
Google Workspace Encryption and Data Privacy
Protect emails, files, and sensitive data in Google Workspace with Virtru.
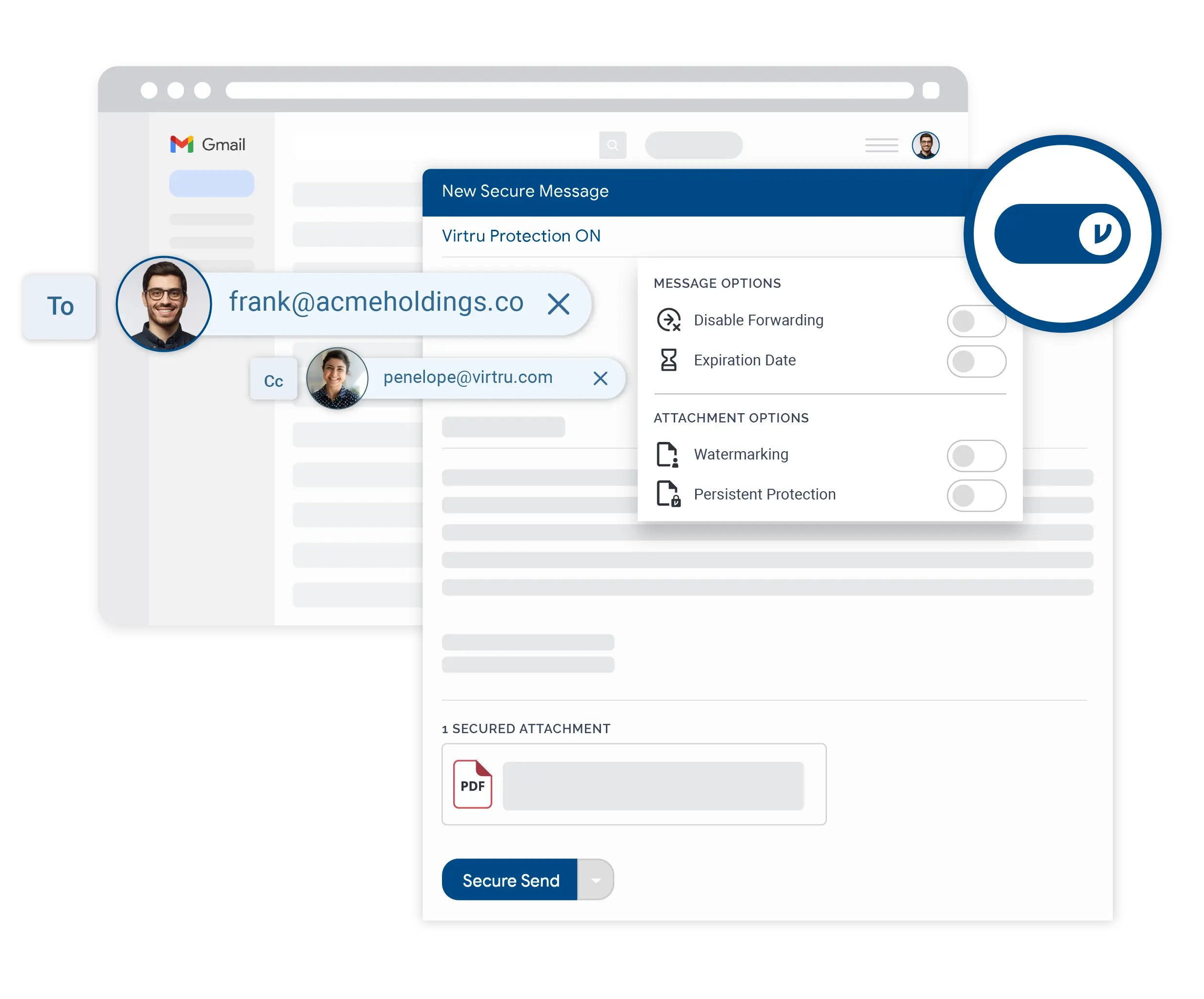

Protect emails, files, and sensitive data in Google Workspace with Virtru.

Your organization stores a lot of sensitive information in Google Workspace. Virtru helps you keep that sensitive data private and secure, across your Google ecosystem.
Virtru’s Gmail plugin is natively integrated within the Gmail interface, making it easy to protect sensitive data before it leaves your organization.
Explore Virtru for GmailProtect files stored in Google Drive upon upload — whether they’re Google files, Microsoft files, videos, PDFs, CAD files, or other formats.
Explore Virtru Encryption for Google DriveKeep your meetings confidential: Encrypt Google Meet calls and video messages to prevent third-party access.
Learn More About Virtru for Google Client-Side EncryptionProtect teams’ plans, ideas, and strategic content created and shared in Google Docs.
Learn More About Virtru for Google Client-Side EncryptionSecure financial reports, budgets, and other sensitive data stored and shared in spreadsheets using Google Sheets.
Learn More About Virtru for Google Client-Side EncryptionSecure important board presentations, client demos, and more with Virtru data protection for Google Slides.
Learn More About Virtru for Google Client-Side EncryptionHost your own encryption keys separately from Google with Virtru Private Keystore, shielding your data from Google, Virtru, and other third parties.
Control Your Encryption Keys with Virtru Private Keystore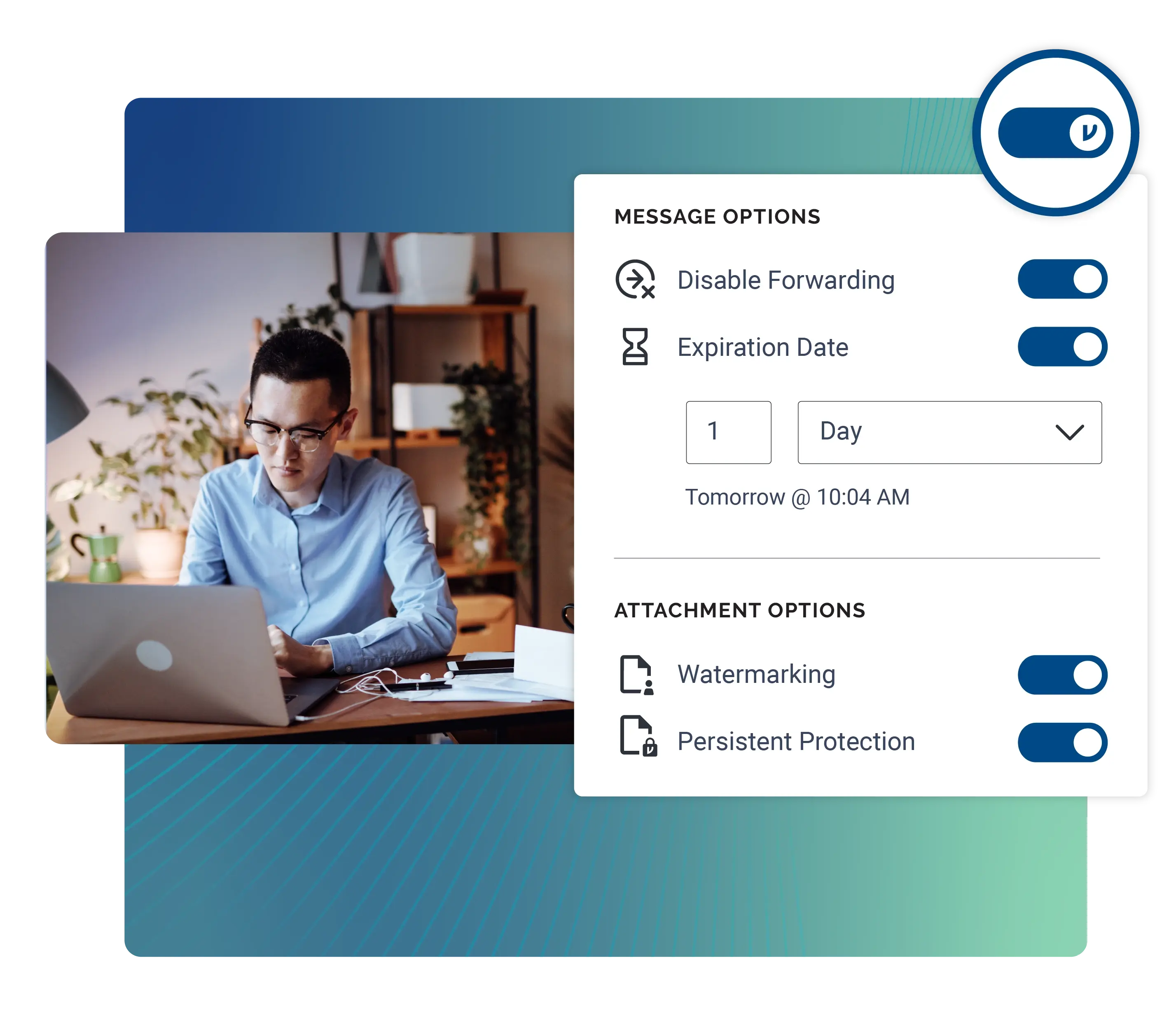
Protect your data in Google Workspace to help maintain compliance, no matter where it is shared or who has been granted access. Granular security controls allow Gmail, Google Drive, and Google Workspace users and admins to:
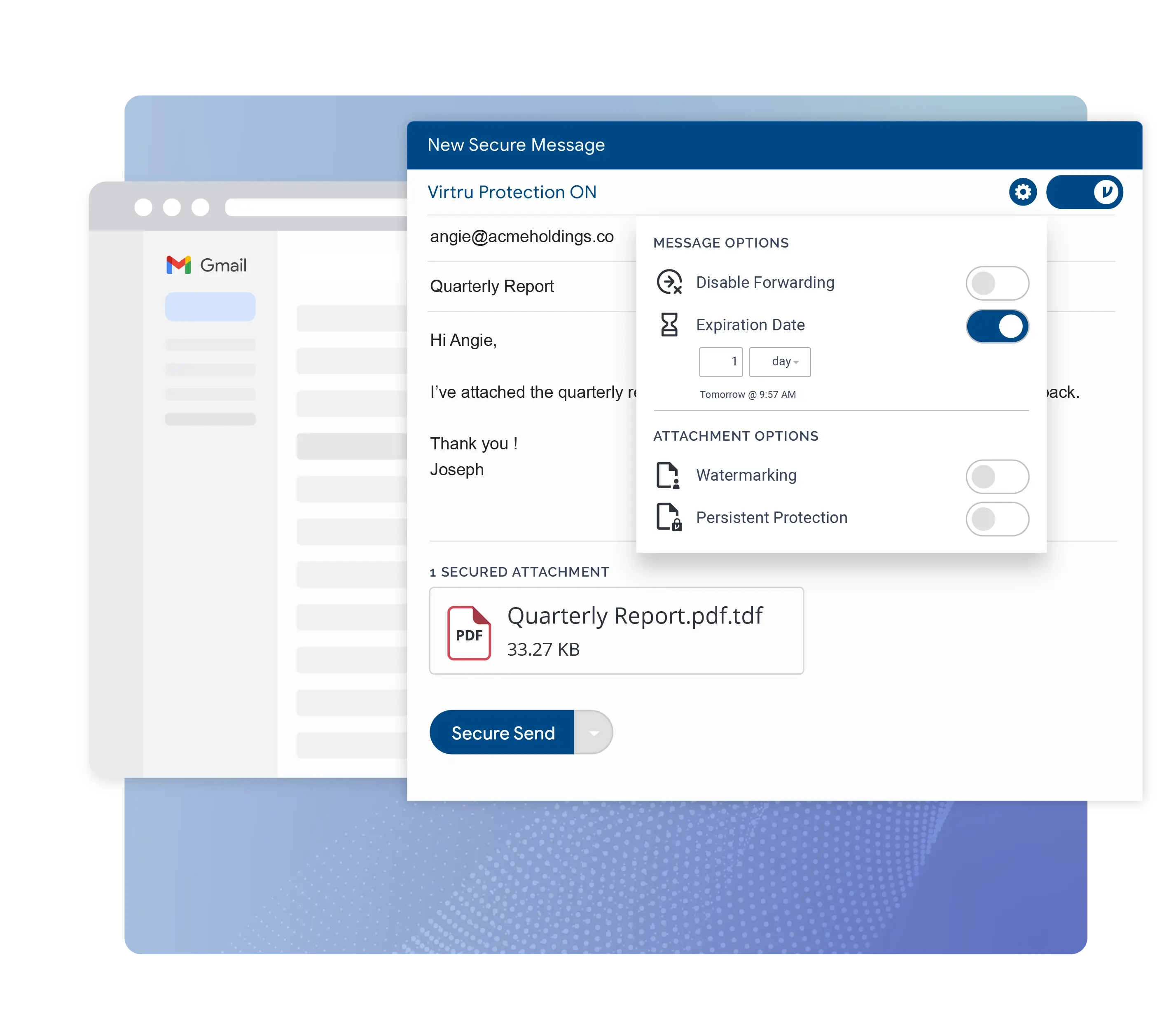
One-click, end-to-end encryption and decryption with no portal logins.

Easily collaborate with anyone, whether they’re inside or outside your organization. Our industry-leading recipient experience means recipients can access data easily:
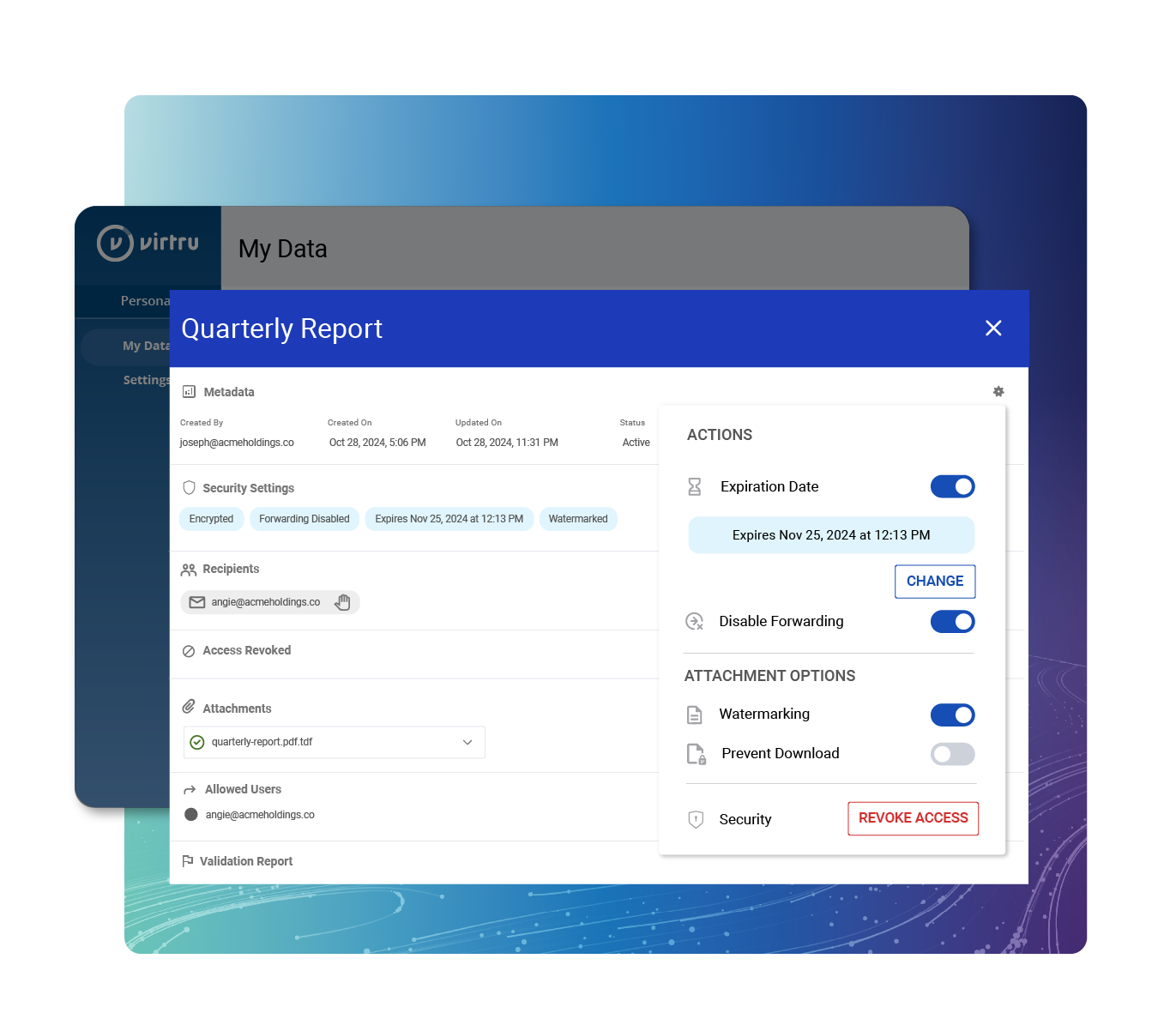
Virtru gives you centralized insights to make informed business decisions.
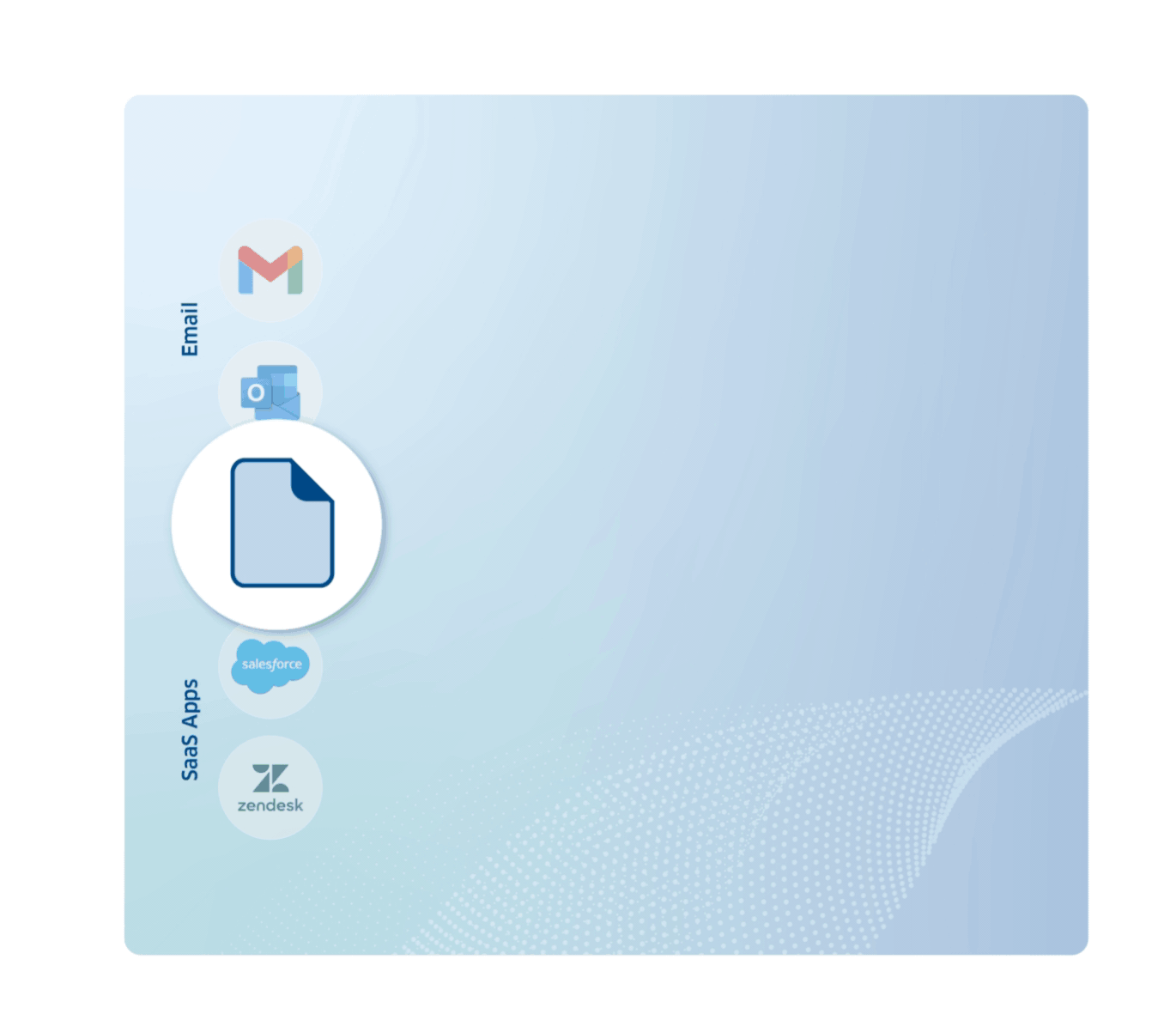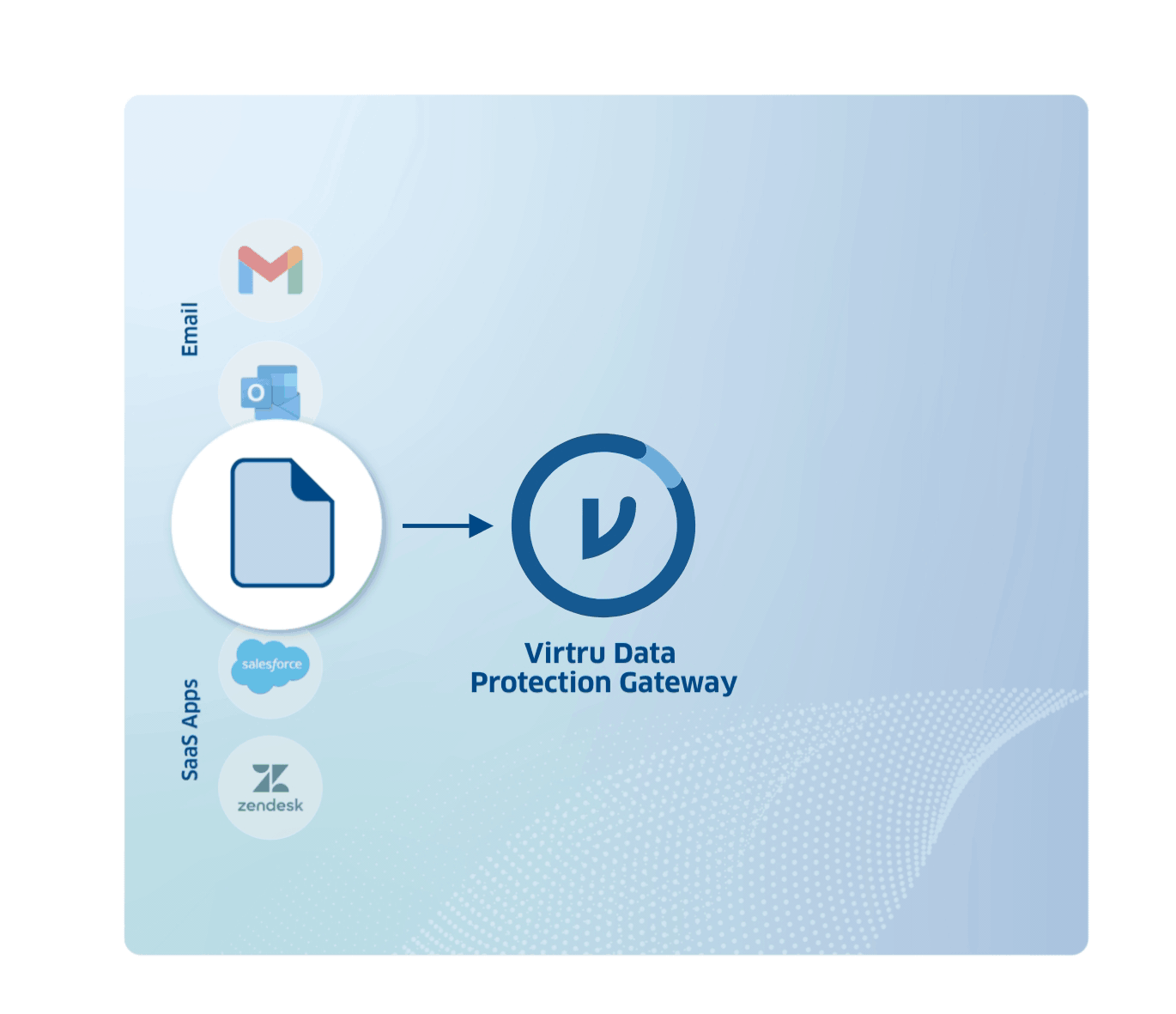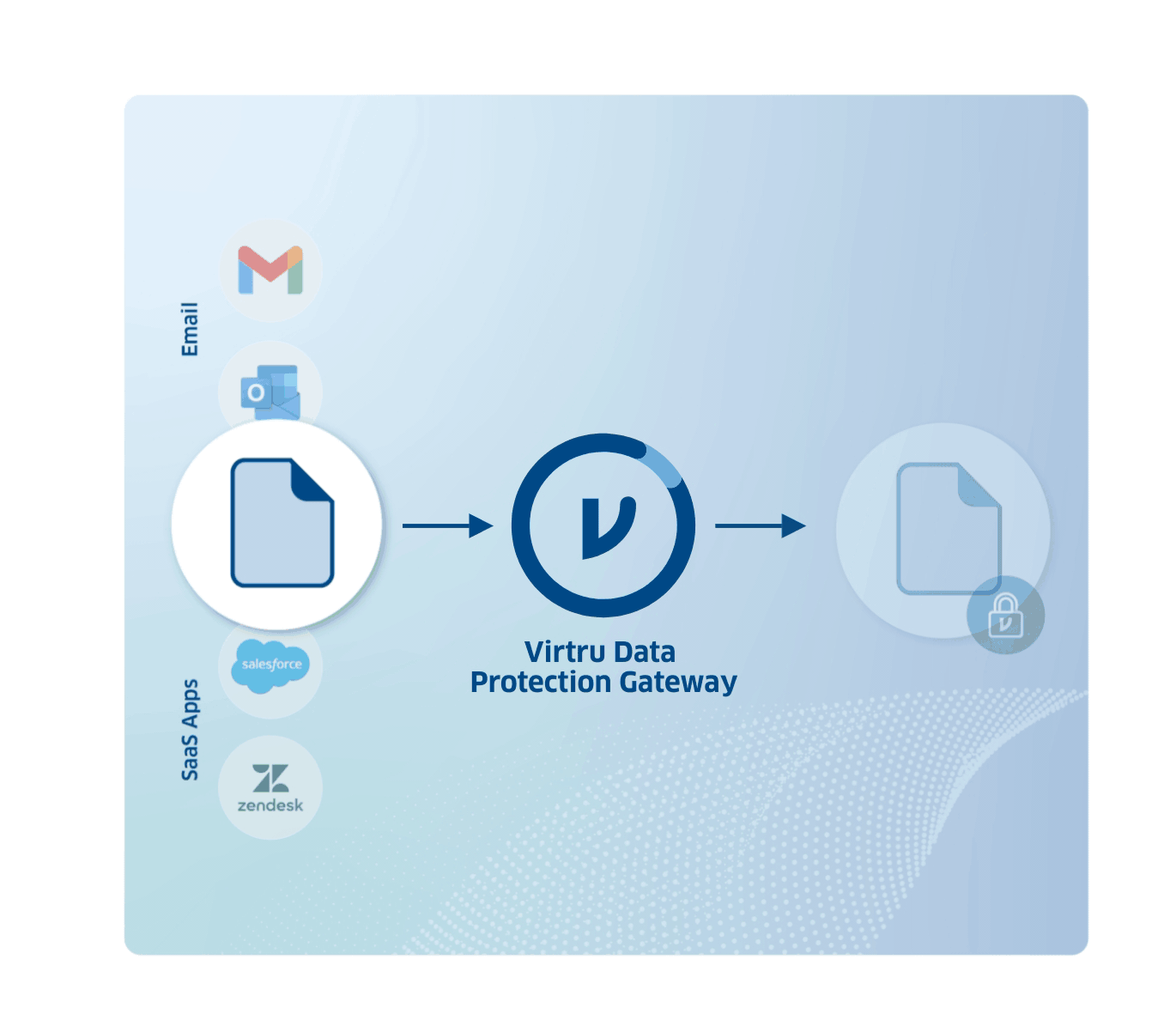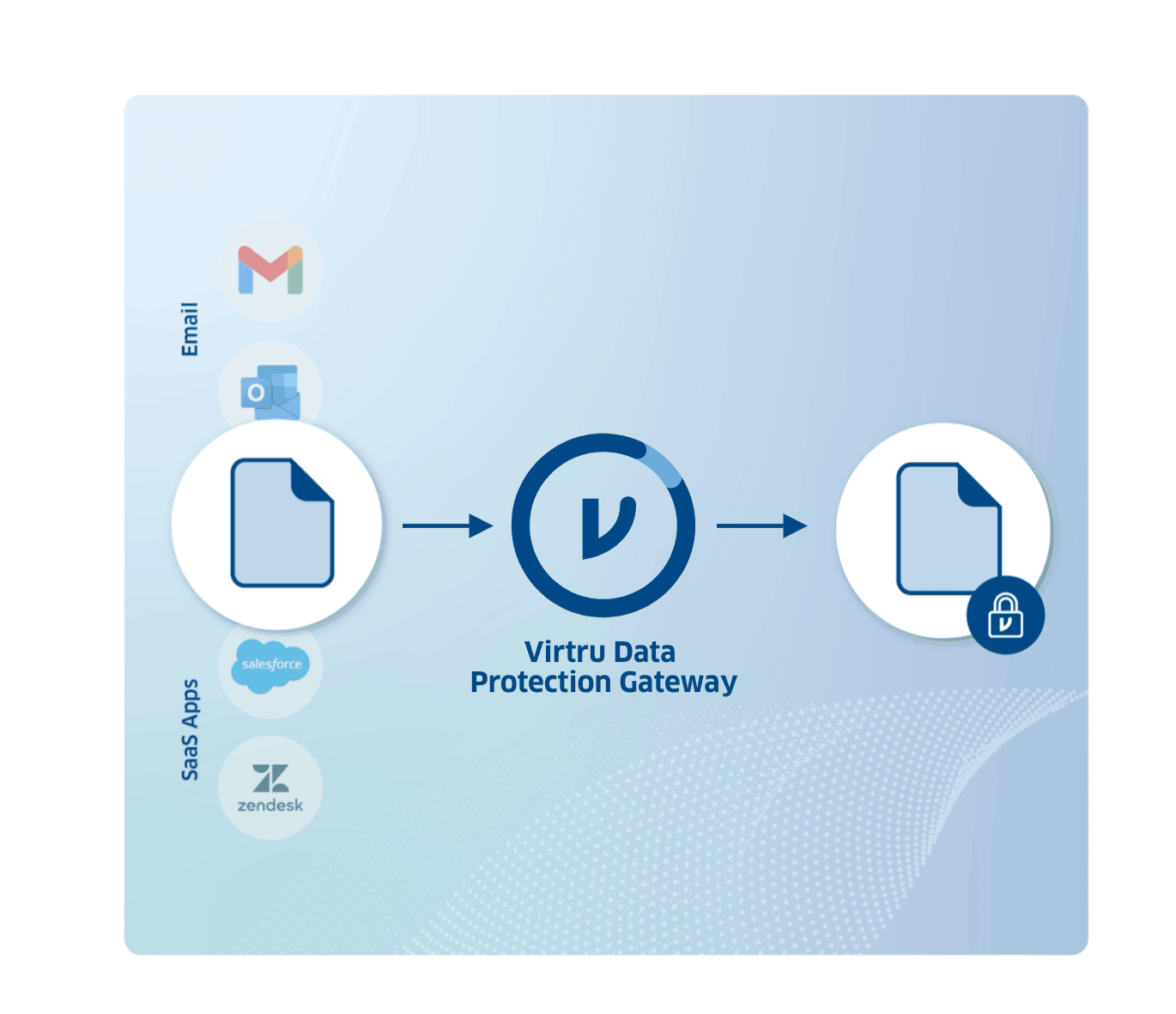
Humans are, well, human. Protect sensitive data against human error with the Virtru Data Protection Gateway.
Protect your data in Google Workspace to help maintain compliance, no matter where it is shared or who has been granted access. Granular security controls allow Gmail, Google Drive, and Google Workspace users and admins to:

One-click, end-to-end encryption and decryption with no portal logins.

Easily collaborate with anyone, whether they’re inside or outside your organization. Our industry-leading recipient experience means recipients can access data easily:

Virtru gives you centralized insights to make informed business decisions.

Humans are, well, human. Protect sensitive data against human error with the Virtru Data Protection Gateway.

/Partner%20of%20the%20Year%20Google.webp)
Virtru was named a 2024 Google Cloud Partner of the Year in Industry Solutions - Technology for Government and Education.
Add a layer of data-centric security and control with Virtru’s data protection for Google Workspace.
Easy-to-use encryption helps you meet data security requirements without the complexity or cost associated with legacy solutions.

CASE STUDY
Exxelia Secures Intellectual Property According to ITAR & CMMC 2.0 Standards with Virtru
Read the Case Study
Easy organization-wide installation means users are up and running within minutes, with the option for more dedicated support if needed.

CASE STUDY
NEXT Insurance Gains Speed and Security with Virtru
Read the Case Study
Take control of your encryption keys and policies to maintain ownership of your data and govern access.

CASE STUDY
HR Tech Innovator Maki Uses Virtru Private Keystore for Advanced Google Cloud Security
Read the Case Study


“AFRL invests in its collaboration tool stack by using the Google Workspace suite to foster that simple, easy-to-use collaboration, along with Virtru’s client-side and server-side data protection to provide additional layers of security for sensitive information.”
Dr. Dan Berrigan
Lead, Collaborative Tools, Air Force Research Laboratory Digital War Room

It's your data. Let's keep it that way. Take complete ownership of your encrypted cloud data. Host your private keys wherever you like. Let Virtru do the rest, from high volume key exchanges to policy management.
Virtru Private Keystore
Virtru's server-side data protection can be configured to meet the needs of your organization, adding a valuable safety net to automatically encrypt data moving through email and SaaS apps.
Virtru Data Protection Gateway
Need a secure way to exchange large files with customers or partners? Virtru Secure Share makes it simple: It works in your browser, integrates with your favorite apps, and puts full control in the hands of the data owner.
Virtru Secure ShareGet expert insights on how to address your data protection challenges.
6,100 CUSTOMERS TRUST VIRTRU FOR DATA SECURITY AND PRIVACY PROTECTION.




Contact us to learn more about our partnership opportunities.