/blog%20-%20Ravenna%20Hub/ravenna-hub.webp)

Decrypted
The Virtru Blog
Tips, takes, and expertise for the data-centric security practitioner
/blog%20-%20Ravenna%20Hub/ravenna-hub.webp)
Education
Lessons from the Ravenna Hub Vulnerability
A recent security lapse involving Ravenna Hub, an online admissions platform used by families to enroll children into schools, ...
Read Post
Popular Posts

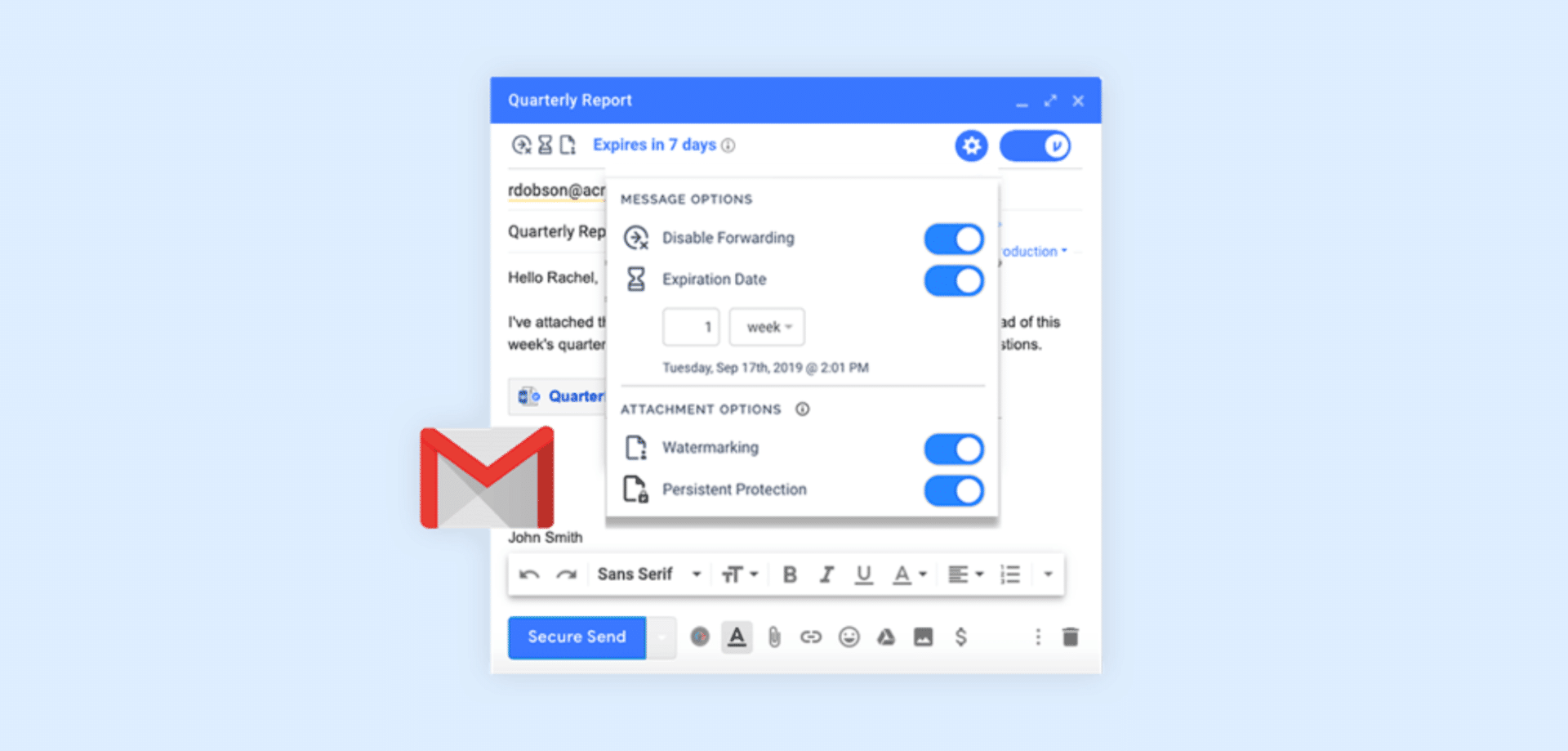
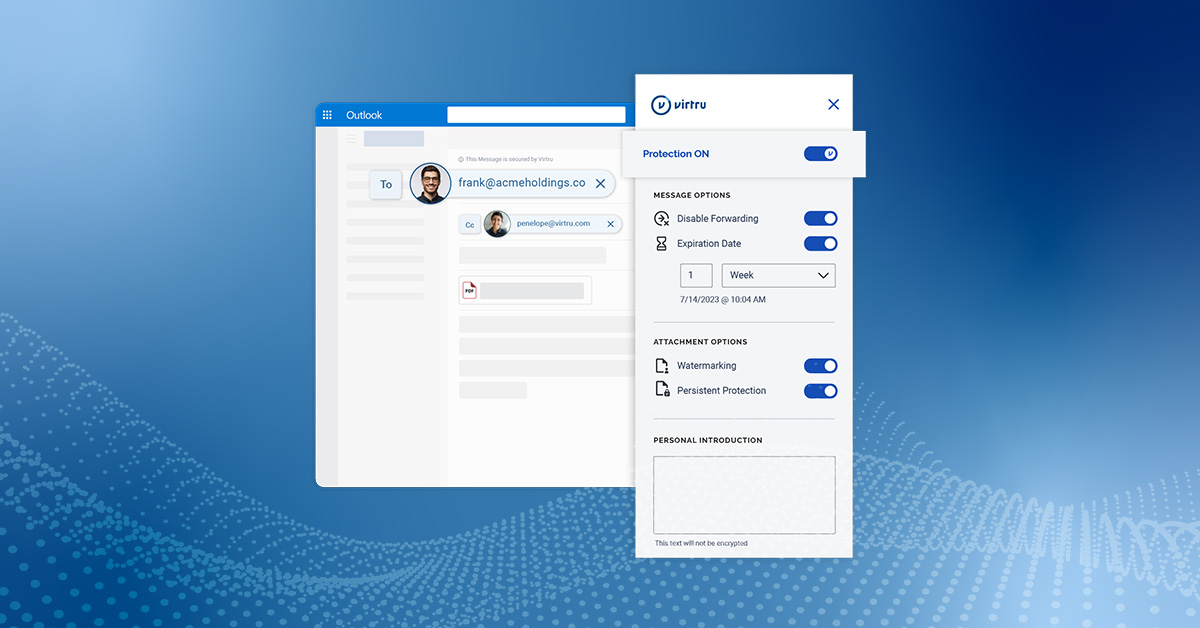
Virtru for Outlook
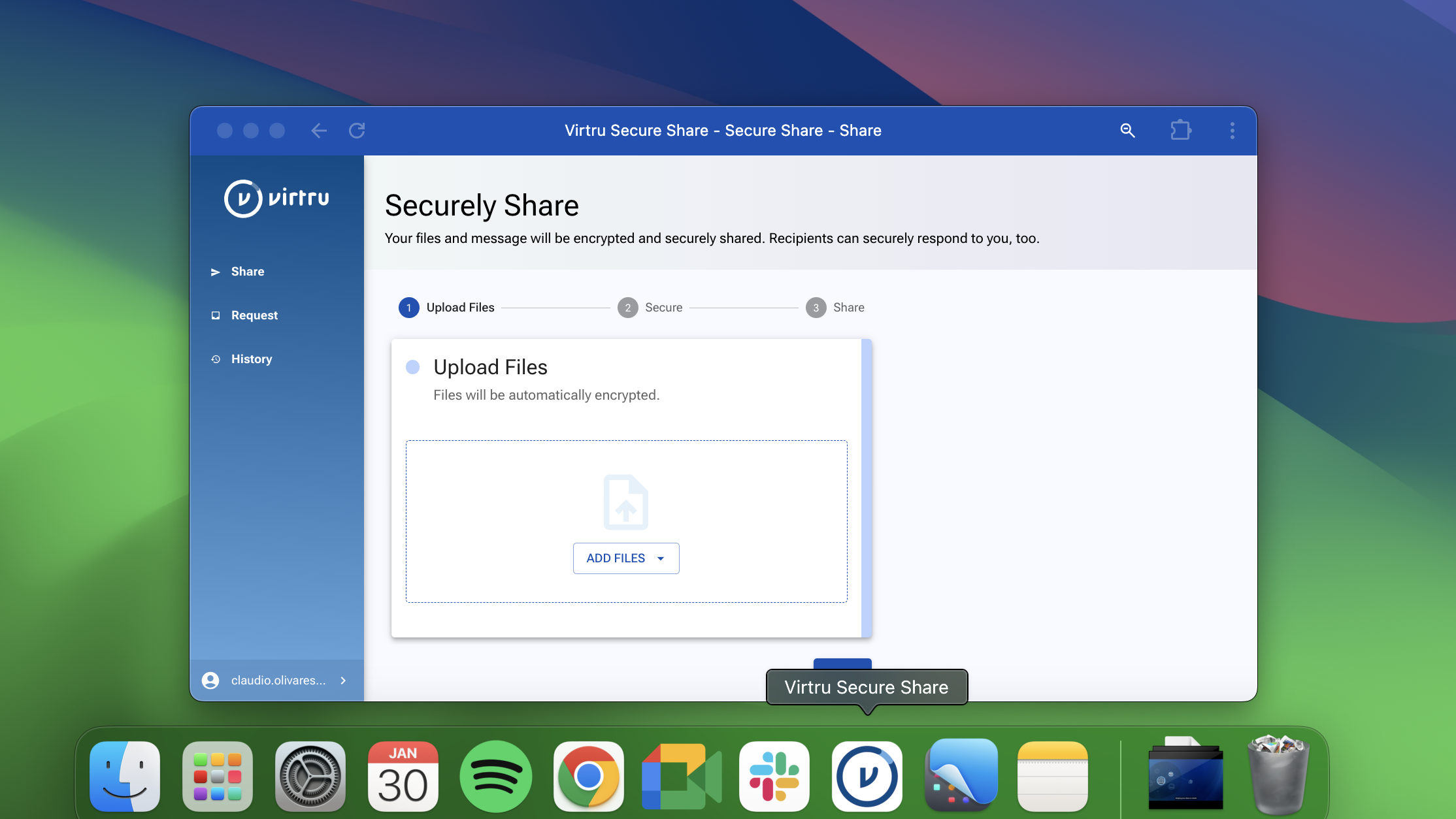
Virtru Secure Share
CMMC/NIST/DFARS
When Data Must Move: How to Share CUI Outside Microsoft GCC High

Virtru Secure Share
CMMC/NIST/DFARS
Microsoft 365 Business Premium for GCC High: Pros and Cons for CMMC

Virtru Private Keystore
HIPAA
Healthcare
Virtru for Google Workspace
Virtru for MSFT 365
/blog%20-%20title%2048%20november%2010/cmmcnov10.webp)
/blog%20-%20ukraine%20and%20taiwan%20HIO%20recap/UkraineTaiwanRecapBlog.webp)

/blog%20-%20HIO%20Maya%20HTT/Maya-HTT-Level-2-lessons%20copy.webp)

/blog%20-%20cmmc%20level%203/CMMC-LEVEL-3.webp)

/blog%20-%207%20Healthcare%20Vulnerabilities/7-hipaa-vulns.webp)
/blog%20-%20please%20delete%20that%20email.%20domain%20wide%20protection/please-delete-that-email.webp)
/blog%20-%20next%20breakfast/next-breakfast-2.png)
/blog%20-%20microsoft%20bitlocker/microsoft-bitlocker.webp)




/blog%20-%20EEOC/EEOC.webp)

/blog%20-%20marquis%20exploit/Marquise-Zero-Day.webp)
/blog%20-%20the%20data%20layer/geode.webp)

/blog%20-%20From%20Zero%20Trust%20Principles%20to%20Practice/dcs-principles.webp)

/blog%20-%20Zero%20Trust%20Primer%20-%20N5K%20series/Zero-Trust-Primer%20copy.webp)
/blog%20-%20Private%20Cloud%20Compute%20is%20Only%20Half%20the%20Story/PrivateCloudCompute.png)



/blog%20-%20data%20liberation/data-liberation-2.jpg)
/blog%20-%20ACP-240%20and%20HIGHMAST/highmast-acp-240.webp)

/blog%20-%20discord-zendesk%20breach/discord-breach.webp)
/blog%20-%20Fortra%20Zero-Day%20Exploit/fortra-goanywhere-vulnerability.webp)

/blog%20-%20Save%20Secure%20Share%20Protected%20Files%20Directly%20to%20Google%20Drive%20and%20Microsoft/csecure-share-cloud-save-blog.jpg)


/blog%20-%20nov%2010%20cmmc/cmmc-nov-10-FINAL.webp)

/blog.%20-%20The%20Wait%20Is%20Over%20as%20CMMC%20Moves%20from%20Proposal%20to%20Reality/cmmc-in-final-review.webp)


/blog%20-%20Apple%20vs%20UK%20update/applevUKupdate.webp)


/doctor-patient-phi-01.webp)
/title48-to-OIRA.webp)
/blog%20-%20CyberArk%20and%20Palo%20Alto/CyberArk-PaloAlto-Acquisition%20copy.webp)

/blog%20-%20Secure%20Share%20for%20MS%20Teams/Secure-Share-for-teams-blog.webp)

/blog%20-%20microsoft-pentagon%20digital%20escort/dod-digital-escort-blog%20copy.webp)
/blog%20-%20series%20D%20funding/25-Funding-Commentary.jpg)

/blog%20-%20congress%20bans%20whatsapp/congress-whatsapp-ban.webp)


/blog%20-%20Washington%20Post%20Breach/wapo-breach-blog.webp)
/blog%20-%20What%20a%20Marines%20Email%20Fame%20Teaches%20Us%20About%20Modern%20Data%20Security/email%20snafu%20marines.jpg)

/blog%20-%20educause%202025%20roundup/educause-panel-blog.webp)
/blog%20-%20HIPAA%20Breach%20Response%20How%20to%20Prevent,%20Mitigate,%20or%20Resolve%20Leaked%20PHI/revoke-HIPAA.webp)
/blog%20-%20varonis%20fedramp/fedramp-blog-varonis.webp)
/blog%20-%20Why%20Investors%20Are%20Pouring%20Billions%20Into%20Protecting%20What%20Matters%20Most/billion-dollar-investment.webp)
/blog%20-%20ABAC%20101/ABAC-101.webp)
/blog%20-%20inbound%20encryption/inbound-encryption-blog.webp)

/blog%20-%20saving%20billions%20and%20securing%20america/billionsinsavings.webp)
/blog%20-%20Varonis/Varonis.webp)


/blog%20-%20white%20house%20google%20drive/GSA-google-drive.webp)
/blog%20-%20The%20CMMC%20Assessment%20Gamble%20Why%20Assess%20First,%20Fix%20Later%20Is%20a%20Risky%20Strategy/cmmc-fail-risky-strategy.webp)

/blog%20-%20case%20against%20florida%20backdoor%20bill/case-against-florida-backdoor-bill%20copy.webp)

/blog%20-%20Simplify%20the%20Recipient%20View%20Security%20Control%20Customization%20for%20Virtru%20Email/custom-recipient-security-options_FINAL.webp)
/blog%20-%20When%20Regulators%20Become%20Targets%20The%20Treasury%20Email%20Breach/treasury-occ-breach.webp)
/blog%20-%20data%20lakehouse/data-lake-house.webp)

/blog%20-%20What%20Frank%20Slootmans%20Move%20to%20Cyera%20Means%20for%20DataCentric%20Security/cyera-board-blog.jpg)
/blog%20-%20march-25%20executive%20order/March-25-executive-order.webp)




/blog%20-%20encrypted%20search/encrypted-search-blog.webp)
/DIB-Fedramp-Authorized-Software.webp)
/17-state-gov-virtru.webp)
/TLS-E2EE-Truck.webp)

/blog%20-%20How%20Universities%20Can%20Still%20Meet%20CMMC%202.0%20Requirements%20Despite%20the%20NIH%20Budget%20Cut/cmmc-r1-university-budget-cuts.webp)
/blog%20-%20A%20Call%20to%20Accelerate%20Zero%20Trust%20Adoption%20and%20Strengthen%20Our%20National%20Cyber%20Resilience/Accelerate-zero-trust-adoption.webp)

/blog%20-%20pexip%20recap/pexip-HIO-recap.webp)
/blog%20-%20TDF%20vs%20TLS%20encryption/tdfvstlsencryption.webp)
/blog%20-%20Zero%20Trust%20Data%20Format%20ZTDF%20The%20Clear%20Path%20to%20Data%20Interoperability/zero-trust-data-format-interoperability.webp)
/blog%20-%20apple/apple-no-backdoors-no-adp-blog.webp)
/blog%20-%20secure%20share%20for%20onedrive%20and%20sharepoint/onedrive-sharepoint-blog.webp)

/Blog%20-%20Maximizing%20CMMC%202.0%20Compliance%20How%20Virtru%20Enhances%20Google%20Workspace%20Security%20+%20Protects%20CUI/google-workspace-CMMC.webp)

/man-looking-out-window.webp)
/blog-%20hotchkiss,%20kent,%20success%20academies%20recap%20blog/HOTCHKISS-KENT-SUCCESS-ACADEMIES-RECAP-BLOG.webp)




/blog%20-%20excited%20for%202025/excited-for-2025.webp)
/blog%20-%20eo%20on%20encryption/white-hosue-EO.jpg)
/jen%20easterly%20and%20salt%20typhoon.webp)
/blog-Virtru%20and%20anduril/Anduril-and-Virtru.webp)

/blog%20-%20Open%20Technology,%20Standards,%20and%20Commercial%20Innovation/Open%20Technology%2c%20Standards%2c%20and%20Commercial%20Innovation-%20US%20DoD%E2%80%99s%20Fastest%20Path%20to%20Zero%20Trust%20Controls%20and%20Data%20Centric%20Security.webp)
/blog%20-%20Beyond%20Compliance%20Theater/compliance-theater.webp)
/bridge-malmo-copenhagen.webp)

/blog-atx%20defense%20recap/atx-defense-webinar-recap.webp)
/fbi-encryption.webp)
/Crowd%20Silhouettes.jpg)
/blog%20-%20DOD%20and%20Virtru%20leadership/dod-and-virtru.webp)
/blog%20-%20HIM/HIM-blog.webp)

/blog%20-%20hipaa%2030%20to%2015/HIPAA-timeline.webp)


/blog%20-%20boise%20and%20nc%20state/boise-state-and-nc-state.webp)
/cmmc%20engineering%20project.webp)
/rising-tide-wave.webp)
/Threat%20Intel%20Storm%20Chaser.webp)

/data%20liquid.webp)

/office-windows.webp)
/CMMC%20Quick%20Start%20Guide.webp)
/smime-rust.webp)
/cmmc2-dcs.webp)


/Starboard-Gaffe.webp)
/VIRTRU-TEAM.webp)
/backdoor-FINAL.webp)
/water-treatment-plant.webp)
/Backdoor%20Blog.webp)
/Zero%20Trust%20Fast%20Z.webp)
/blog%20-%20cybersecurity%20awareness%20month%202024/cyber-awareness-month-blog.webp)
/blog%20-%20two-perspectives/data-security-two-worlds.webp)

/blog%20-%20proofpoint%20eol%20october%201/oct-1-proofpoint-eol.webp)
/Twitter%20Elon%20Email.webp)
/24-blog-3-reasons-SS-Drive.webp)
/Wave-Perimeter.webp)

/blog%20-%20leave%20the%20antiquities%20to%20academia/academia.webp)
/georgia-tech.webp)


/blog-cmmc-august-2024/cmmc-2-august-update_FINAL.webp)
/blog%20-%20kiteworks%20valuation/kiteworks-blog%20copy.webp)
/Blog%20-%20FCA/dc-capitol-skyline.webp)
/JADC2%20Exercises.webp)


/summer-camp%20copy.webp)

/blog-echospoofing/echo-spoofing.jpg)


/gemini%20ai%20sharing%20blog.webp)
/Virtru%20Secure%20Share/Secure%20Share%20Interface%20Blog.webp)
/Google%20Drive%20Secure%20Share.webp)
/ATT%20Snowflake%20Breach%20CISO.webp)
/blog%20-%20nato%20+%20virtru/nato-virtru%20copy.webp)
.jpg)

/blog-%20june%202024%20progress%20moveit/Commentary.webp)
/blog%20-%20stone%20age%20IT/Opinion.jpg)
/Gmail%20Confidential%20Mode.webp)






/Virtru%20Watermarking%20Outlook.webp)
/cui-data-contractor-01.webp)



/blog-software%20companies%20turn%20to%20virtru/softwarecompany.webp)
/blog-dell%20breach/virtru-for-zendesk.webp)

/blog%20-%20file%20encryption%20pillar/file-encryption-pillar.webp)

/Tucson-City-Hall-01.webp)

/Fedramp%20CMMC%20Dfars.webp)
/Google%20Drive%20Custom%20Labels.webp)
/men-coats-coffee-talking-01.webp)
/blog%20-%20versatile%20TDF/Versatile%20TDF%20Blog.webp)
/blog%20-%20how%20smime%20works/aerial-view-office-couch-01.webp)
/Blog%20-%20ZTDF%20The%20Quiet%20Revolution/zero-trust-data-format.webp)
/blog-%20cse%20for%20gmail/it-manager-purple-01.webp)
/blog%20-%20what%20is%20pgp%20encryption/matroshka-nesting-doll-01.webp)

/blog%20-%20email%20encryption/woman-standing-with-laptop-01.webp)
/blog%20-%20hidden%20costs%20of%20email%20portal/Business-meeting-it-finance-01.webp)
/blog%20-%20Granular%20Access%20Control%20Bridging%20the%20Gap%20in%20Google%20Workspace%20CSE/Google-cse-label-based-controls-blog.jpg)
/blog%20-%20GCP%20commit/Woman-Working-Green-Window.webp)

/blog%20-%20g2%20best%20software%20award/Virtru%20Best%20Software%20G2%202024.webp)
/blog-%20whiskey/whiskey.webp)
/blog%20-%20New%20Partnership%20Brings%20Best-in-Class%20Data%20Security%20to%20Google%20Cloud/23-VirtruGoogle-V1%20BLOG.jpg)
/blog%20-%20a%20day%20in%20the%20life%2066Degrees/healthcare-data-security.webp)
/indopacom.jpg)




































.jpg)


















.jpg)