Mission-Critical Data Security for Federal Government Organizations
Virtru's Data Security Platform enables secure, compliant data sharing to unlock digital workflows and protect your most sensitive data — in military and civilian contexts.
Strengthen Your Zero Trust Posture with the Virtru Data Security Platform
With end-to-end encryption and fine-grained access control, you can govern and share sensitive data with coalition partners and fellow federal agencies.








/Virtru%20NATO%20OTAN.webp)
Virtru for NATO and NCI Agency
Virtru has partnered with the NATO Support and Procurement Agency (NSPA) and the NATO Communications and Information (NCI) Agency to provide technological, cyber defense solutions for NATO member states.
With Virtru, our agencies, coalition partners, and combatant commands can securely and rapidly share time-sensitive, mission critical information.
Learn More/Blog%20-%20ZTDF%20The%20Quiet%20Revolution/zero-trust-data-format.webp)
/Leadership%20page/MC2%20Security%20Fund.png)
"Given growing market demand for Zero Trust Data Access (ZTDA) solutions and the clear opportunity for Virtru within the government market, we see great things on the horizon for Virtru. We are thrilled to partner with them on this journey and look forward to seeing what Virtru will deliver next to protect our nation and its data."
Michael Chertoff
Secretary of the U.S. Department of Homeland Security ('05-'09), Co-Founder and Executive Chairman of MC2 and The Chertoff Group
Federal Compliance Certifications
/FedRAMP%20Card.webp)
FedRAMP
Virtru has a certified Authorization to Operate (ATO) at the moderate level under FedRAMP. As part of our FedRAMP compliance program, we adhere to the security controls defined in the NIST 800-53 and 800-171 publications to ensure the integrity of federal information systems.
/SOC%202%20Card.webp)
SOC 2 - Type 2
Virtru’s security operations and processes are validated by third-party assessments for Service Organizations Control (SOC) 2 Type 2 Compliance. This attests that we can be trusted to safeguard sensitive customer data in the cloud.
/FIPS%20card.webp)
FIPS 140-2
Virtru solutions are FIPS 140-2 Validated. For a cryptographic module to be FIPS validated, it must undergo an independent examination by NIST-accredited lab. Validated modules are issued certificates, which can be viewed on the Cryptographic Modules Validation Program (CMVP) website.
Unlock Secure Collaboration
With Virtru, agencies can securely collaborate, protecting CUI and sensitive information with end-to-end encryption and persistent access control, everywhere it's shared.
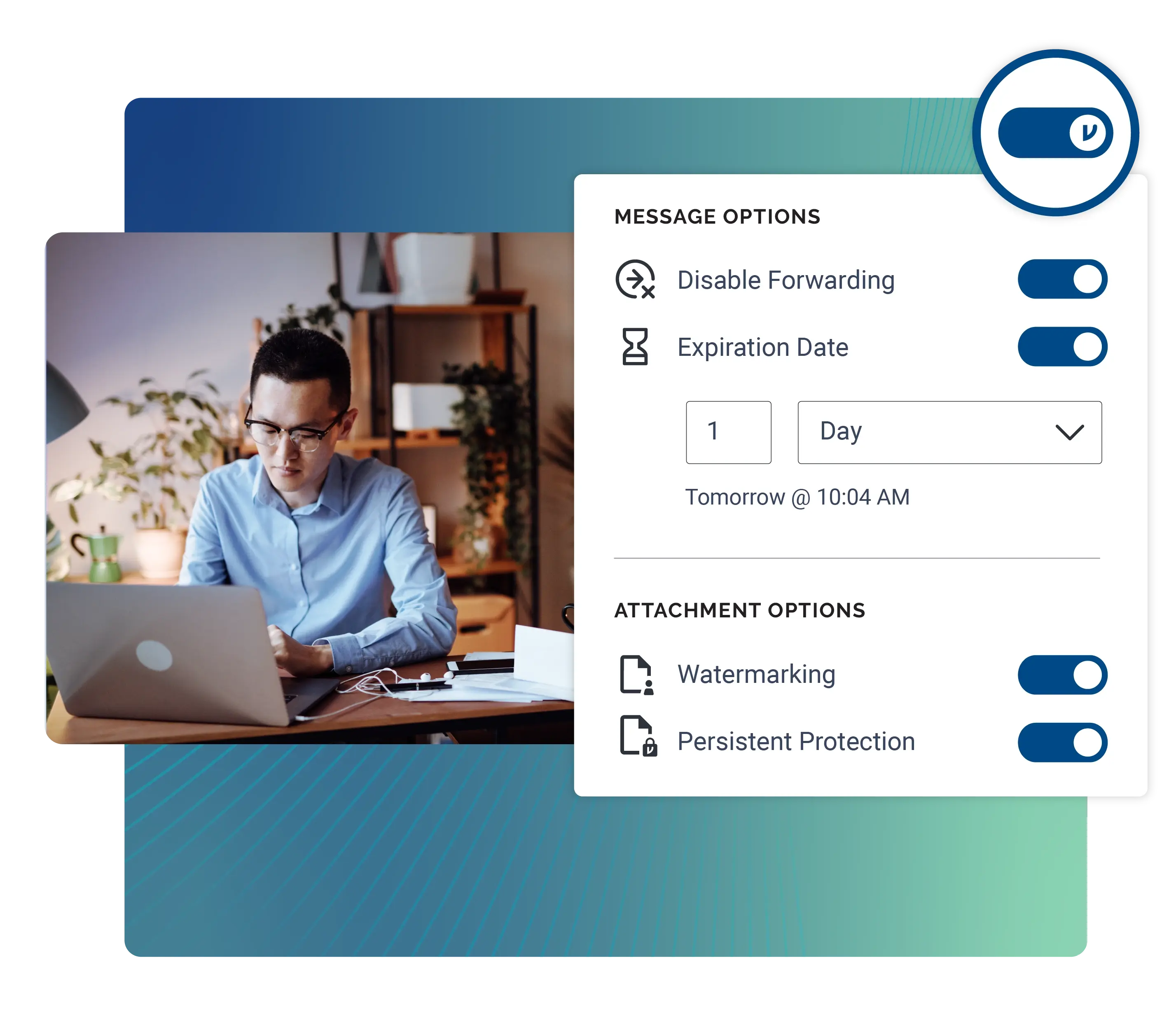
Advance Office Productivity
With our government email encryption and file protection solutions, federal agencies can equip their distributed teams to collaborate with confidence. With the ability to revoke access at any time, set expiration dates, watermark attachments, and disable forwarding, Virtru gives end users autonomy, security, and control over their data, everywhere it’s shared. Layer in Data Loss Prevention (DLP) rules as a safety net, plus encryption for SaaS applications such as SAP, for data protection across all workflows.
Learn More
Fine-Grained Control of Edge Data
Whether relaying data from sensors in remote locations or embedded in medical equipment, Virtru’s Trusted Data Format (TDF) is flexible and versatile, protecting data on small devices and in low-bandwidth areas. With TDF, agencies can protect full-motion video, biometric data, and more.
Learn More
Govern Data Sharing with Coalition Partners
For federal agencies, it’s critical to ensure sensitive data doesn’t fall into the wrong hands, and that it is only accessed by those with a need to know. Because many organizations have numerous levels of access rights, as well as numerous channels and products by which data is disseminated, data tagging and access management have become extremely complex. Powered by the Trusted Data Format (TDF), the Virtru Data Security Platform simplifies secure data-sharing, automates encryption and access control, and streamlines federal data sharing workflows.
Learn MoreEnable Secure Analytics
Break down data silos and equip mission and business owners to share data securely with external collaborators to unlock greater insights. In the same way that Virtru enables data owners to maintain full lifecycle control over their sensitive information and securely share it for approved analysis, we also empower analytic owners not only to maintain control of the analytic, but also to have a say in how the outputs of analysis are managed and tracked, adding a level of transparency and trust that offers the potential for faster outcomes while ensuring compliance with a wide array of security and privacy requirements, including those derived from FISMA, HIPAA, CJIS, ITAR, and others.
Learn MoreVirtru Data Security Platform Architecture
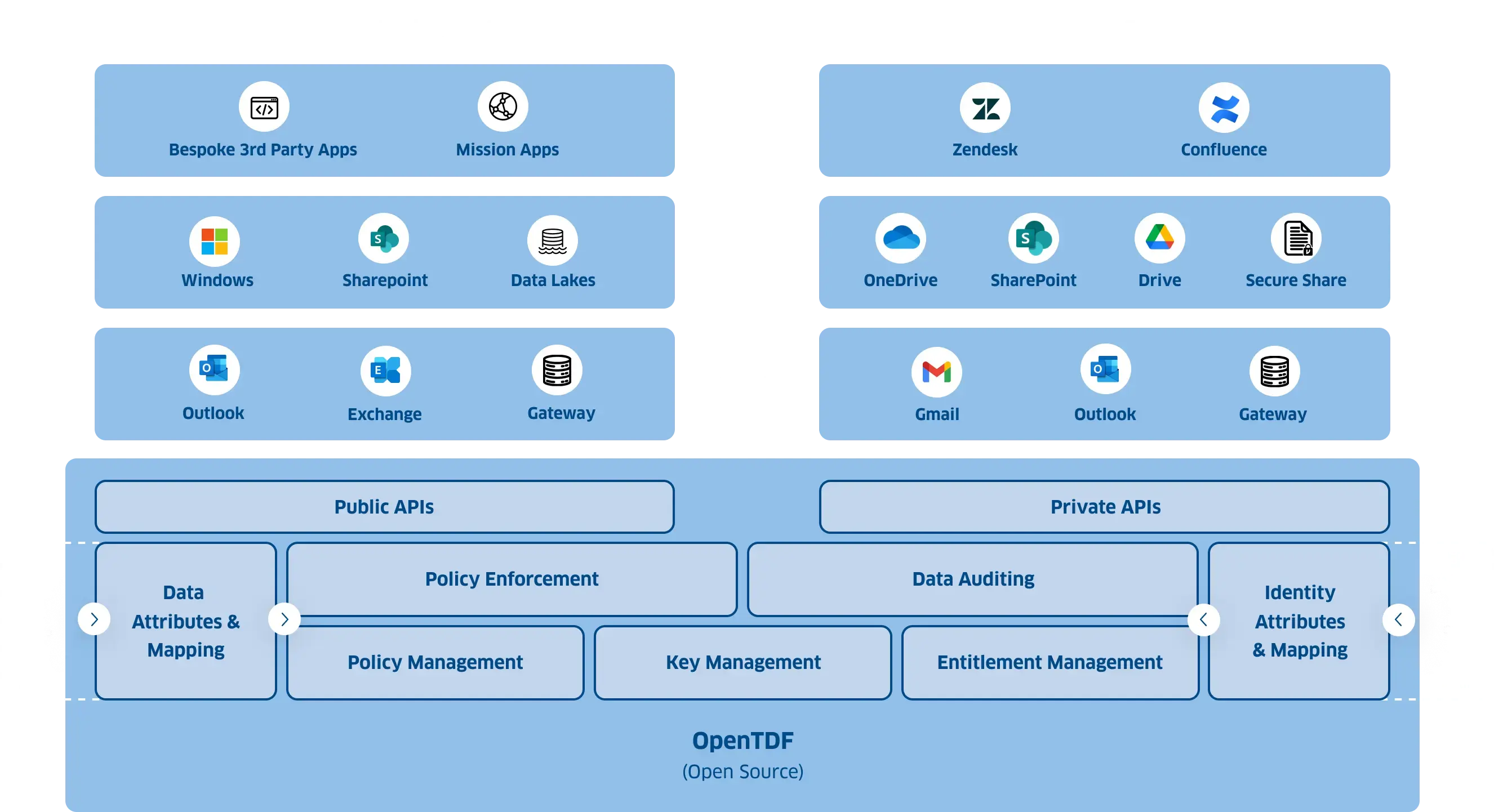
On-Premises / Virtual Private Cloud
SaaS
Bespoke 3rd Party Apps
Mission Apps
Apps
Zendesk
Confluence
Windows
Sharepoint
Data Lakes
Files
Drive
Secure Share
Outlook
Gateway
Gmail
Outlook
Gateway
Titus
Cyera
Rubrik
Active
Directory
Okta
Ping
Identity
OpenTDF
(Open Source)
Click each box to learn more
Public API
Suite of SDKs available to developers to extend data-centric security controls into bespoke applications
Private API
Reserved endpoints used by Virtru only
Data Attributes & Mapping
Normalize attributes and metadata from external resources
Policy Enforcement
Dynamically enforce granular access control policies
Data Auditing
Provides comprehensive visibility into data access and usage
Identity Attributes & Mapping
Normalize identity metadata from external resources
Policy Management
Define and manage granular access control policies
Key Management
Control access to encryption keys using ABAC (Attribute Based Access Control)
Entitlements Management
Configure and manage connections to external ldPs, and define policy around identity
Virtru Federal Government Procurement Contracts
Virtru's federal government contracting vehicles are managed in partnership with Carahsoft. You can view the full list on Carahsoft.com.
Government Data Security Resources
Get expert insights on how to address your data protection challenges and implement a Zero Trust architecture.
Take the next step with Virtru.
6,700+ CUSTOMERS TRUST VIRTRU FOR DATA SECURITY AND PRIVACY PROTECTION.





/blog%20-%20versatile%20TDF/Versatile%20TDF%20Blog.webp)
