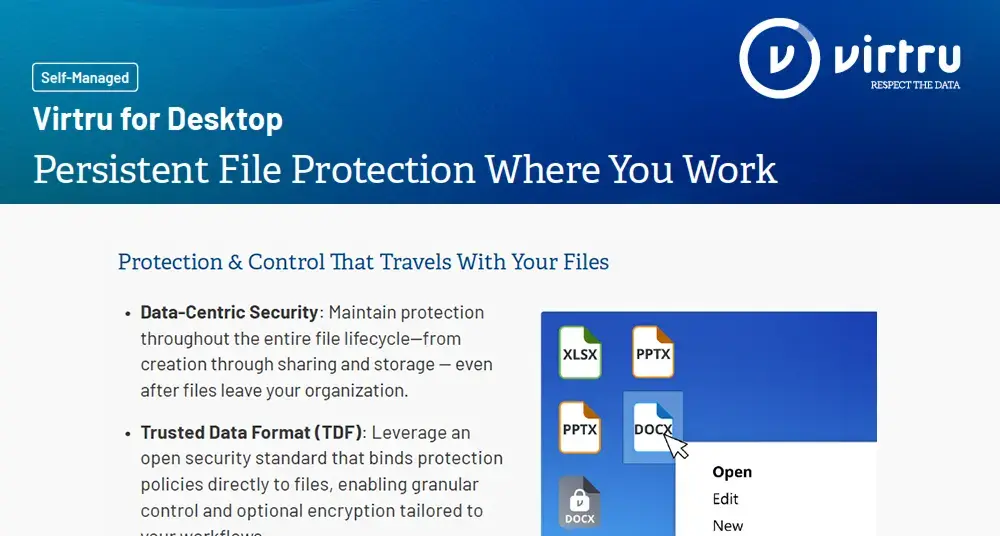
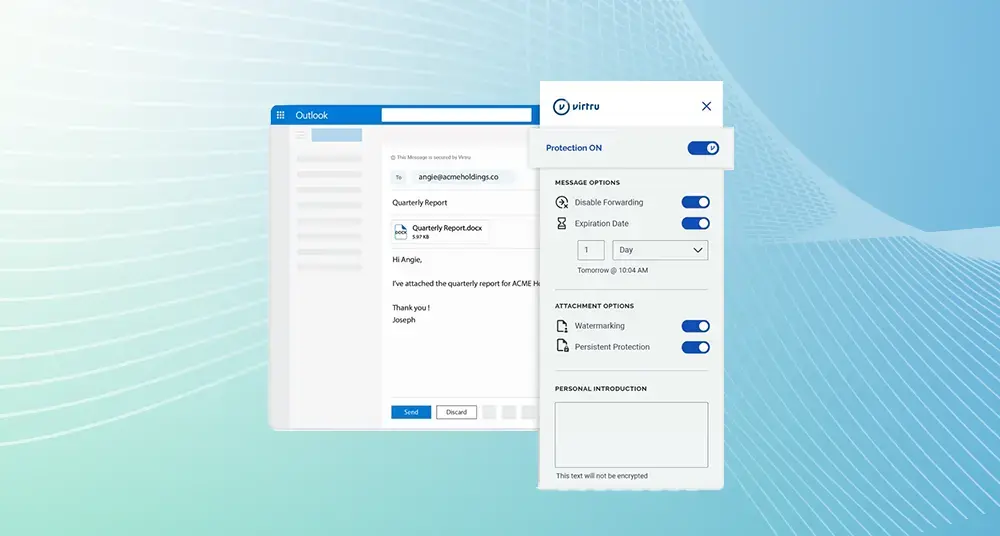
PII Protection Checklist and Best Practices
Download this free PII protection checklist to learn how to enable secure, compliant sharing workflows to maintain the privacy of PII, meet compliance requirements, and improve collaboration.
Download Datasheet
What You'll Learn
- 6 steps to securing PII, including the critical step of implementing an encryption solution.
- What features to look for in an encryption solution.
- How Virtru's end-to-end encryption can protect PII throughout digital sharing workflows.
As organizations collect, process, and store personally identifiable information (PII) they must also accept responsibility for protecting this sensitive data. After all, data breaches can occur at all levels of organizational sophistication, but the impacts on the organization are often the same: breaches are costly, time-consuming, and damaging. Remember, one careless employee can result in PII being shared with unauthorized recipients.
Every single organization stores and uses PII, either on their employees or customers. To better understand how to protect the PII within your organization and beyond, download a copy of our PII protection checklist.