TABLE OF CONTENTS
See Virtru In Action

Sign Up for the Virtru Newsletter


Fifteen months ago, May 12, 2021 was the day that President Biden issued the Executive Order on Improving the Nation’s Cybersecurity.
Nine months ago, January 26, 2022 was the day that the Office of Management and Budget (OMB) released a 28-page strategy memo for implementing Zero Trust cybersecurity in federal organizations.
Last week, on September 7, 2022 David McKeown, Department of Defense Deputy CIO for Cybersecurity, spoke at the Billington Cybersecurity Summit and outlined the Defense Department's new framework for implementing zero trust security controls which includes 90 clearly defined capabilities.
Having read EO 14028 and the OMB memo both — and having spent a few days myself at the Billington Cybersecurity Summit last week, it's very clear that Zero Trust security transformation is a journey, not a destination. It's a massive landscape that requires a wide range of tools, technologies, and practices to govern and control everything from human and machine identities, to end points and devices, to networks, to applications, and most important of all, the data.
At Virtru, we do not claim to be a singular solution for Zero Trust governance. We do however believe that our collection of zero trust data control products provide a strong foundation for fostering agency collaboration and mission success while simultaneously protecting what matters most: your data.
Here is our simple, four-part vision for why Federal agencies should embrace data-centric policy controls to foster secure collaboration in support of their Zero Trust journeys.
Implementing Zero Trust security controls in a network-centric manner via physically separate domains often diminishes flexibility, limits collaboration across multiple partners, and reduces operational/mission effectiveness. We need to think beyond the network for a more effective solution.
An important part of Zero Trust security and risk management is extending policy controls all the way down to individual data objects. Why is this important? Because, when we apply granular policies to individual pieces of data, we can empower mission teams to share information by default with partners (not by exception), and thereby maximize operational effectiveness without sacrificing security.
By acknowledging data as a strategic resource and embracing data centric policy controls, we will learn to share data more openly and yet still have the ability to safeguard information via policy enforcement points which are highly scalable, and can automatically approve or deny human access to information based on a person's “need to know.”
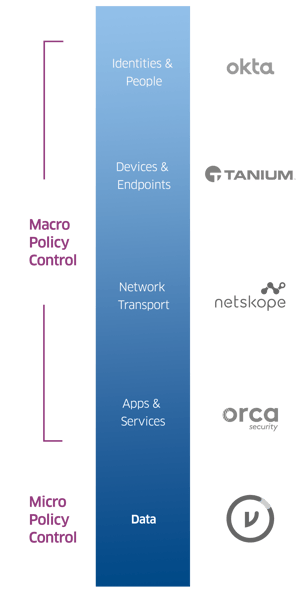
As mentioned above, implementing Zero Trust takes a village — you'll likely have several partners in making your Zero Trust posture a reality. Choose partners aligned with your vision, who will empower your organization to do its best work without slowing it down.
It's essential to ensure you're covering identities and people; devices and endpoints; network transport; and apps and services. But, foundational to all of these macro policy controls, is the ability to apply data-centric, micro policy control that protects the data itself, everywhere it moves. That's where Virtru comes in.
Virtru empowers more than 7,000 customers with Zero Trust security. We'd love to help you take your Zero Trust posture to the next level. Book a demo with our team to start the conversation.

A proven executive and entrepreneur with over 25 years experience developing high-growth software companies, Matt serves as Virtu’s CMO and leads all aspects of the company’s go-to-market motion within the data protection and Zero Trust security ecosystems.
View more posts by Matt HowardSee Virtru In Action
Sign Up for the Virtru Newsletter











Contact us to learn more about our partnership opportunities.