The Definitive Guide to Gmail Encryption

Gmail is often praised for its convenience and seamless integration with Google Workspace, but its security features are equally impressive. Native encryption and extensive administrative controls allow businesses and users to secure Gmail, reducing risks associated with hackers as well as malicious insiders.
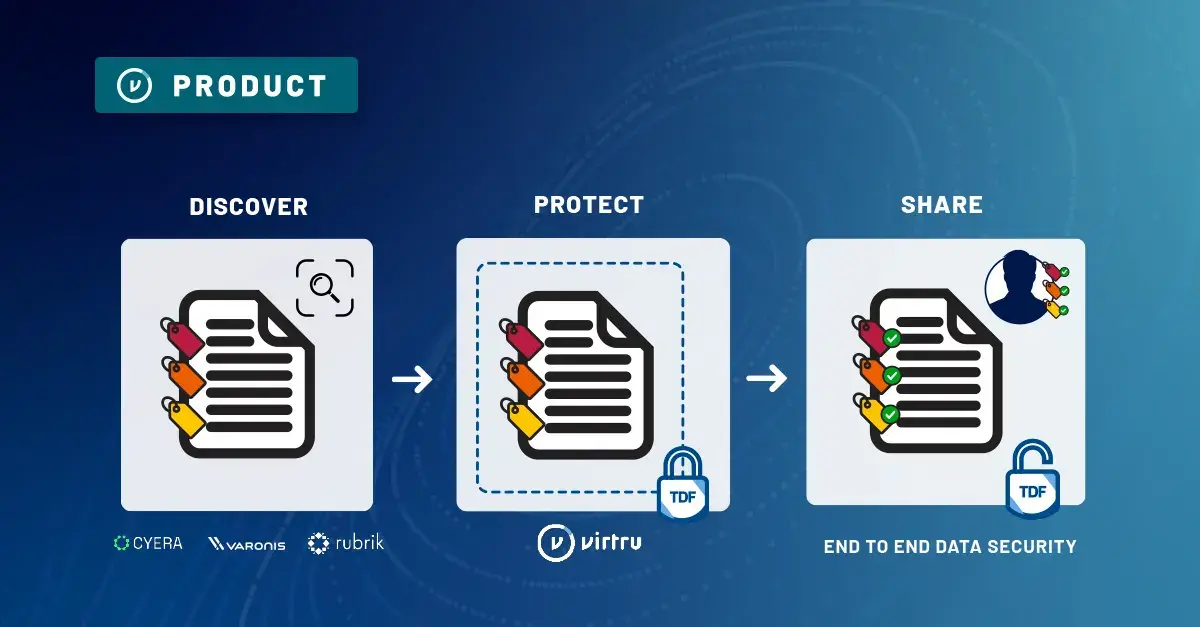
Gmail's native encryption does have its limits, but can be easily strengthened with an additional layer of client-side encryption, like Virtru for Google Gmail.
TLS Encryption: Google's Default Gmail Encryption
Google uses Transport Layer Security (TLS) to encrypt emails in transit. It provides an encrypted pipe through which your emails can travel. But TLS depends on both the sender’s and recipient’s email provider, so it doesn’t always work.
When you send a Gmail-encrypted email, your browser contacts Google’s server and creates a secure connection. The message is encrypted, sent to the server and decrypted. The server repeats the process with the next server, until it reaches your recipient’s server.
To help prevent unencrypted emails from exposure, Google warns users when TLS won’t work; an open red padlock symbol signifies that an incoming or outgoing message isn’t encrypted.
Google for Work users can also require TLS, preventing their email from sending or accepting messages that can’t be secured with Gmail encryption. You can require TLS for all inbound messages, all outbound messages or just certain domains and email addresses.
Gmail Confidential
Google offers Gmail Confidential mode to augment its TLS encryption services. Confidential mode is a feature that enables users to implement basic access management over their email. This means that users will be able to set expiration dates for messages, revoke access from certain users or prevent actions like forwarding and printing.
Where Gmail Encryption Falls Short
If both parties use Gmail encryption, the risk of your message being compromised is very low. However, if your recipient’s email service doesn’t use TLS, messages won’t be encrypted, and in some cases, the message simply won’t be sent.
Even if both parties use TLS, the message could pass through a hacked or improperly configured server outside of Google’s network, allowing a third party to decipher and read it.
Similarly, the access control provided by Gmail Confidential certainly improves security—but it doesn’t go far enough. It provides limited visibility for senders and admins, doesn’t take compliance or third-party access concerns into account and adds no additional encryption to email data. Your recipients may not be able to forward that email, but they can fully control your data if they download it or transfer it out of Gmail.
In other words, Gmail’s network is secure. But if your sensitive data isn’t properly configured within the network or leaves it entirely, the data is no longer encrypted and is exposed to risk.
Take Gmail Security One Step Further
The best way to secure your data is with data-centric protection. Data-centric security focuses on protecting the data itself regardless of where it is hosted, from applications to the body of an email.
Gmail End-to-End Encryption
End-to-end encryption is at the heart of data-centric security strategies. End-to-end encryption wraps every piece of data in a layer of protection at all times, not just in transit and at rest; it also ensures that only the sender and recipient can view the contents of an email. This protection stays with your data no matter where it goes, even after it leaves the email platform.
If your data itself isn’t encrypted and relies on TLS encryption, it is at a higher risk of exposure, potentially leading to compliance issues. Implementing end-to-end encryption helps to ensure that your organization is fully compliant with data security regulations, whether that means industry rules, HIPAA, FERPA, CJIS or GDPR.
Moreover, end-to-end encryption from a third-party plugin prevents your data from being exposed to your platform provider. Encrypted data is decrypted with encryption keys that unscramble that data. When both the keys and the data are stored in the same place or by the same provider, that provider can use those keys to decrypt your data as needed. This poses inherent risks, such as mandatory disclosure or a malicious insider accessing your emails. It’s therefore a best practice to store encryption keys and sensitive content separately: If one company, such as Google, controls both your data and your encryption keys, it can access your unencrypted data without your knowledge.
Implement Encryption with a Third-Party Provider
To truly eliminate risks and develop a strategy for complete email protection, reinforce native Gmail encryption with a third-party app that provides strong, data-centric encryption. This ensures that unauthorized users—such as hackers, Google or even your third-party provider— are not able to access your content.
Gmail’s native encryption is automatic, so it requires no setup, and it works with most recipients. Your email encryption add-on should have comparable ease of use and even better interoperability. Look for a provider that has one-click encryption and can send encrypted emails to any recipient—even if they don’t have the encryption plugin installed. Encryption should work as a browser add-on, and install quickly with little to no configuration.
Your Gmail encryption plugin should also address the weaknesses in TLS. Choose client-side encryption that protects emails and attachments, rather than just the connection between servers. Client-side encrypted emails stay encrypted until your intended recipient opens them. Even if a hacker intercepts a secure message in transit, they won’t be able to read it.
Encryption: Traditional and Innovative Options
S/MIME and PGP Gmail Encryption Plugins
S/MIME and Pretty Good Privacy (PGP) are two traditional options for added email security. Both provide data-centric security via different methods.
- S/MIME allows you to digitally sign your email with a private key. The recipient then verifies the message with your public key, improving security and preventing phishing. However, in order to send and receive encrypted emails, both the sender and recipient need to have each other’s S/MIME certificate.
- PGP plugins offer the reverse: you encrypt your email with the recipient’s public key, and the recipient decrypts the email with their private key. Either service presents complex challenges for your encryption key management.
Both plugins provide an additional layer of encryption. However, they both require users to manually exchange encryption keys. This adds a significant security risk: if your keys end up in the wrong hands as a result of this exchange, your data is suddenly unprotected. It also severely limits usability for end users: slowing down the email process, requiring more technical knowledge and adding additional steps for an end user to read an email. The added security significantly increases friction in email use.
Virtru’s Solution
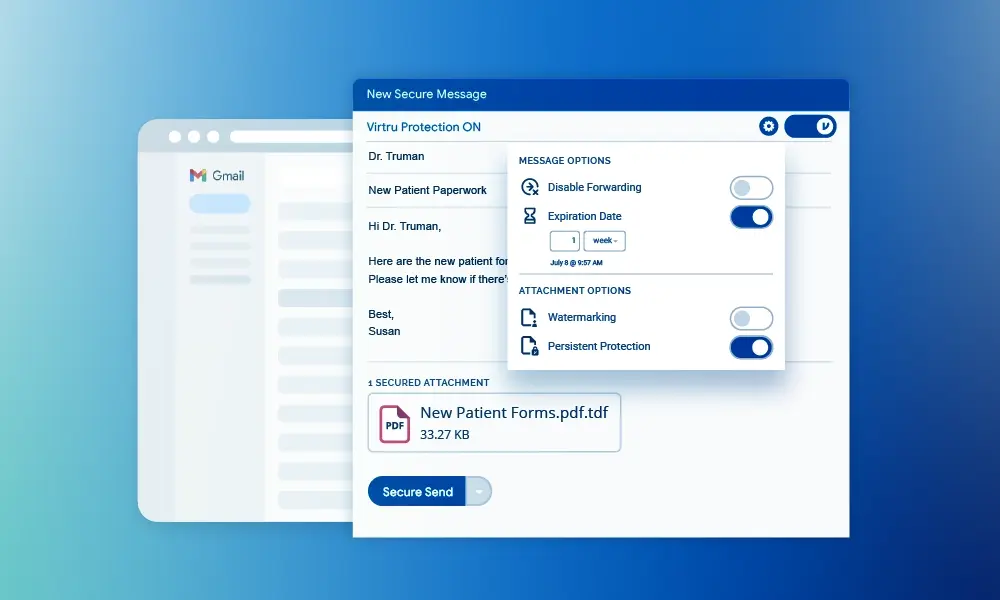
Virtru provides complete end-to-end encryption for your emails and all the data they contain, designed specifically for Gmail. Virtru’s encryption services are built directly into Gmail for ease of use: send and receive emails as you normally would, but with robust data-centric protection included. Your end-users won’t be impacted—there are no extra steps or clunky manual processes. The service also provides significant administrative control that goes beyond Gmail Confidential, with true visibility and full management and audit capabilities
You can also rest easy knowing that unwelcome eyes will not be able to view your data: Virtru’s encryption key management enables you to host your encryption keys separate from Virtru’s platform. No one, from Virtru to Gmail to outside threats, will access your data without permission. You’ll also be notified if non-authorized users attempt to access your data. If you suspect a data breach, Virtru enables you to suspend all data access until the threat is mitigated.
Take your protection a step further by encrypting your Google Workspace shared data, all of which rely on TLS encryption. This ensures that protection travels with your sensitive data, even when it leaves the server.

Editorial Team
The editorial team consists of Virtru brand experts, content editors, and vetted field authorities. We ensure quality, accuracy, and integrity through robust editorial oversight, review, and optimization of content from trusted sources, including use of generative AI tools.
View more posts by Editorial TeamSee Virtru In Action
Sign Up for the Virtru Newsletter