Why Conventional Wisdom for Zero Trust Security Falls Short


Zero Trust security transformation. Why is everyone talking about it? Because we now live and work in a digital world without walls. And, without walls, cyber leaders must rethink their entire strategy for defending businesses against attacks and securing valuable data.
But what exactly are people saying about Zero Trust? And, more importantly, what aren’t they saying? What critical points might be missing from the current Zero Trust conversation?
Conventional cybersecurity wisdom has brought us this far, but in order to adapt to a rapidly escalating threat landscape, we have to think differently. We have to think beyond the status quo.
Old Habits Die Hard
The rapid adoption of public cloud infrastructure means that most companies have migrated some, or all, of their IT operations to the cloud. Furthermore, the global pandemic has fundamentally changed the nature of work itself, which now requires every IT department to support remote-first operations. Simply stated, the IT perimeter has vanished – and with it, the proverbial castle wall. Thus, companies everywhere are actively rethinking their approach to cyber security.
But, old habits die hard.
Despite living in a world without walls, most cyber professionals today still have perimeter-centric thoughts defining their priorities and guiding their actions. As a result, they tend to focus a majority of their time and energy on one thing: keeping bad guys off their networks and out of their systems. They do this by investing heavily to implement identity-based perimeters, complete with single sign-on and multi-factor authentication. They invest further to strengthen endpoint security. They dig even deeper into their pockets to implement best-in-class network security solutions and services like cloud access security brokers (CASB) in an attempt to bring SaaS apps inside of virtual perimeter. In other words, at this early stage of the Zero Trust security transformation journey, the prevailing cybersecurity mindset is still focused on defending the ever-expanding digital attack surface from external threats – rather than securing sensitive data objects which live on the digital protect surface.
Conventional Wisdom Falls Short
In the modern economy, organizations that are able to collect, analyze, and mine massive amounts of data have a huge advantage over their competitors and a clear path to rapid growth and value creation. However, these same companies that possess massive amounts of sensitive data must contend with huge overhead costs, including regulatory compliance, engineering operations, security risk management, and the enormous obligation that comes with being trusted to protect sensitive and private information about customers, employees, and business partners.
Furthermore, because data is the lifeblood of every business, organizations find themselves constantly sharing it with others, with or without proper controls. Similarly, companies must accommodate the fact that sensitive data, owned by others, is frequently being shared with them.
Today, conventional wisdom advocates that cyber leaders focus first and foremost on defending the digital attack surface from external threats. Such thinking isn’t wrong. It’s just a bit myopic, because it diminishes the critical importance of securing the data itself, which flows constantly in and out of your digital protect surface.
Thinking Outside of the Zero Trust Box
Against this backdrop, cyber security leaders would be well served to expand their Zero Trust thinking beyond conventional wisdom and simply defending their ever expansive attack surface. They should challenge themselves and their teams to examine innovative solutions designed to secure an organization’s protect surface where sensitive data actually lives and breathes, flowing in and out of businesses on a daily basis.
A convenient way for cyber security leaders to think beyond conventional wisdom is to ask themselves and their teams three critical questions:
- How should we govern sensitive data that we own and possess internally?
- How should we govern sensitive data that we own, but no longer possess internally because we’ve shared it externally?
- How should we govern sensitive data that has been shared with us, but is owned by others?
Zero Trust Data Access (ZTDA) for Inbound Workflows
Conventional wisdom on Zero Trust Data Access (ZTDA) advises a five-pronged approach to governing risk:
- First, use micro-segmentation in datacenters and cloud environments to separate workloads.
- Next, embrace the principle of least privilege to allow each user to access only the data they need.
- Third, apply role-based access controls (RBACs) to make sure the right people have access to the right data.
- Then, leverage Security Assertion Markup Language (SAML) and single sign-on (SSO) to reduce the prevalence of passwords and insecure user behavior.
- And finally, take advantage of multi factor authentication (MFA) to further strengthen authentication and authorization.
Indeed, if your sole mission is to govern sensitive data that your organization owns and possesses internally – then it makes sense to follow conventional wisdom and invest all of your time and energy into governing which people and devices can access which data over a virtually secure network via inbound workflows.
Zero Trust Data Control (ZTDC) for Dynamic Workflows
Unfortunately, data isn’t static. It’s dynamic, constantly moving and evolving — born to be free in order to maximize its potential to shape strategies and inform important decisions. You can’t afford to lock it away. And you can’t afford to lose control of it either.
Thus, if your mission is to govern the entire protect surface and all forms of sensitive data, including data shared externally with third parties, then it is a good idea to think outside of the proverbial box. To do this, you will want to examine Zero Trust controls like Trusted Data Format (TDF) which is well-suited to facilitating secure collaboration, so you can guarantee access ONLY by intended identities, even when data has been shared externally.
Think Different – Say Hello to the Trusted Data Format
TDF is a super fast and affordable way for any organization to expand their zero trust security controls to encompass common information assets, like emails and files, which frequently contain sensitive and risky data.
TDF leverages military-grade data encryption to wrap data objects in a layer of security that remains with the data wherever it flows. We call this approach Zero Trust Data Control (ZTDC), because it gives you complete control over your data at all times – even after it has left your organization. You retain ownership and control for as long as the data exists, so you can always ensure access only by intended entities.
The graphic below shows how this works. The right hand side represents the conventional part of the zero trust wisdom as follows: identity and endpoint controls coupled with secure networks work in concert to determine which people and devices can access which apps and data with least privilege.
But the real power is on the left — and this is the essential part of the Zero Trust strategy that is often missing from conventional thinking. These are your collaboration and outbound workflows, and this is where TDF-based solutions give you a unique ability to minimize risk by securing granular pieces of data moving dynamically in and out of your business via emails, files, and SaaS applications. You can apply policy, attach identity, encrypt the data, authenticate and authorize the intended recipient, easily decrypt the data, and maintain control wherever the data flows and for as long as the data exists.
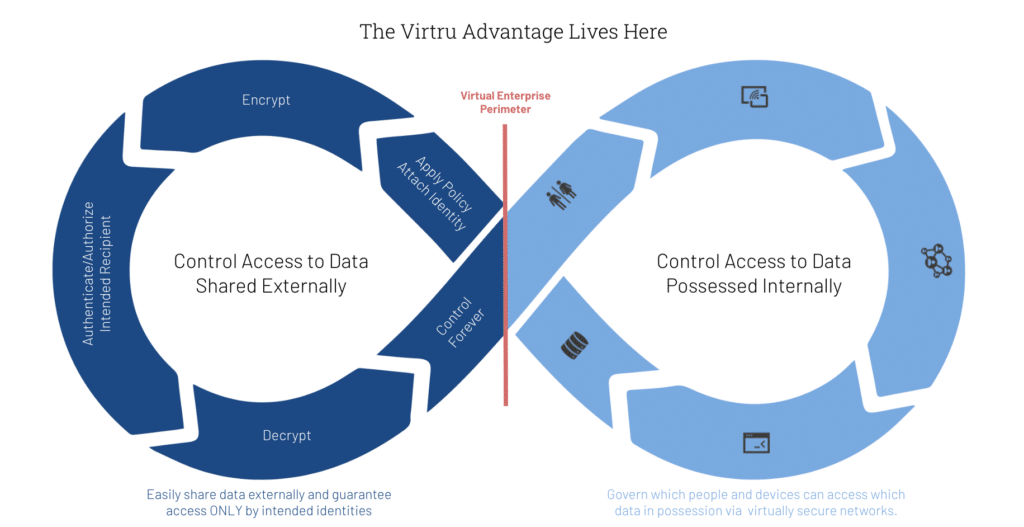
In this way, TDF compliments and extends your existing zero trust initiatives. It does so by creating a continuous, virtuous circle of policy control where you can enable your organization to collaborate with others and easily conduct business without ever losing control of sensitive information.
With TDF-based solutions, users can simply click a button to safely share sensitive data via email and files. Further, your organization can safely move customer data in and out of mission-critical software-as-a-service (SaaS) applications. Finally, TDF can easily help you govern data flowing to and from a vast array of IoT devices.
As cyber risk continues to grow exponentially, Zero Trust security transformations will only become a greater imperative. TDF-based solutions enable you to maintain Zero Trust Data Control over both your inbound and your outbound workflows – safeguarding the entirety of your protect surface and equipping you to share data with confidence.

Matt Howard
A proven executive and entrepreneur with over 25 years experience developing high-growth software companies, Matt serves as Virtu’s CMO and leads all aspects of the company’s go-to-market motion within the data protection and Zero Trust security ecosystems.
View more posts by Matt Howard









