ITAR Compliant Email and File Sharing
Prevent non-US entities from accessing ITAR technical data throughout cloud-based sharing workflows with data-centric protection and powerful key management capabilities.
Enable ITAR Compliant File Sharing Workflows
With end-to-end encryption, enforceable security settings, granular access controls, and customer-hosted key management capabilities, Virtru supports compliance with the International Traffic in Arms Regulation (ITAR) and helps prevent foreign access to technical data in the cloud.

/Virtru%20DSP%20FedRamp.webp)
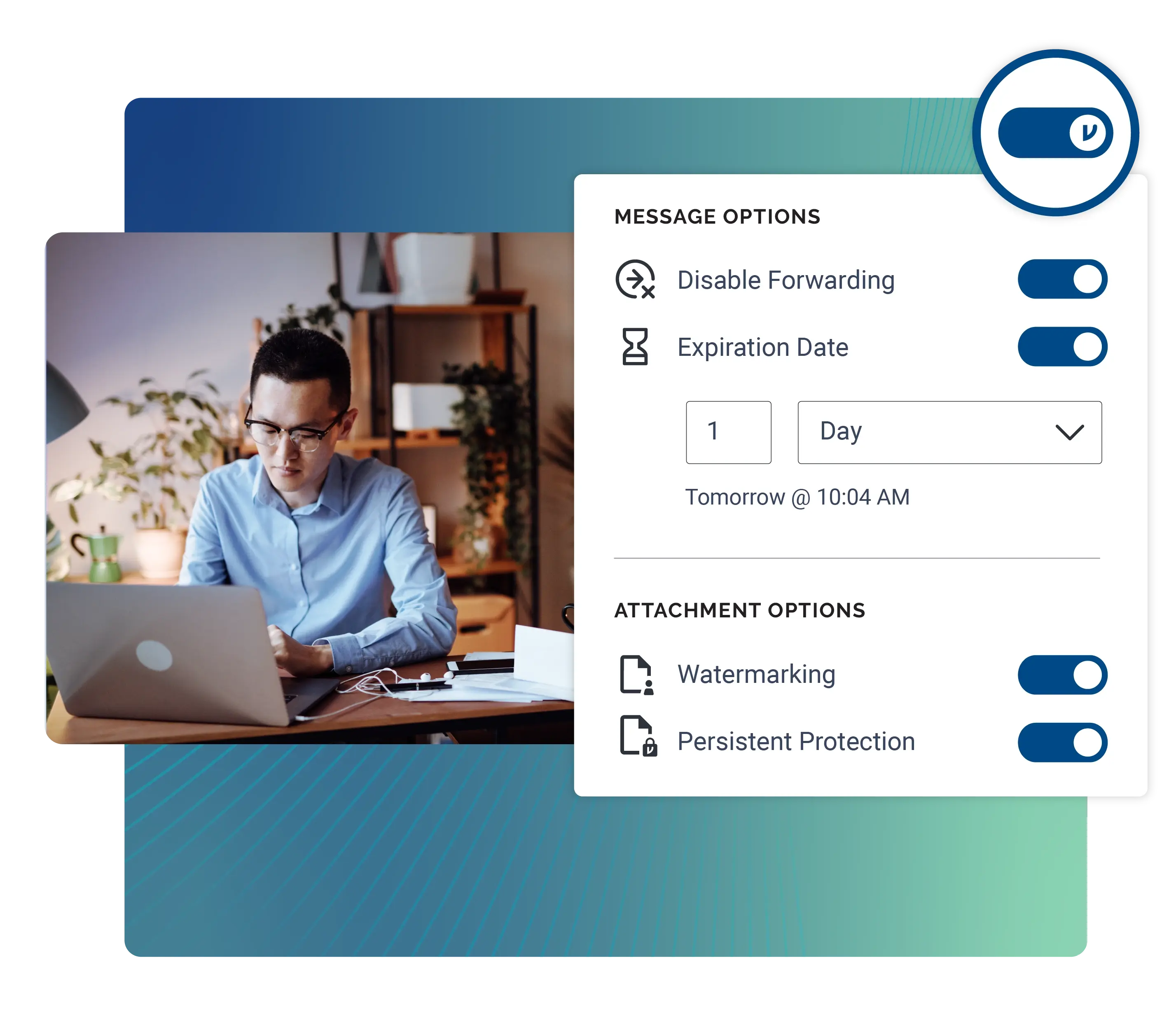

/Virtru%20Watermarking%20Outlook.webp)

/Virtru%20DSP%20FedRamp.webp)


/Virtru%20Watermarking%20Outlook.webp)


“In-house, we of course have to keep everything securely stored, both physically and electronically. Regarding communications with the outside world, we also have to keep that confidential, and this is where Virtru comes into play. Virtru helps us make sure that we keep emails containing confidential information properly encrypted and properly safe.”
Laurent Muller
IT Systems Manager
Encryption for the ITAR Carve-Out Rule
Virtru helps organizations meet the State Department’s 120.54 encryption carve out by protecting ITAR technical data from access by non-U.S. entities wherever it’s shared, unlocking the cloud’s efficiency and cost-saving benefits.
Encrypt ITAR Emails and Files
Cryptographic protection must be applied prior to data being sent outside of the originator’s security boundary and remain undisturbed until it arrives within the security boundary of the intended recipient. This means encrypting data prior to emailing or sharing it.

NIST Compliant and FIPS 140-2 Validated Encryption
Encryption must be certified by the U.S. National Institute for Standards and Technology (NIST) as compliant with the Federal Information Processing Standards Publication 140-2 (FIPS 140-2), or meet or exceed a 128-bit security strength.
Encryption Key Management
Information that can be used to decrypt (access) the technical data subject to ITAR compliance may not be shared with a third party (such as a cloud or email provider). A best practice is to manage your encryption keys separately from the data: On premises or in a private cloud.
Clarifying CMMC and ITAR for Contractors
Granular Audit and Access Control for ITAR Compliance
ITAR compliance can be complicated, but Virtru makes it remarkably simple for your teams to securely share sensitive technical data via emails and files.
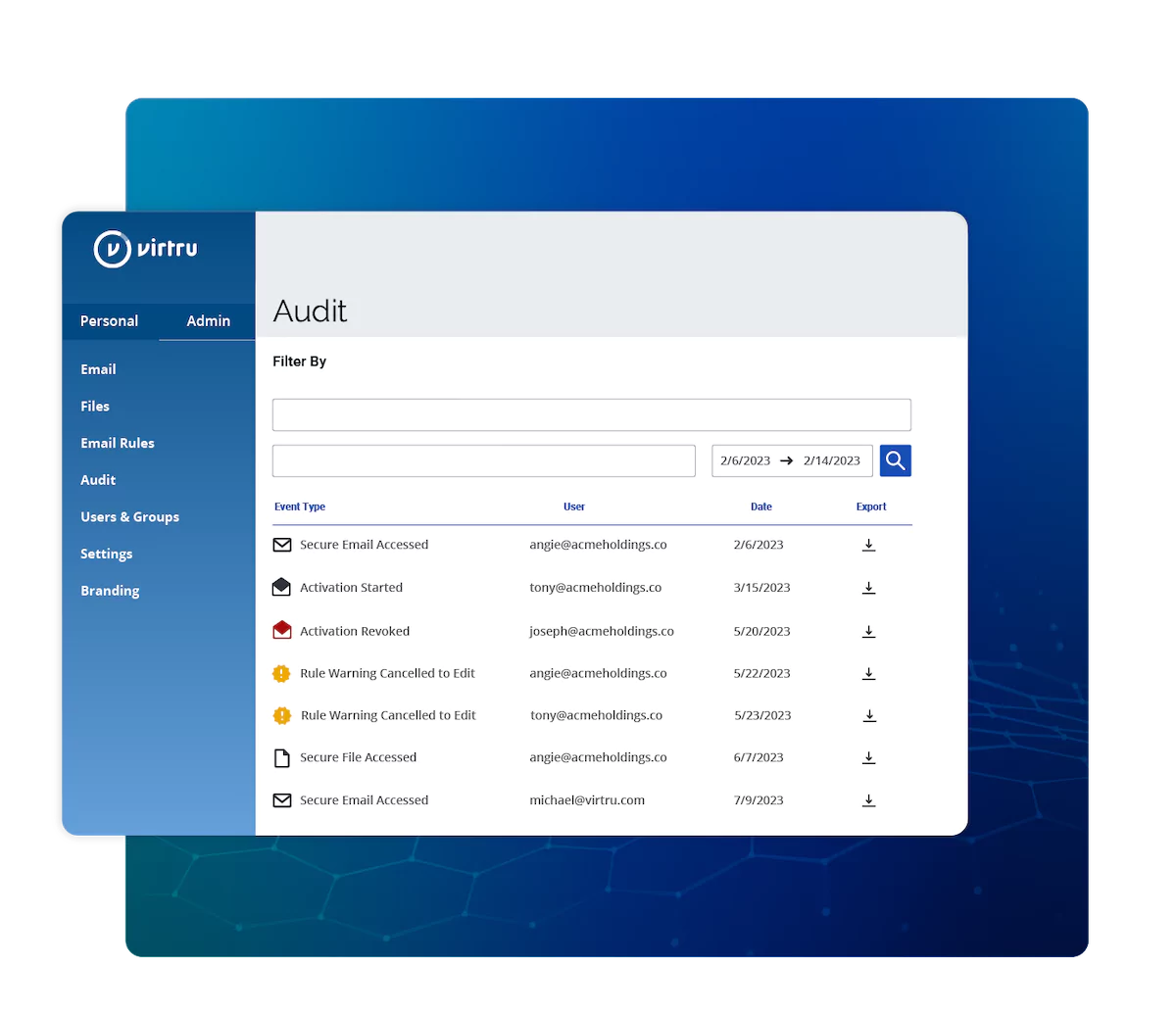
Granular Audit Trails
See and govern your organization's secure email and file sharing from a centralized location. Admins appreciate the comprehensive view that Virtru provides in the Control Center, which tracks the data that's been shared, who has accessed it, and what policies have been attached to each shared item.
Automate ITAR Data Encryption
People make mistakes. Don't let that impact your sensitive ITAR data. With the Virtru Data Protection Gateway, you can automatically detect and protect sensitive emails and files before they leave your organization, helping you confidently support ITAR encryption requirements.
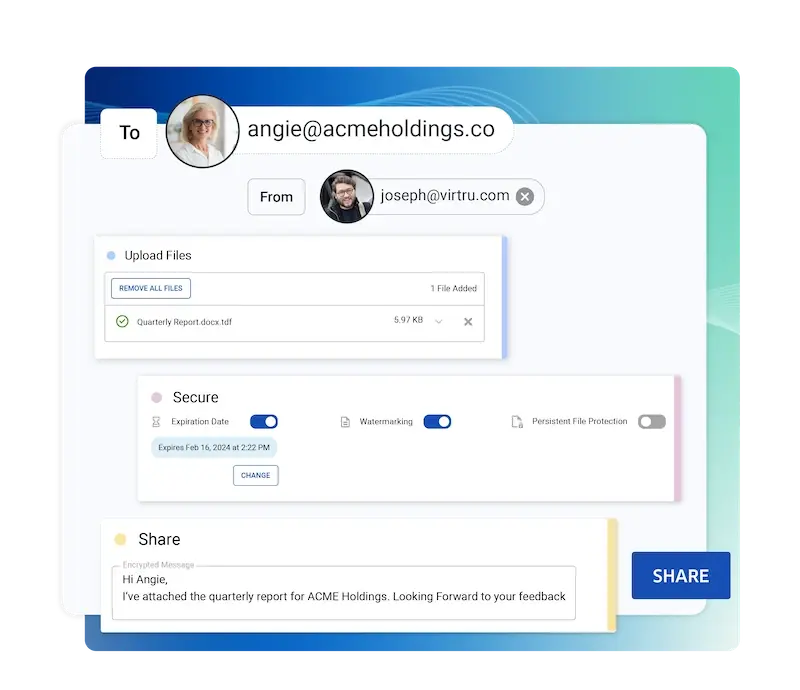
Encrypted File Sharing Up to 15 GB
With Virtru Secure Share, you can securely send and receive large files, such as video footage, CAT files, or product details. Easily collect sensitive files from partners across the supply chain, and give your teams a way to maintain control and visibility over the files they share externally.

The Data Security Platform Trusted by the U.S. Intelligence Community
Built on the ODNI open standard Trusted Data Format (TDF), The Virtru Data Security Platform underpins all Virtru's products, providing military-grade security, fine-grained access control, and ease of use to every data sharing workflow.
Resources
Get expert insights on how to address your data protection challenges.
Ready to take the next step?
6,100 CUSTOMERS TRUST VIRTRU FOR DATA SECURITY AND PRIVACY PROTECTION.




Book a Demo
Become a Partner
Contact us to learn more about our partnership opportunities.


