Protect Intellectual Property and Strengthen Compliance
Your data is your competitive advantage: That includes intellectual property, strategic plans, and sensitive information like customer data. Virtru helps you safeguard that valuable information.

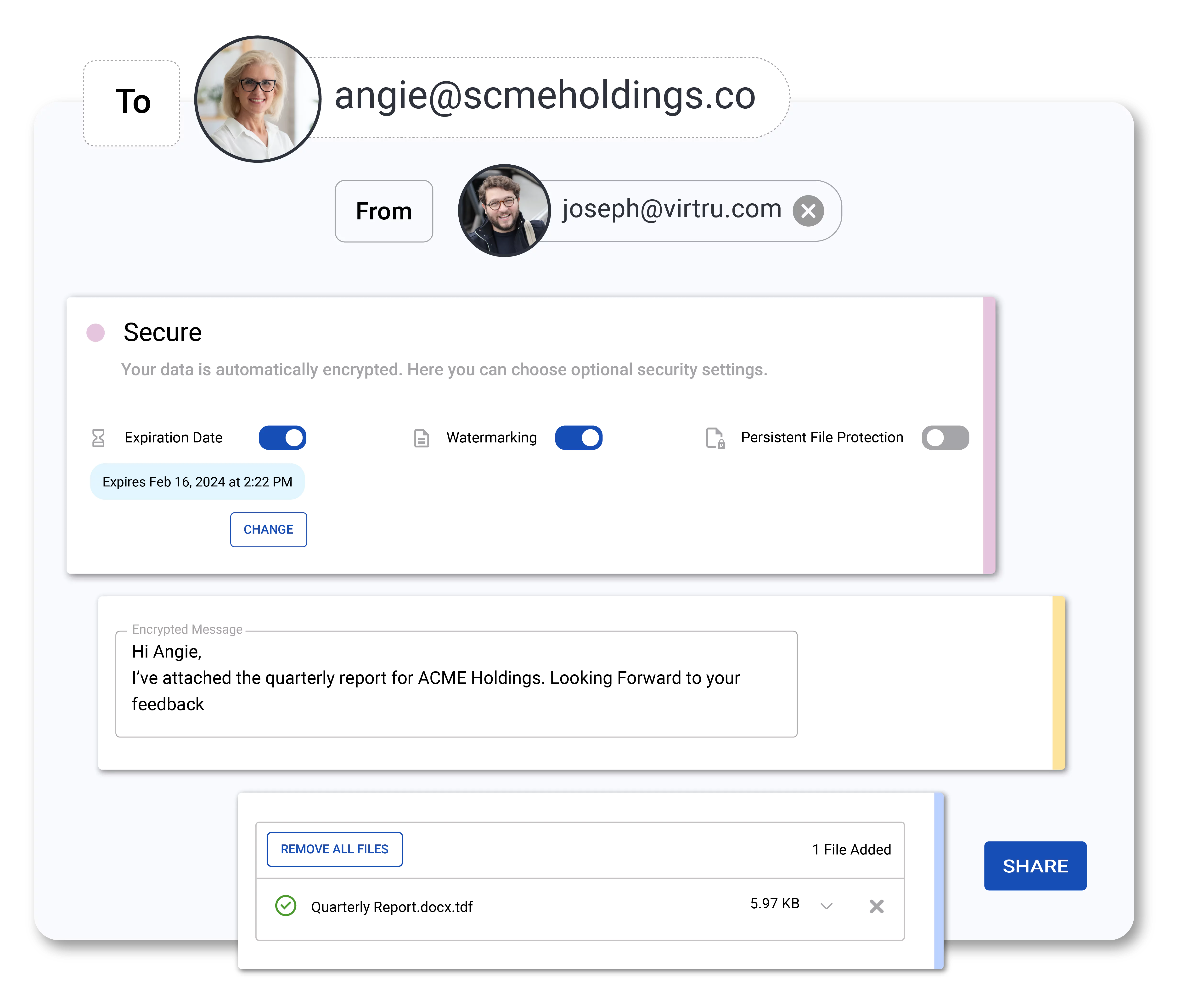
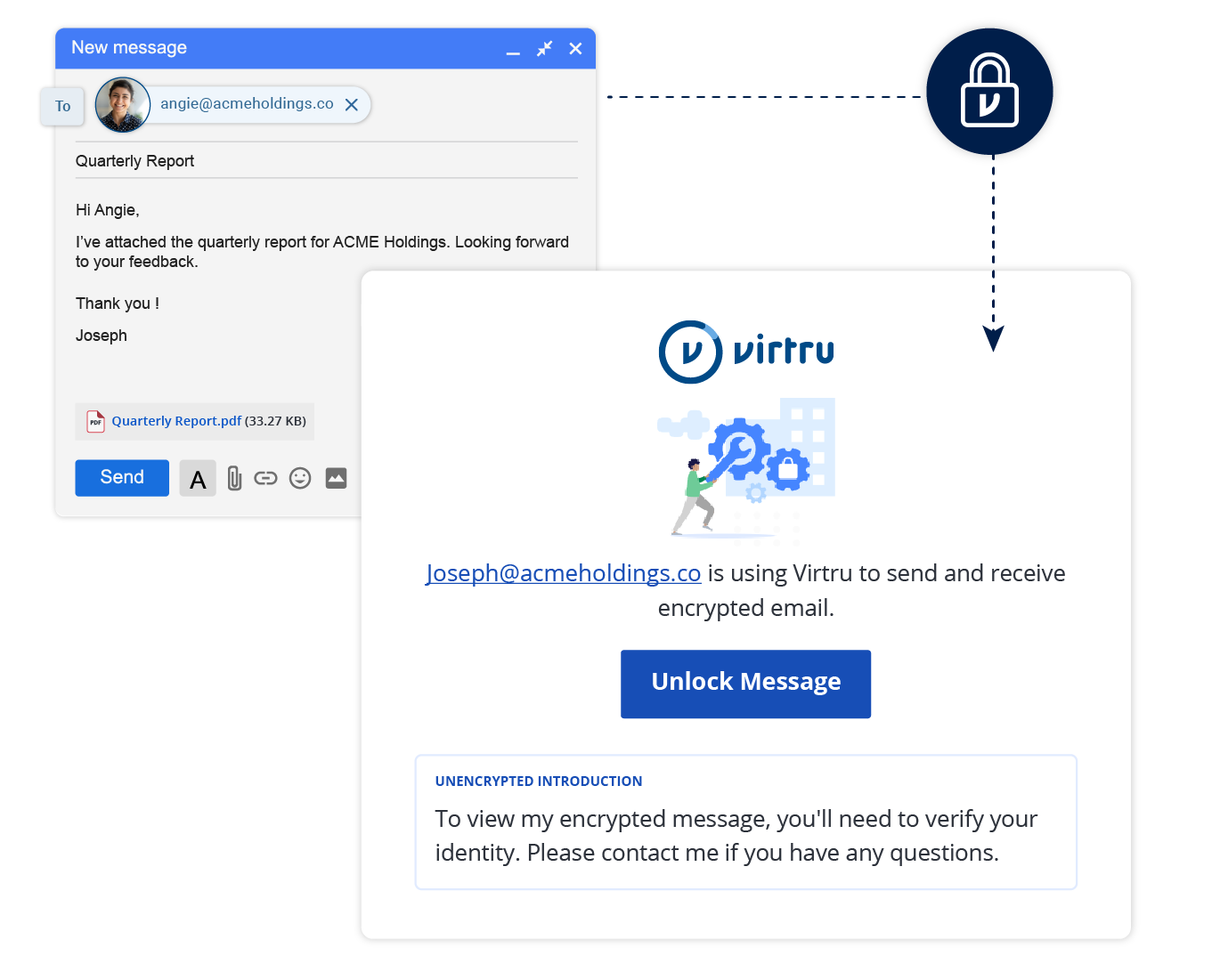
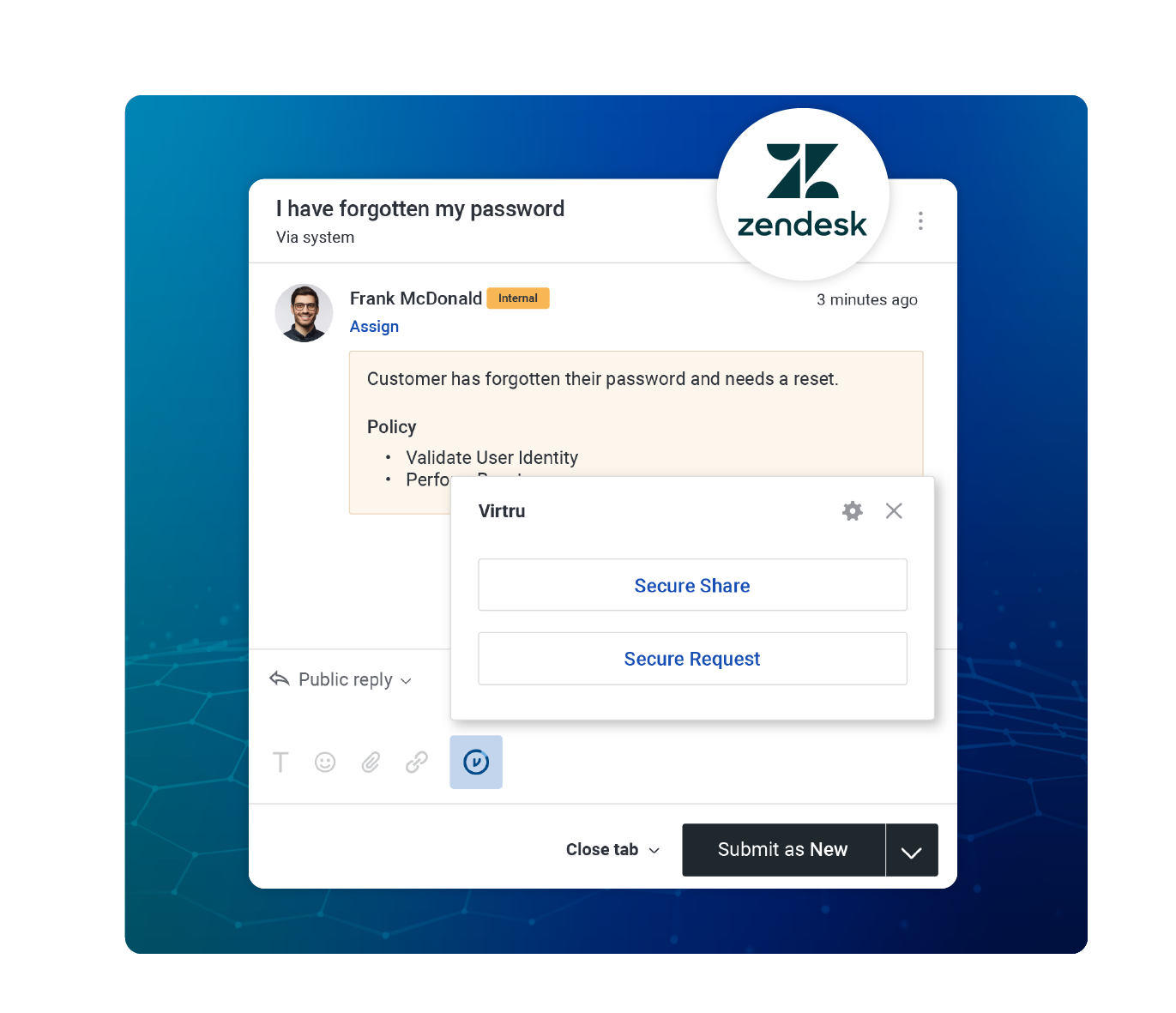
Centrally Manage and Monitor Data Access
Control proprietary data wherever it’s shared with instant access revocation, expiration, disable forwarding, and document watermarking.
Audit who has accessed your data, when, where, and for how long. Integrate with your SIEM to flag unusual activity.








.jpg)

