Accelerate Outcomes Through Precise Data Access Controls
Control access to your most sensitive information by enforcing policy at the intersection of attributes on data and entitlements on identities.

Share data and drive value without sacrificing security, privacy, or control

In the face of today's advanced cyber threats, organizations must operate with the mindset that network perimeters are already compromised. To succeed in this new reality, security leaders must prioritize granular controls and architectures centered on the data itself rather than perimeter-based defenses alone.

Share Data Securely
Persistent protection travels with data as it's shared inside and outside your perimeter, promoting collaboration while maintaining privacy, governance, and control.

Enforce Granular Policies
Protect sensitive data that has been shared with others, inside and outside your organization.

Embrace Open Standards
No vendor lock-in: Virtru’s platform leverages the world’s leading open, secure data standard — the Trusted Data Format (TDF).
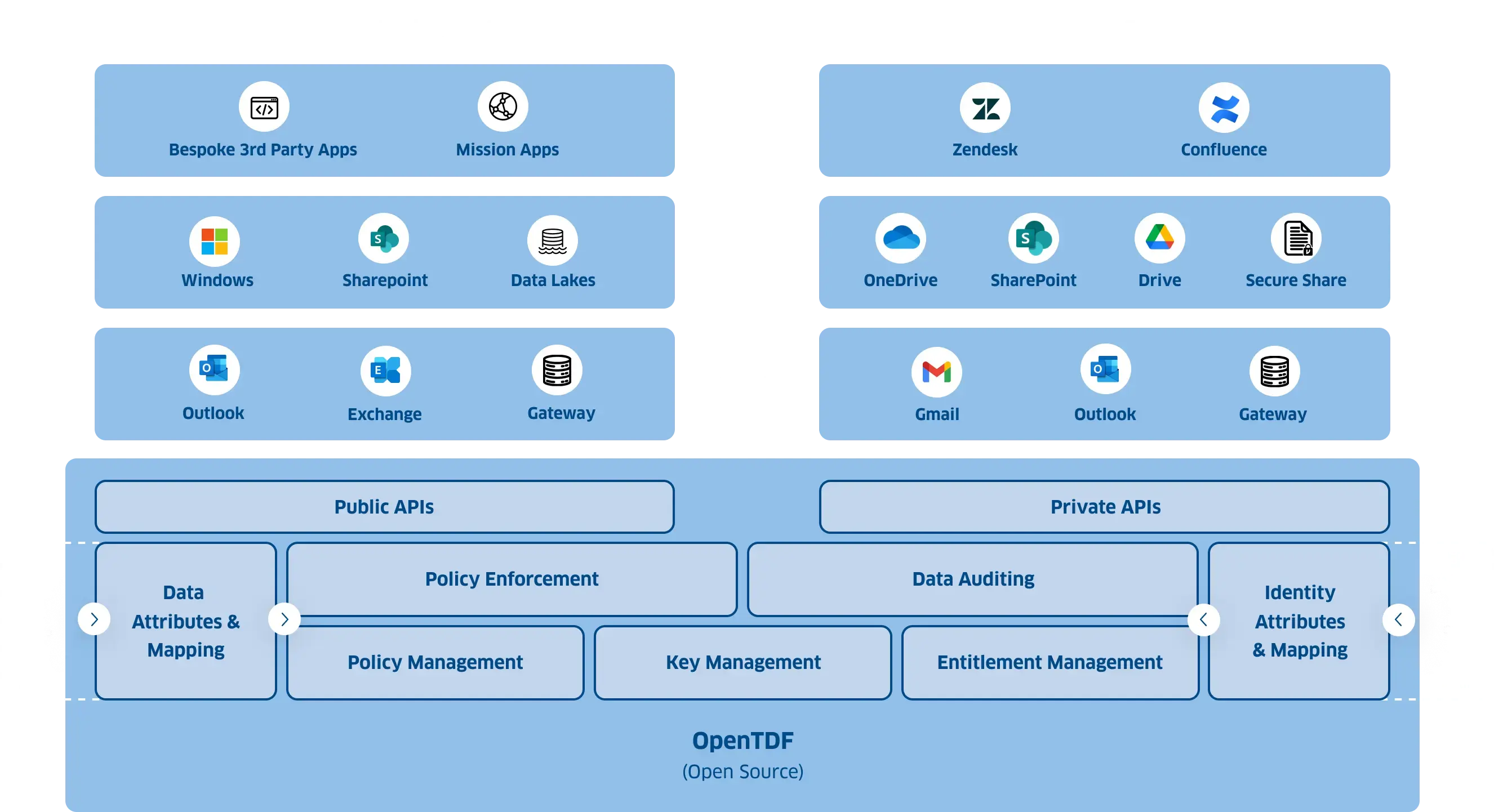
The Virtru Data Security Platform provides a comprehensive and adaptable foundation for data-centric security. Built on the open TDF standard, our platform enables your organization to protect sensitive data shared with others.
Dynamically enforce policies at the intersection of attributes on data and identities.
/DSP-Transform.webp)
Bespoke 3rd Party Apps
Mission Apps
Zendesk
Confluence
Windows
SharePoint
Data Lakes
OneDrive
SharePoint
Drive
Secure Share
Outlook
Exchange
Gateway
Gmail
Outlook
Gateway
Titus
Cyera
Rubrik
Active
Directory
Okta
Ping
Identity
OpenTDF
(Open Source)
Click each box to learn more
Suite of SDKs available to developers to extend data-centric security controls into bespoke applications
Reserved endpoints used by Virtru only
Normalize attributes and metadata from external resources
Dynamically enforce granular access control policies
Provides comprehensive visibility into data access and usage
Normalize identity metadata from external resources
Define and manage granular access control policies
Control access to encryption keys using ABAC (Attribute Based Access Control)
Configure and manage connections to external ldPs, and define policy around identity
Virtru’s solutions seamlessly integrate with your everyday applications — such as email clients, cloud-based enterprise applications, customer support platforms, data lakes, and more. The best part: The Zero Trust security capabilities of the Data Security Platform will be virtually invisible to your team, so they can focus on getting their jobs done.
Native Integration With Your Everyday Apps
Virtru Data Protection Gateway
Virtru for Gmail
Virtru for Google Drive
Virtru for Microsoft Outlook
Virtru for Microsoft Sharepoint
Virtru Secure Share
Virtru Secure Share for Google Drive
Virtru Secure Share for OneDrive
Virtru Secure Share for SharePoint
Virtru Secure Share for Zendesk
Virtru Secure Share for Confluence
Granular policy and persistent security are essential for sharing data in a perimeter-less world.
Protect your data everywhere; even after it's been shared with others.
Safely collaborate with external partners while controlling who accesses your data and for how long.
Infuse granular policy and data-centric security into your favorite apps and existing workflows.
Strengthen Regulatory Compliance
Adhering to regulatory compliance standards is a top priority for many organizations. Virtru Data Security Platform helps you meet regulatory obligations, ensure data remains secure, and safeguard your organization's data collaborative position.
Control access to your most sensitive information by enforcing policy at the intersection of attributes on data and entitlements on identities.
/Platform-Page-Images_DSP%201.webp)
Leverage ABAC's granular access control superpowers to grant or restrict access to information based on data and entity attributes, such as roles, departments, classifiers, etc.
/Platform-Page-Images_DSP%202.webp)
ABAC dynamically adapts to evolving circumstances, ensuring authorized users can access the data they need or have access instantly revoked when situations change. This enhances your organization's security posture while maintaining mission velocity.
/Platform-Page-Images_DSP%203.webp)
Take advantage of attributes from your existing data classification and tagging tools, as well as your identity and access management (IAM) provider.
We offer two deployment options for the Virtru Data Security Platform:
The Data Security Platform's self-managed deployment option offers the most comprehensive set of data-centric security capabilities available. In addition to our suite of optional policy enforcement points, a rich set of developer resources is uniquely available, enabling you to extend granular ABAC-based policy control into bespoke mission applications.
Let us do the work. Our fully managed cloud platform offers a convenient and efficient solution for quickly protecting your data workflows. The SaaS platform offers easy accessibility, scalability, and integration with the applications your team uses every day.
Learn More: SaaS Deployment Option

Virtru's platform offers a robust developer experience, simplifying the process of extending attribute-based access control into legacy off-the-shelf applications or bespoke mission applications.
Virtru Developer Experience/Copy%20of%20DSP-TDF.webp)
The Virtru Data Security Platform extends the capabilities of the open-source OpenTDF project, making it easier to set up, administer, and enforce data-centric policies across your enterprise.
The Trusted Data Format – TDF – is the metadata standard leveraged by the Data Security Platform and is the data-centric security standard trusted by numerous organizations, including the U.S. Intelligence Community, the world’s largest financial institutions, and nearly 7,000 other commercial and public-sector organizations.
TDF is quickly becoming recognized as the Zero Trust data standard.
Trusted Data Format6,100 CUSTOMERS TRUST VIRTRU FOR DATA SECURITY AND PRIVACY PROTECTION.




Contact us to learn more about our partnership opportunities.