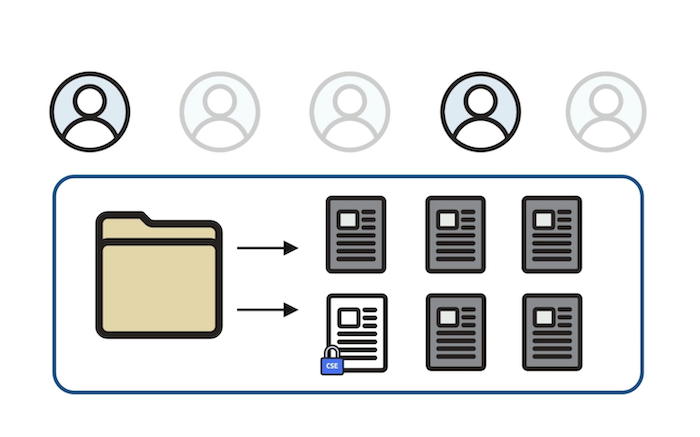
Virtru works seamlessly with data classification tools like Titus, Boldon James, Microsoft, and Google to apply labels and policies to data. This allows you to extend the value of your data tagging tools to safeguard the information your organization creates and shares.
Whether you’re sending an email, attachment, or large file, Virtru lets you securely collaborate internally and externally.
Apply attribute-based access controls to sensitive data flowing in and out of your organization. Change or revoke access to encrypted emails sent at any time. Keep encryption US based with the option to manage your own encryption keys.
Put automated data protection in place, and leverage your existing data labeling tools to apply enforceable labels to the data you manage.
When you can confidently and securely share information, big things happen: silos disappear, ideas flow, and innovation thrives. Extend the power of your data classification software to cover the full lifecycle of the data.
/resource%20-%20forge%20institute/forge%20logo.png)
"With Virtru, you can ensure that information sent is encrypted at all points, not just in transit. It's encrypted at rest in your recipient's inbox, and you also have visibility and control over that information. So you can worry less about what's happening with it once it leaves your organization."
Lee Watson
Chairman and CEO
Forge Institute
Read the Case Study


“Our transport is materially better than it was. Our costs are materially better. We have trust... And it was frictionless with Virtru. It was honestly above and beyond. This is operational excellence at its peak."
Karl Jankowski
Information Security and Privacy Manager
WealthForge
Read the Case Study

/Master-Electronics%20copy.webp)
"I remember the winning feature of Virtru, comparing it against everybody else: From the recipient side, there is no installation that needs to be done. There is no login that needs to be created."
Head of Information Security
Master Electronics
Read the Case Study
/resource%20-%20forge%20institute/forge%20logo.png)
"With Virtru, you can ensure that information sent is encrypted at all points, not just in transit. It's encrypted at rest in your recipient's inbox, and you also have visibility and control over that information. So you can worry less about what's happening with it once it leaves your organization."
Lee Watson
Chairman and CEO
Forge Institute
Read the Case Study


“Our transport is materially better than it was. Our costs are materially better. We have trust... And it was frictionless with Virtru. It was honestly above and beyond. This is operational excellence at its peak."
Karl Jankowski
Information Security and Privacy Manager
WealthForge
Read the Case Study

/Master-Electronics%20copy.webp)
"I remember the winning feature of Virtru, comparing it against everybody else: From the recipient side, there is no installation that needs to be done. There is no login that needs to be created."
Head of Information Security
Master Electronics
Read the Case Study