Data Protection Built for CCPA Security Standards
Virtru's versatile data security solutions integrate with the apps you use every day for heightened data control and governance for CCPA alignment.
Prevent unauthorized access to consumer data wherever it’s shared with data-centric protection and powerful key management capabilities that meet security and control obligations under CCPA.
/Dealership%20Email%20FTC%20Safeguards.webp)
Implementing and maintaining the “reasonable security procedures and protections” required for compliance with the California Consumer Privacy Act (CCPA) boils down to protecting California residents’ private data from unauthorized access. Virtru provides an easy way to govern data access for stronger consumer privacy.

Virtru integrates seamlessly with your everyday apps like Gmail, Outlook, Google Drive, Zendesk, and more. End-to-end encryption and granular access controls protect consumer data as it’s collected, processed, and shared throughout its lifecycle.
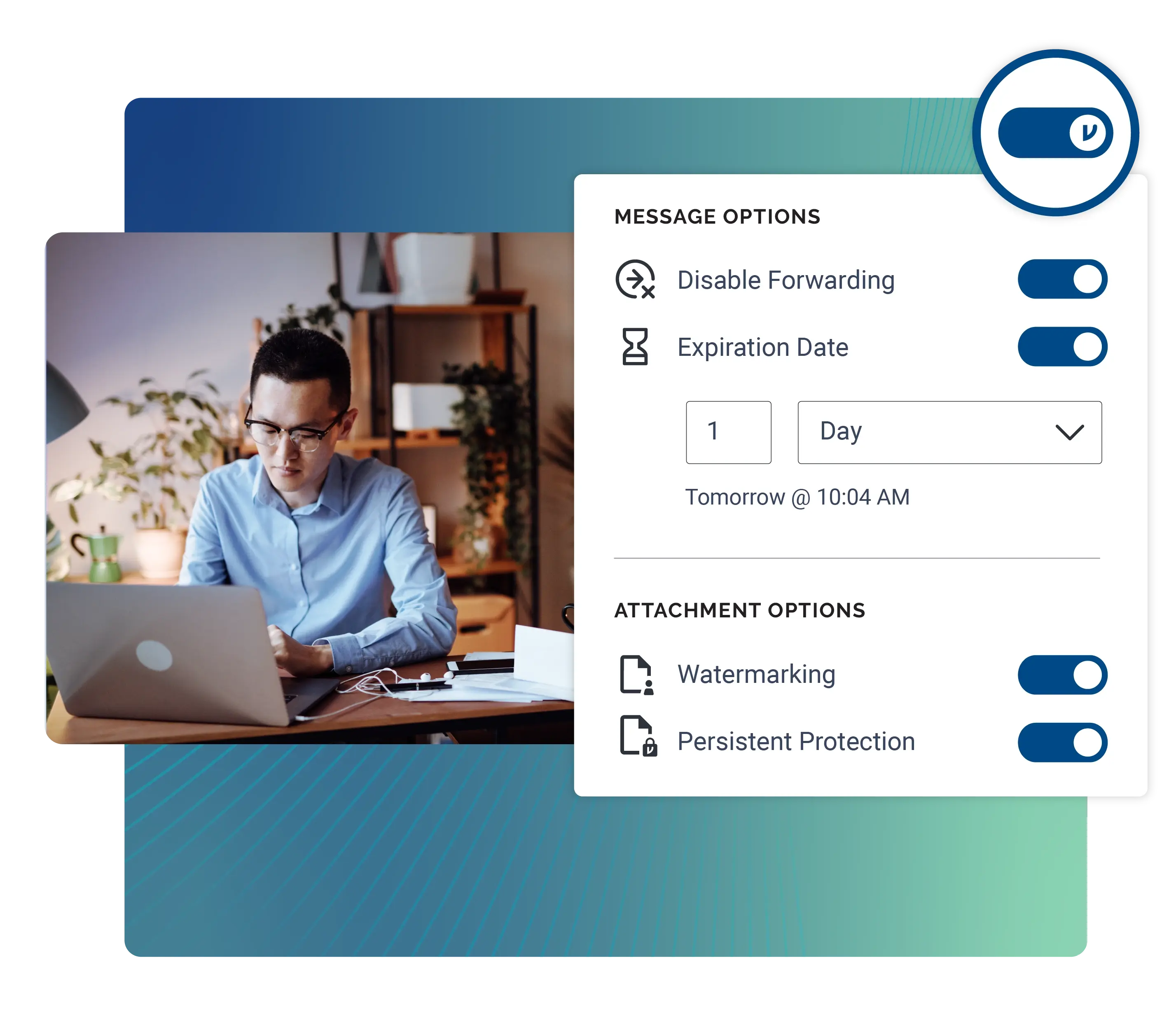
Prevent unauthorized access to Californians' personal information with end-to-end encryption, granular access controls, and customer-hosted keys that help ensure consumer data privacy.





“We want the customers to feel safe. So, it doesn't matter if the product ends up on a supermarket shelf or in a highly classified environment. It's very important for us that we're giving them a professional way to share data, and we're not just attaching it to an email.”
CTO
AI Startup, Virtru Customer
Virtru's versatile data security solutions integrate with the apps you use every day for heightened data control and governance for CCPA alignment.

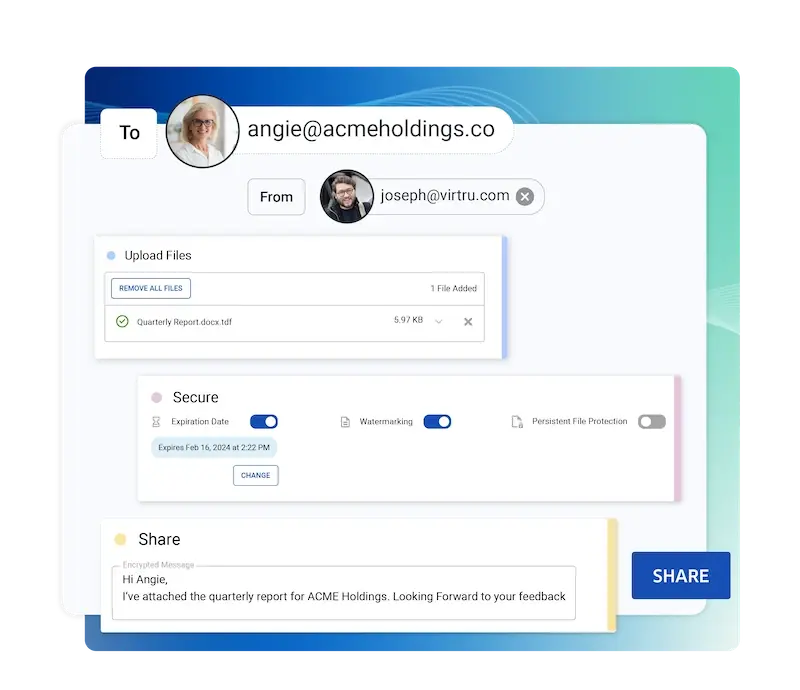
Encrypt Gmail and Outlook messages and Google Drive files directly within the client to keep consumer data protected from unauthorized access. Fulfill DSAR workflows securely using encrypted email and encrypted file-sharing solutions that work in any browser.

Disable forwarding, set expiration, and revoke access immediately. Watermark files to deter consumer data leaks. Apply persistent protection to maintain control wherever private files are shared, while giving collaborators seamless, secure access through the Secure Reader.

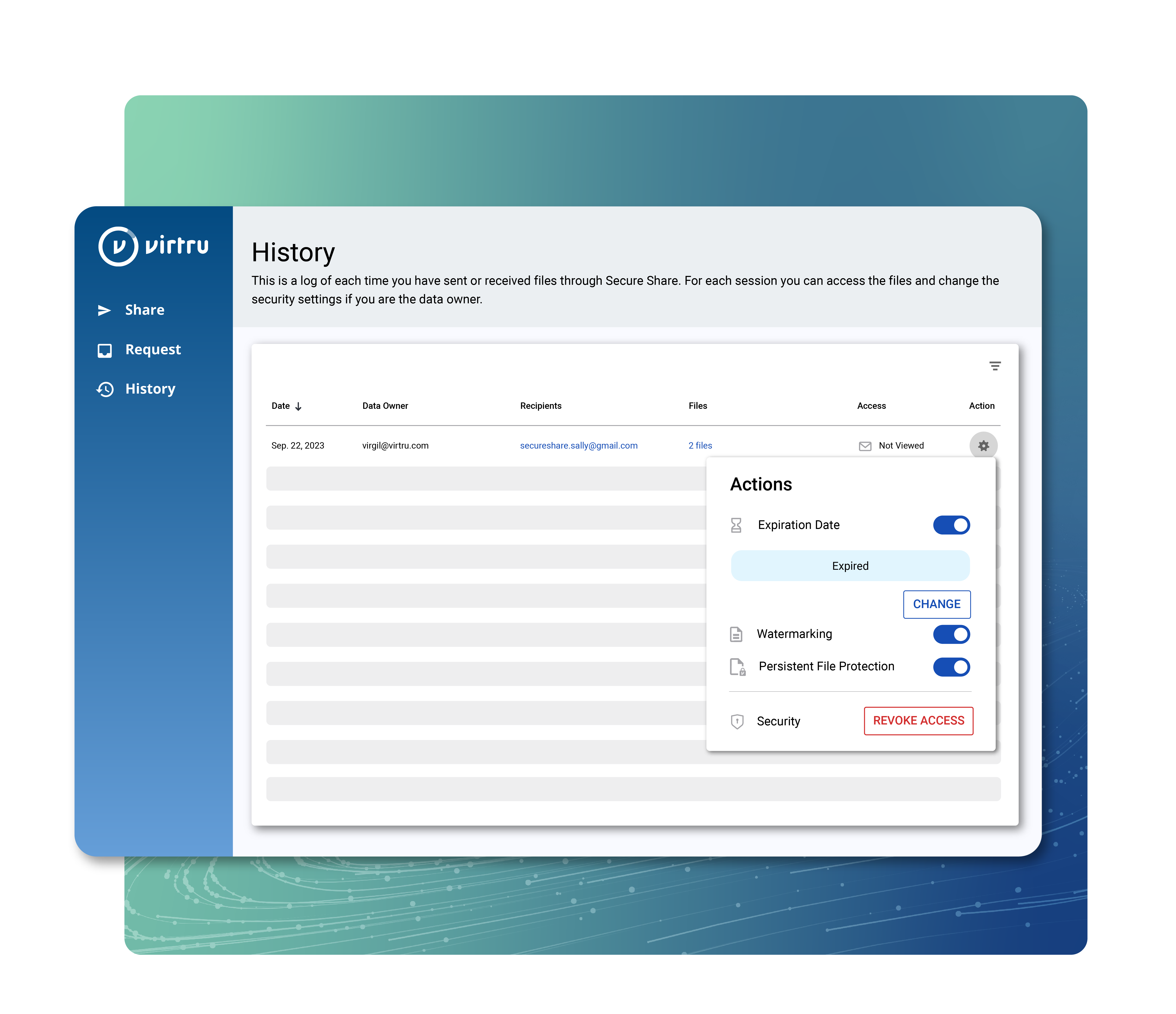
View when and where email messages, attachments, and files containing consumer data have been accessed during their lifecycle with the Virtru Control Center. Adapt controls as access requirements evolve throughout private consumer data sharing workflows.
/Training%20Portal%20Virtru.webp)
Configure DLP rules that scan emails and attachments to detect private consumer data, then automatically enforce encryption and access controls that persist throughout collaboration workflows to help maintain CCPA compliance.
Open data protection standard for object-level encryption that binds data to policies and metadata to ensure only authorized users can access private data.
With Virtru Private Keystore, host your encryption keys in the location of your choice, whether on-prem, in a private or public cloud, or with Virtru. This provides stronger control and separation between content and keys.
Virtru leverages attribute-based access control to ensure that sensitive information can only be accessed by the right individuals or systems, at the right time. The Virtru Data Security platform is FedRAMP-authorized, FIPS 140-2 validated, and supports many heightened compliance requirements.
6,100 CUSTOMERS TRUST VIRTRU FOR DATA SECURITY AND PRIVACY PROTECTION.



Contact us to learn more about our partnership opportunities.