Datasheet
Protect Technical Data and Support ITAR Compliance
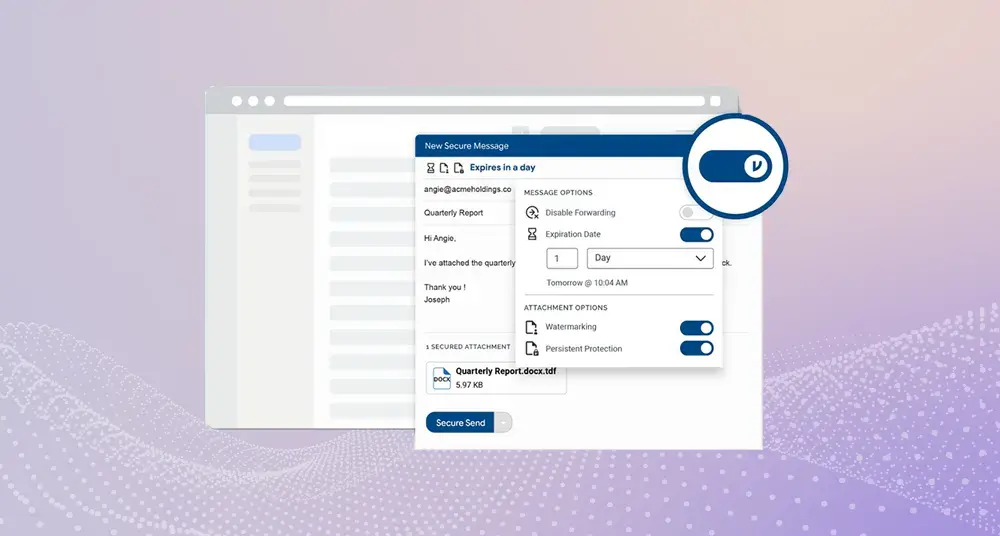
Virtru’s end-to-end encryption, enforceable security settings, granular access controls, and customer-hosted key management capabilities prevent foreign access to technical data in the cloud.
Enable ITAR Compliant Sharing and Storage of Technical Data
The ITAR Encryption “Carve Cut” Rule states that:
- Cryptographic protection must be applied prior to data being sent outside of the originator’s security boundary and remain undisturbed until it arrives within the security boundary of the intended recipient. This means encrypting data prior to emailing or sharing it.
- Encryption must be certified by the U.S. National Institute for Standards and Technology (NIST) as compliant with the Federal Information Processing Standards Publication 140-2 (FIPS 140-2), or meet or exceed a 128-bit security strength.
- Information that can be used to decrypt (access) the technical data may not be shared with a third party.
How Virtru Helps You Meet ITAR Compliance
Virtru hosts everything in the U.S., uses encryption algorithms that comply with FIPS 140-2, is FedRAMP authorized at the moderate impact level, and adheres to the security controls defined by NIST SP 800-53. Virtru cannot access your protected data at any time.
Related Resources
Get expert insights on how to address your data protection challenges




/Fintech%20Startup.webp)

/Gmail%20Confidential%20Mode.webp)


/county-health-departments.webp)