The Unique Virtru Advantage:
Data-Centric Security
Apply encryption, policy, and access controls directly to data flowing in and out of your organization via email, files, and SaaS applications.
Take Total Control of Your Data
Data isn’t static. It moves in and out of your organization at high velocity. It’s always in motion, and it’s always changing. Think about your organization’s most sensitive, proprietary data.
Are you protecting that data across its entire lifecycle — everywhere it moves?
Do you have a clear picture of how and where it’s been shared?
Once it leaves your organization, do you have any control over how it can be accessed?
If something goes wrong, do you have a way to take that data back?
Virtru gives you that control. Powered by the Trusted Data Format, our open, military-grade encryption wraps each data object in a layer of security and privacy that stays with the data, forever — giving you complete control at all times.
Data-Centric Security Solutions for Your Most Important Workflows
Over 8,000 Customers Worldwide Trust Virtru for Security, Privacy, and Compliance
Protection by Proxy vs. Pinpointed Data Protection
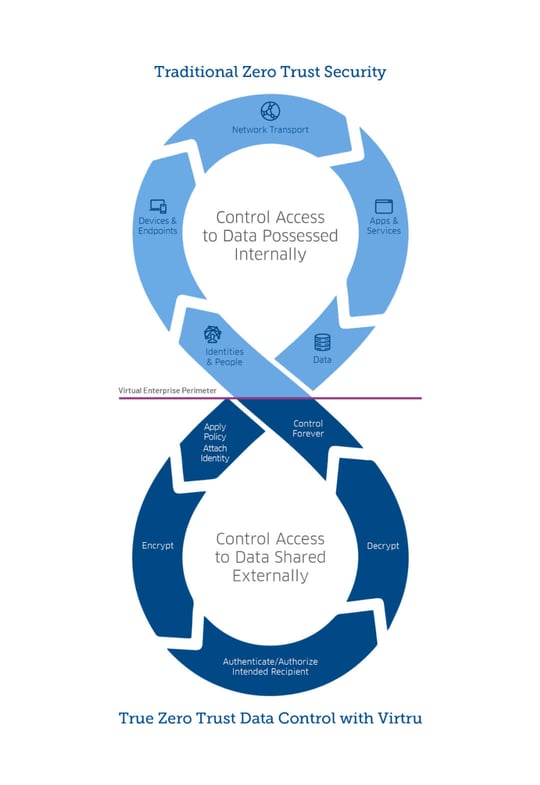
A first principle of Zero Trust security is “Never trust, always verify.” This applies to identities, endpoints, network traffic, applications, and, indeed, the data itself.
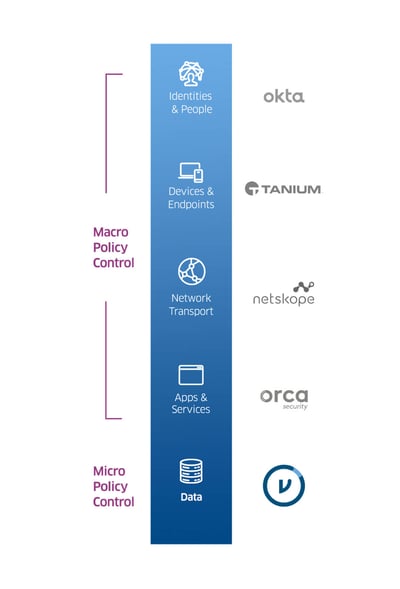
Regardless of the Zero Trust reference architecture you are aligned with (DoD, NIST, Forrester ZTA), there are five pillars that must be considered as part of your security transformation. In today’s world, many organizations actively migrating to the cloud understandably prioritize investments aimed at securing identities, devices, and networks.
Further, as data breaches continue to increase exponentially, organizations are increasingly expanding their Zero Trust initiatives to include policies applied to the data itself. Such efforts can include remarkably simple policies applied to email and files, automated protection of data flowing through SaaS applications, or sophisticated policies applied to multi-party analytics.
Getting Smarter About Data Centric Security
Prioritize Ease of Use
Deploy tools that make it easy and intuitive for your workforce to protect data. Virtru allows you to implement Zero Trust security without disrupting end-user workflows.
Attach Attribute-Based Controls to Data
Role-based access controls can cause you to over-grant data access to your employees. Use Virtru to assign granular tags to data, so it can only be accessed by those with a true need to know.
Revoke Access When Circumstances Change
People change jobs, get reassigned, and work on short-term projects. If, and when, circumstances change, use Virtru to revoke data access instantly, at any time.
Secure Data Across Multi-Cloud Environments
Whether your teams are using Microsoft or Google cloud services, or a combination of the two, Virtru’s data protection is cloud-agnostic — making secure, cross-cloud collaboration easy.
Wherever You Are, Advance Your Zero Trust Strategy with Virtru
Let’s face it: Evolving toward a Zero Trust security architecture is hard work. It involves a complex set of practices that span all aspects of IT; from identity, to devices, to networks, to apps, and all the way down to data itself.
It’s no secret how difficult and expensive it can be to implement Zero Trust controls for all phases of the digital value stream. What might be a secret, however, is just how easy and inexpensive it can be to apply Zero Trust controls directly to your sensitive data flowing in and out of your business via email, files, and SaaS applications.
Regardless of where you are on your Zero Trust journey, Virtru makes it easy for you to take the first step (or the last step) with data-centric policy controls that can be deployed in less than a day, for less than you might expect.


“One of our company values is to dare to simplify. We were looking for a solution that could easily scale as we grow and was also easy for our customers to use. That’s why Virtru is absolutely ideal for us.”
Ram Avrahami
Head of Global IT and IS
Next
Read the Case Study

“When your business has private, confidential information about people, securing that data isn’t an option—it’s an absolute requirement. You need a secure platform to deliver that capability, and Virtru is the best in the market.”
David Nicholson
Founder and Managing Director
DNA Worldwide
Read the Case Study


“Virtru’s seamless integration with our cloud partners allows us to grow and deploy quick data protection solutions that fit our needs.”
Chad Bairnsfather
CISO
Health IQ
Read the Case Study

“One of our company values is to dare to simplify. We were looking for a solution that could easily scale as we grow and was also easy for our customers to use. That’s why Virtru is absolutely ideal for us.”
Ram Avrahami
Head of Global IT and IS
Next
Read the Case Study

“When your business has private, confidential information about people, securing that data isn’t an option—it’s an absolute requirement. You need a secure platform to deliver that capability, and Virtru is the best in the market.”
David Nicholson
Founder and Managing Director
DNA Worldwide
Read the Case Study


“Virtru’s seamless integration with our cloud partners allows us to grow and deploy quick data protection solutions that fit our needs.”
Chad Bairnsfather
CISO
Health IQ
Read the Case Study