CJIS Compliant Data Workflows
With Virtru, you can keep CJI protected and controlled, without sacrificing the ability to collaborate.
Encrypt and control criminal justice information (CJI) stored and shared via Google Workspace and Microsoft 365 for CJIS compliance (Criminal Justice Information Services).

What is CJIS compliance? Criminal Justice Information Services (CJIS) analyzes criminal justice information (CJI) from law enforcement centers around the country and provides a centralized database to store and access CJI. To use CJIS databases, organizations must comply with government regulations:

Support your need to collaborate internally and with external agencies, and unlock digital workflows to support remote government workers and distributed agency teams.
Virtru’s data-centric, end-to-end encryption and granular access controls help protect CJI stored in or shared via email and file systems like Gmail, Google Drive, and Outlook from access by unauthorized users with AES-256 bit encryption, FIPS 140-2 compliant modules, and two-factor authentication.

Human error — particularly when it comes to email — is one of the leading factors in data breaches. With the Virtru Data Protection Gateway and DLP, you can automatically encrypt sensitive emails and attachments shared by users who handle CJIS-protected data.






“By enabling full compliance for our law enforcement agency, Virtru gave us a path toward a complete cloud migration.”
Susan Lyon
Google Cloud Team Manager, State of Maryland
End-to-end encryption prevents unauthorized access to email and files containing CJI and maintains the privacy of citizens’ PII, supporting CJIS compliance.
Persistent protection to govern access throughout the data lifecycle, with the option to host your own encryption keys.
Boost user adoption and deliver simple recipient access that naturally fit into workflows between users, admins, and agency partners.
Virtru hosts everything in the U.S., uses encryption algorithms that comply with FIPS 140-2, is FedRAMP authorized at the moderate impact level, and adheres to the security controls defined by NIST SP 800-53. Virtru cannot access your protected data at any time.
With Virtru, you can keep CJI protected and controlled, without sacrificing the ability to collaborate.
/Updated%20Solutions%20Pages/law-enforcement-office-01.webp)
Without end-to-end encryption, use of cloud services requires CJIS-specific background screening and training for cloud vendor personnel and specialized SLAs and/or contractual clauses that compound costs and delay deployments.
Virtru’s end-to-end encryption streamlines CJIS compliance in the cloud by preventing vendor personnel from accessing CJI. Transparent key exchanges avoid complexities of other end-to-end encryption approaches like PGP and S/MIME for enhanced adoption and usage

Provide law enforcement agency employees and administrators easy-to-use data protection, embedded in existing applications. Complement user protections with DLP rules that automatically enforce encryption and control.
Enable seamless access for recipients and collaborators at external agencies and departments, without requiring new accounts, passwords, or software, for digital sharing workflows that support rapid delivery of services that support public safety.

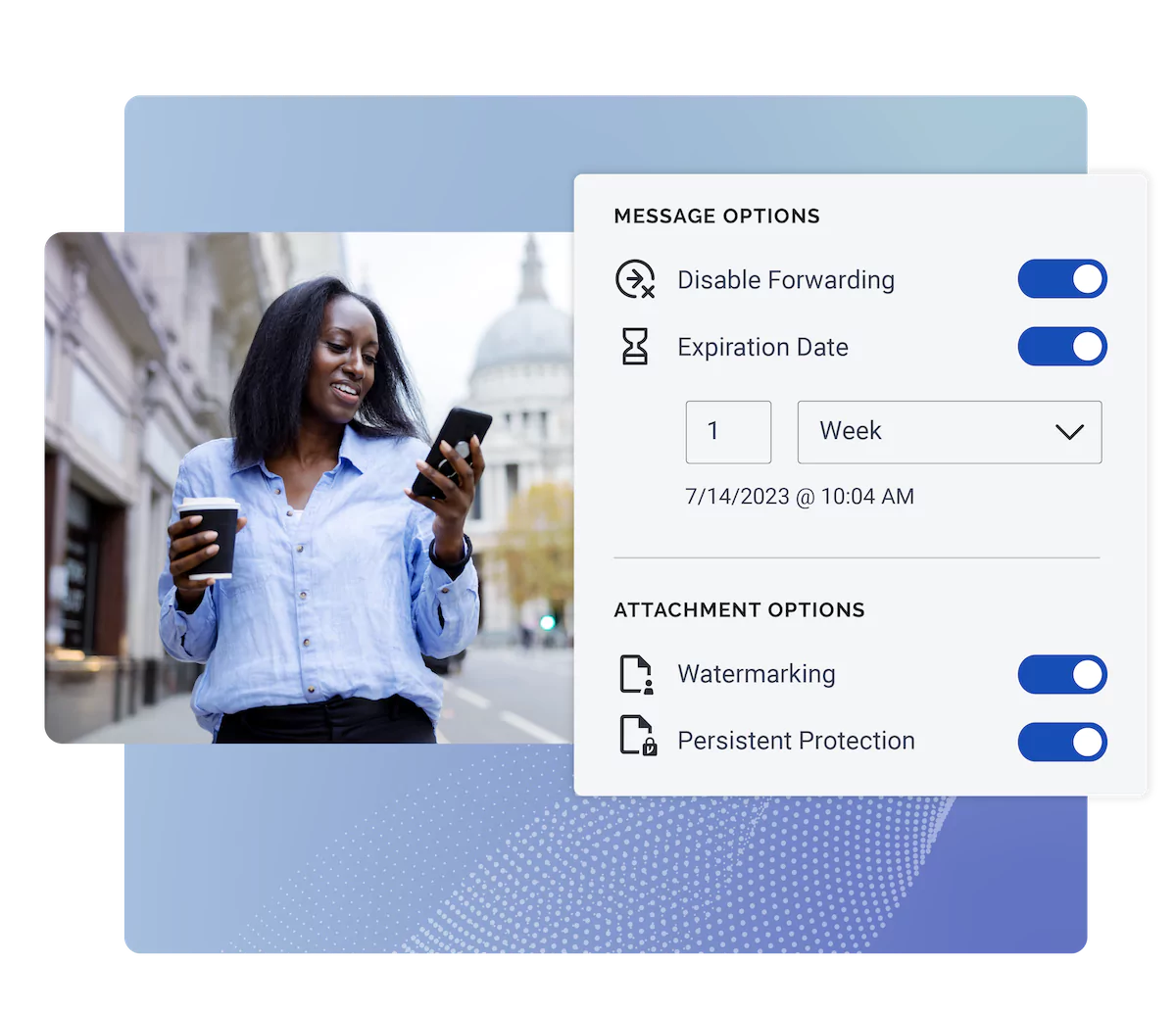
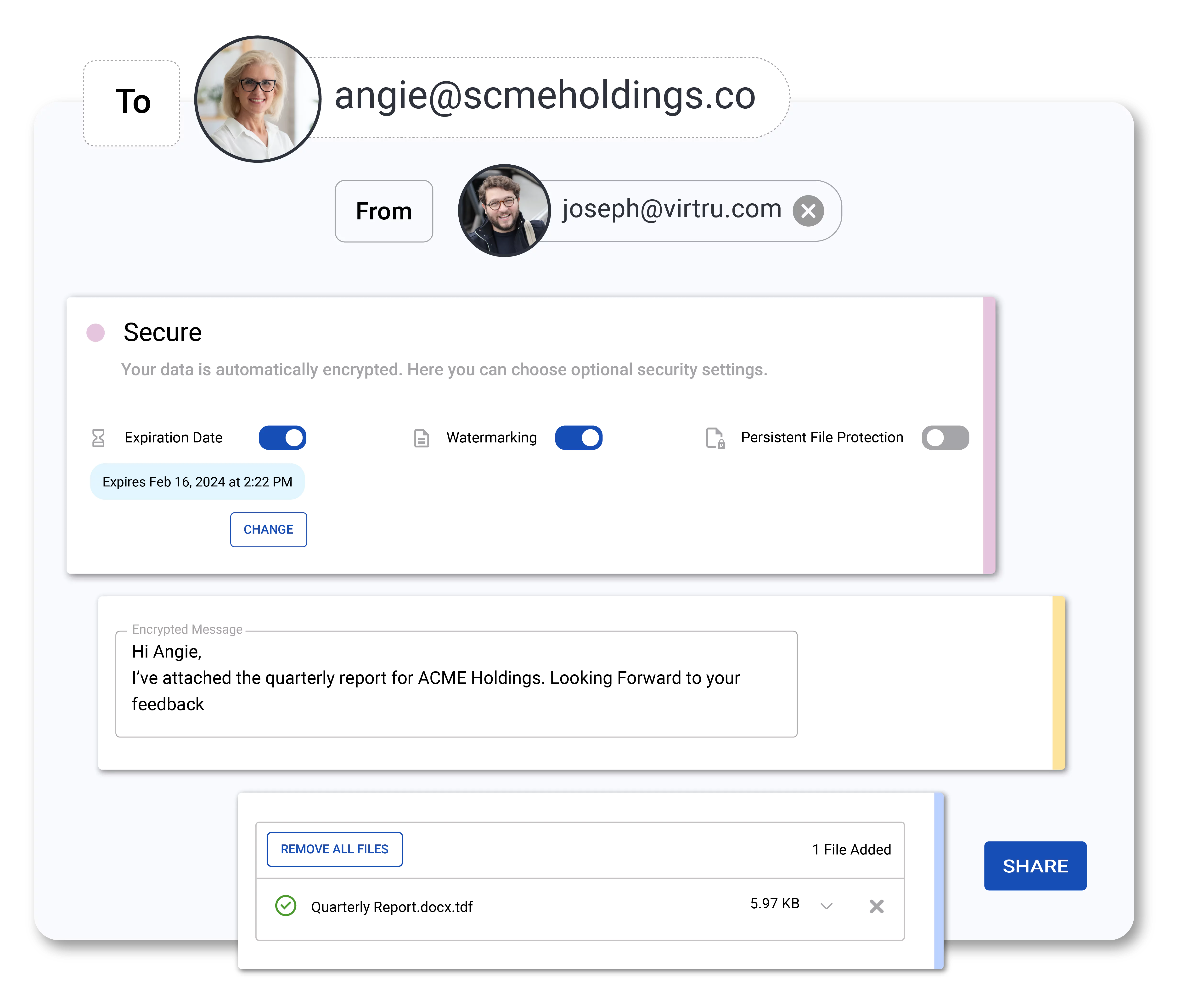
Enable secure data sharing, aligned with CJIS compliance, across agencies with attribute-based access controls (ABAC) for CJI that enable instant access revocation, expiration, disable forwarding, and document watermarking capabilities.
Audit who has accessed CJI, when, where, and for how long. Export event logs for analysis, or integrate with your SIEM for advanced threat analysis.
Maintain ultimate control of the encryption keys protecting all sensitive CJI stored and shared in the cloud with the Virtru Private Keystore.
Get expert insights on how to address your data protection challenges.





Contact us to learn more about our partnership opportunities.