Email Encryption: Everything You Need to Know


The business world runs on email. It's our primary method of communication, both internally and externally, which makes it both a necessity and a risk to manage. Because we share information via email — some of it sensitive — it's important to ensure that information remains protected, secure, and compliant.
This is why email encryption is a vital part of any organization's data security posture. In this post, we'll define email encryption, explain how to encrypt email, and outline the things to look for in the best email encryption software. We'll also cover some of the most common compliance regulations that require encryption.
What is an encrypted email?
An encrypted email is an email with added protection to prevent unintended recipients from viewing it. Most email clients provide at least a basic level of encryption by default, known as TLS (Transport Layer Security), which protects email in transit between the sender's email server and the recipient's email server.
End-to-end encryption (E2EE), however, is a stronger standard for email encryption. End-to-end encryption spans the full life cycle of the data, from the moment the sender creates it to the moment it's accessed by the intended recipient, extending the security of the data. For the most robust end-to-end encryption, you need client-side encryption tools like the Virtru email encryption plugins for Gmail and Outlook, or a capability like Google Client-Side Encryption in conjunction with a key management partner. More on that later.
Finally, there's another form of email encryption called server-side encryption. This protects emails after they've been created, but before they've left your server. This is how the Virtru Data Protection Gateway works: It automatically detects emails on their way out and protects them with encryption before they leave. The user doesn't have to do anything at all, and the gateway does all the work for you.
Recommended Reading: The Basics of Email Encryption
- Privacy is not a crime: Why email encryption is important. Written back in Virtru's early days in 2015, this post highlights why we should care about email encryption from a privacy perspective.
- End-to-end encryption, explained. Here's your opportunity to dig into the differences between TLS and end-to-end encryption methods.
- The struggle is real: Overcoming email encryption difficulties. Email encryption is often hard, but it doesn't have to be. This post highlights how you can make encryption easier.
How to Encrypt an Email: 4 Ways
Beyond your native TLS encryption, there are several ways to go about encrypting an email.
Option 1 (Preferred): Choose an Easy Encryption Provider that Integrates with Existing Processes
This is the simplest option for encrypting email: Choosing a tool that can layer into your email provider to encrypt sensitive information when and where you need it. This is what Virtru provides, in two different "flavors" that can be implemented standalone or together:
Virtru Client-Side Encryption for Gmail and Outlook
Deployed as a simple Chrome Plugin for Gmail and an Add-On for Microsoft Outlook, Virtru provides users with an intuitive option right within their email interface that they simply toggle "on" to protect emails and attachments. This also gives you granular access controls that can be changed any time, letting you revoke an email, change permissions, or set an expiration date — even after the encrypted email has left your organization.
Recommended Reading: The Definitive Guide to Gmail Encryption | How to Encrypt Email in Microsoft Outlook | Do I Need Email Encryption Software?
Virtru Server-Side Encryption for Gmail, Outlook, and SaaS Apps
Deployed as an email gateway, the Virtru Data Protection Gateway runs automatically in the background, invisible to the user. Depending on the path your administrators want to take, you can set up DLP keywords to detect and encrypt sensitive information before it leaves your organization.
Recommended Reading: The Email Gateway: A Swiss Army Knife for Automated Encryption | "It's Been a Game Changer for Us" - Why a Global Research University Deployed Virtru Domain-Wide
Option 2: Choose a Manual Method of Email Encryption, like PGP or S/MIME
Methods like PGP and S/MIME require some up-front effort, both for administrators and for users. PGP email encryption requires you to generate your own encryption keys, and also requires both sender and recipient to have PGP installed in order to exchange public and private keys. S/MIME email encryption requires you to purchase certificates for each of your users. Both of these methods can become unwieldy if your company grows or changes users frequently, and both require substantial intervention if keys or certificates are lost or compromised. More on these methods of encryption, and how to use them, can be found in our blog post, How to Encrypt an Email — The Easy Way and the Hard Way. (Spoiler alert: PGP and SMIME are the hard way.)
Recommended Reading: The Hard Part About Email Encryption Is Decryption: Here's Why | Google Client-Side Encryption for Workspace: Privacy-Enhanced Cloud Collaboration in Partnership with Virtru
Option 3: Choose a Portal-Based Encryption Provider
There are several portal-based encryption providers out there that provide email encryption through a portal, where users and recipients log in to access secure information that's been shared with them. A lot of companies still use portal-based encryption, but the user experience is often lacking — both for internal users and external recipients, who do not want to navigate away from their existing processes or create yet another password that they will ultimately forget. Furthermore, it becomes a headache for administrators, especially with portal providers that put encrypted emails into separate mailboxes. Add this to the increased support ticket volume from cumbersome UX, and your IT teams will probably become frustrated and overworked.
Recommended Reading: The Hidden Costs of Your Secure Email Portal
Option 4: Consolidate With Other Solutions — and Pay For It
Another option for encrypted email is to explore offerings from other providers in your tech stack — but be aware that these solutions could cost you, either in outright cost or in user experience and productivity.
One example is the Microsoft GCC High package, which is a powerful but costly path to advanced email encryption and access control. Upgrading to the expensive high-side package could be an option for you, but know that you're paying more and also consolidating your risk area with a single provider. (One Virtru customer chose to stay on the Microsoft Commercial Cloud package with Virtru email encryption for Outlook as a GCC High alternative — and he saved over $1 million.)
Then you have other providers in your tech stack that specialize in business email compromise (BEC) and anti-phishing/anti-malware — companies like Proofpoint or Mimecast. They may include email encryption as an element of their package, but it's certainly not their focus, and this is often clear in the UX of the product. You don't want email encryption to be an afterthought, and you don't want to introduce clunky processes that your employees are just going to avoid and circumvent anyway.
For example, here's what Proofpoint's user experience looks like for email encryption.
Recommended Reading: Global Engineering Firm Saves $1M by Selecting Virtru Over Microsoft Office GCC High for CMMC 2.0 and ITAR | Trustworthy UX: How to Add Custom Branding to Encrypted Email
The Fastest Email Encryption
The quickest way to encrypt an email is to choose a provider that you can deploy quickly and easily, even if your organization has a lot of employees. Virtru's client-side email encryption for Gmail and Outlook, and our server-side email encryption Gateway, can be deployed in minutes, not days or weeks, and you don't have to go through cumbersome setup and training exercises. The icing on the cake? Virtru is so intuitive and built right into your email experience, that you will hardly have to spend any time training your users on it. We do recommend letting them know about Virtru, but once they are set up, there's not much for admins to worry about.
(In a hurry to deploy email encryption? Contact us, and our team can set you up with Virtru licenses quickly!)
How to Open an Encrypted Email
We've talked a lot about how to send encrypted emails, but what about the recipient? How do they read an encrypted email? Well, depending on your chosen method of encryption above (options 1-4), the recipient experience looks a little different.
How to Open a Virtru Encrypted Email
Virtru makes it easy to open an encrypted email.
- Click the "Unlock Message" button in the email.
- Verify your identity by logging in with your Outlook or Gmail credentials, or a one-time emailed code.
- View the email and any attachments, and reply securely.
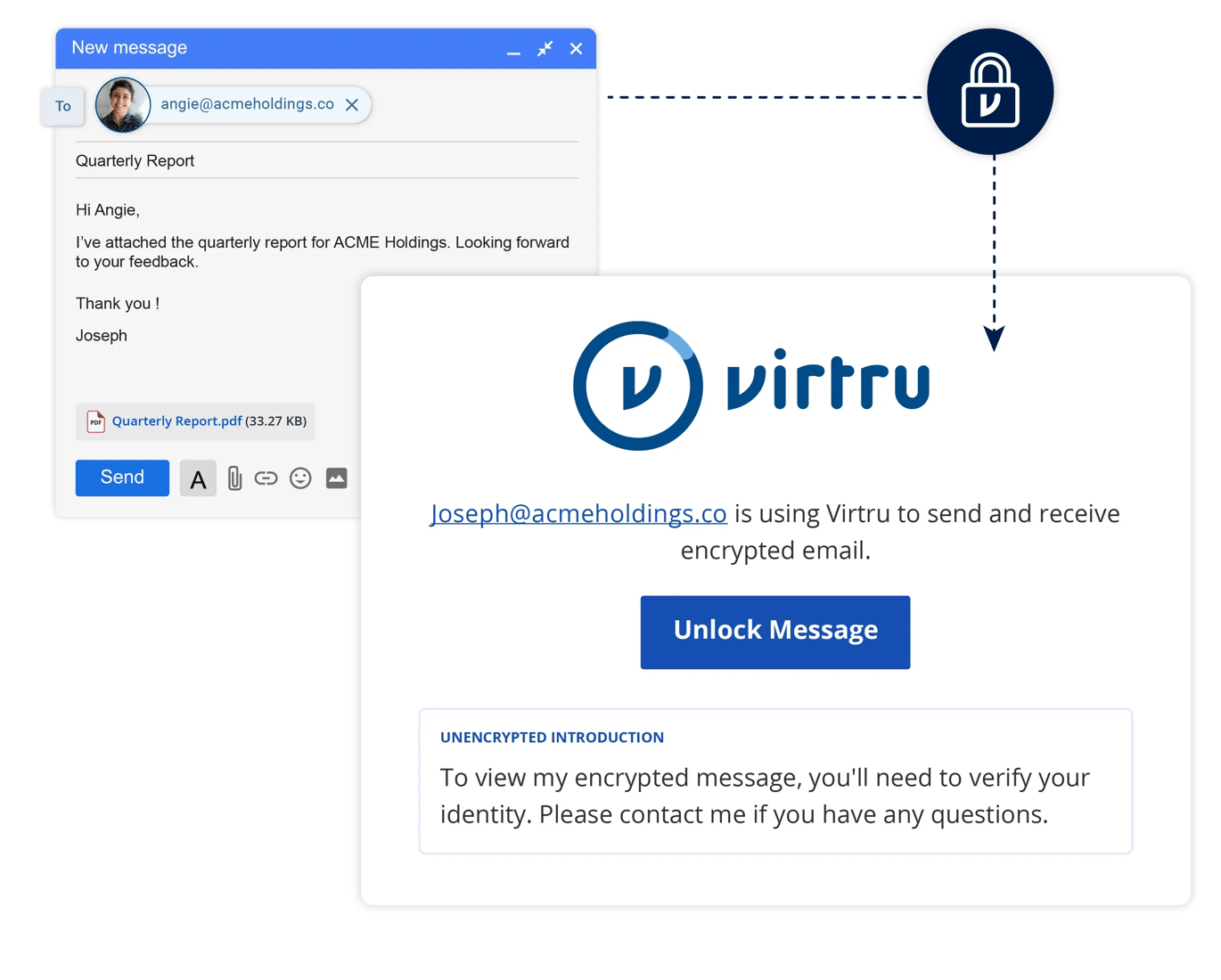
All you have to do is click on the "Unlock Message" button in your Virtru-protected email and log in with your existing Gmail or Microsoft credentials: No new passwords, no software to install. Just authenticate to confirm that you are, indeed, the intended recipient, and you can view the email and any attachments in your browser.
How to Open a PGP Encrypted Email
To open a PGP email, you'll need to have PGP installed so that you can enter your private passkey. Once you enter your passkey to authenticate, you'll be able to view the email.
How to Open a S/MIME Encrypted Email
If your email client supports S/MIME encryption, you can't exchange encrypted email right away. First, you must exchange a "signed" email to establish a secure connection – and this requires that both sender and recipient are well-versed in S/MIME and know what to look for in order to set up this secure connection. Once that is done, those two parties can securely exchange information. It's important to note that this process (outlined in this blog post) must be repeated with every new contact who is receiving encrypted email.
How to Choose Encrypted Email Providers
There are a lot of encrypted email providers out there — some good, some clunky, some terribly outdated — so you'll want to sift through the options to choose the best one for your organization. Here are some things to look for:
Easy Email Encryption Experience
Is the experience easy for everyone who will be encountering it? (This includes your internal users, your administrators, and the external recipients who will be opening the encrypted emails.) You want an email encryption provider that makes the experience easy. This also helps ensure your chosen solution will be widely adopted, and it won't create headaches for your IT support team.
Key Management Options for Compliance
If your organization has advanced data security requirements (think compliance regulations like ITAR, CMMC, DFARS, GLBA, CJIS, and others) you want to explore their encryption key management options: Do they allow you to host your own encryption keys, whether on-prem with a hardware security module (HSM) or in a public or private cloud? Make sure you're able to take control of your encryption keys.
Read Encrypted Email Provider Reviews
Check trusted software review websites like G2, Capterra, and Gartner Peer Insights to see what users are saying. You want to select a vendor that customers trust and are happy with (and, ideally, has won some best software awards). A library of customer stories that highlight use cases and testimonials can also be helpful.
Solve More Problems than Email Encryption
Does your email encryption provider also provide additional coverage for your organization? Think secure file transfer, large file management, and SaaS app security integrations for your other business applications like Salesforce and Zendesk? Explore their other solutions to see if your email encryption solution can scale with you, protecting your current and future data security needs.
Email Encryption for Compliance
Many industries (and geographic locations) require businesses to meet certain data protection standards to remain compliant. Email encryption is often a requirement to support these regulations, as it demonstrates advanced data protection for information both at rest and in motion. Here are a few examples of compliance regulations that highlight the need for encryption.
CMMC 2.0 Encryption Requirements
Let's jump right into the deep end: CMMC 2.0 is one of the world's strictest security standards, and it's a requirement for organizations contracting with the Department of Defense. These organizations can run the gamut from defense contractors to R1 research universities participating in government research initiatives.
There are 110 total controls that organizations need to meet in order to be compliant with CMMC. Several of these controls are related to encryption and fall under access control; audit and accountability; identification and authentication; media protection; and systems and communications protection. Ultimately, these protections are intended to protect controlled unclassified information (CUI).
Some examples of CMMC Level 2 email encryption requirements are:
- Practice ID AC.L2-3.1.19: Encrypt CUI on mobile devices and mobile computing platforms.
- Practice ID IA.L2-3.5.10: Store and transmit only cryptographically-protected passwords.
- Practice ID MP.L2-2.8.6: Implement cryptographic mechanisms to protect the confidentiality of CUI stored on digital media during transport unless otherwise protected by alternative physical safeguards.
- Practice ID SC.L2-3.13.8: Implement cryptographic mechanisms to prevent unauthorized disclosure of CUI during transmission unless otherwise protected by alternative physical safeguards.
- Practice ID SC.L2-3.13.10: Establish and manage cryptographic keys for cryptography employed in organizational systems.
- Practice ID SC.L2-3.13.11: Employ FIPS-validated cryptography when used to protect the confidentiality of CUI.
Virtru helps organizations address 27 of the 110 CMMC Level 2 controls with encryption and granular access control.
ITAR Encryption Requirements
International Traffic in Arms Regulations (ITAR) compliance is intended to regulate U.S. military technology and keep it within the U.S. The ITAR "encryption carve-out" rule states:
Cryptographic protection must be applied prior to data being sent outside of the originator’s security boundary and remain undisturbed until it arrives within the security boundary of the intended recipient. This means encrypting data prior to emailing or sharing it.
Encryption must be certified by the U.S. National Institute for Standards and Technology (NIST) as compliant with the Federal Information Processing Standards Publication 140-2 (FIPS 140-2), or meet or exceed a 128-bit security strength.
Information that can be used to decrypt (access) the technical data may not be shared with a third party (such as a cloud or email provider).
ITAR therefore requires that an organization's encryption keys must be hosted by the data owner in a location that is not accessible to their cloud or email provider. This is where the Virtru Private Keystore adds tremendous value: Virtru allows self-hosted encyrption keys, so customers can store them in a public or private cloud, or on premise. As one Virtru customer, Laurent Muller, of Exxelia, said in an ITAR case study, "Our biggest priority when it comes to compliance is ITAR, especially because we are international. That means that everything we do in the United States has to stay in the United States... We are not allowed to have any piece of information leaving the country — even electronically. Virtru helps us make sure that we keep emails containing confidential information properly encrypted and properly safe”
CJIS Encryption Requirements
Criminal Justice Information Services (CJIS) is an entity that aggregates criminal justice information (CJI) from law enforcement organizations around the U.S. into searchable databases. CJIS compliance is required by any organization accessing this information, designed to ensure the gathered information remains protected.
CJIS encryption requirements include:
- Section 5.10.1.2.1: When CJI is transmitted outside the boundary of the physically secure location, the data shall be immediately protected via encryption that is FIPS 140-2 certified.
- Section 5.10.1.2.2: When CJI is at rest (i.e. stored digitally) outside the boundary of the physically secure location, the data shall be protected via encryption with the same standard mentioned above or use a symmetric cipher that is FIPS 197 certified (AES) and at least 256-bit strength.
Law enforcement agencies, as well as state and local government organizations, use Virtru to support CJIS compliance. In one CJIS case study, Jesus Rodriguez, IT Application Developer for Hidalgo County, Texas, said, "CJIS compliance standards require that inbound email containing criminal justice information (CJI) be encrypted at all times. To meet these requirements, we initially turned to Virtru to secure our Gmail messages and attachments containing CJI. Fast forward a few years and we were working on new custom app scripts that would access our information system, auto-generate a report, and email it to certain individuals. To make this new method of delivering reports CJIS compliant, we needed to build encryption into the workflow. We quickly realized there was an opportunity to leverage the same encryption technology from Virtru that we depend on within Gmail, but in our own custom workflows.”
FTC Safeguards Encryption Requirements
Part of the Gramm-Leach Bliley Act (GLBA), the FTC Safeguards Rule requires heightened security to protect customers' data. Rule 314.4 (c) (3) states: "In order to develop, implement, and maintain your information security program, you shall... Protect by encryption all customer information held or transmitted by you both in transit over external networks and at rest." This rule applies to a wide variety of financial institutions defined by the FTC, including auto dealerships, mortgage lenders, financial advisors and tax preparation firms, and even organizations like travel agencies.
When the FTC Safeguards Rule went into effect in 2023, many organizations had to act quickly to deploy the required encryption. Many organizations chose Virtru because it's the easiest software on the market. Take, for example, TrueCar's FTC Safeguards case study: Senior Security Engineer Brett Henry noted that Virtru's ease of use was an essential part of his encryption provider decision. "To have a tool like Virtru that we could roll out ourselves, that didn’t require a lot of work to put it in the hands of our users, was an advantage. These are people-people. They’re not engineers or developers.” Henry wanted to give them simple tools to get the job done — while protecting sensitive data — as easily as possible.
Encryption for HIPAA Compliance Standards
HIPAA recommends that healthcare practices incorporate data protection standards to safeguard protected health information (PHI). Email encryption provides an auditable, secure way to share patient records and paperwork — both with patients, insurance providers, and other physicians' offices — while ensuring PHI remains protected according to HIPAA security requirements.
Many healthcare practices leverage Virtru to protect the patient files that inevitably need to be shared externally. Virtru's advantage here is that it's easy for patients to use, as well — even if they aren't particularly tech savvy.
According to one HIPAA email encryption review on G2, “With Virtru, we are solving the issue of email security when sending patient information to physicians or offices. Working in healthcare, we must follow HIPAA guidelines and be sure to send patient information in a secure manner. Virtru allows me to feel safe when sending patient information because I know the information is encrypted.”
Encryption for FERPA, New York Ed Law 2-D, and Other State-Level Education Requirements
Schools are responsible for a wide variety of student data, and many state-level data privacy regulations are being established to protect student privacy. From FERPA compliance to Ed Law 2-D in New York, email encryption protects a wide variety of student data, including:
- Student PII (contact information, social security number, address, family contact information)
- Health records subject to HIPAA (e.g., vaccination records)
- Individualized education plans (IEPs)
- Student transcripts
- School security footage
For many school districts, it's important to find a budget-friendly encryption tool that will support these requirements and protect student data, without breaking the bank. This was the case for Newfield Central School District in New York, who chose Virtru. "We did not think that we would be able to afford encryption for the district,” said Sunshine Miller, Director of Technology for the district. “But Virtru has been great for us. I am so happy that we've actually been able to afford encryption — and that we've been able to afford it for the whole district. It's very rare that a company gives you the full product, at a reasonable price that a school district like ours can afford.”
Discover the Benefits of Email Encryption for Your Organization
Email encryption is one of the best investments you can make for your business. In a landscape where so much security investment is focused on the data you possess internally, it's vital to also prioritize the data that is inevitably leaving your business because it needs to be shared. When that information is shared externally, you'll have peace of mind knowing it still remains under your control at all times.
Ready to take the next step with email encryption? It's remarkably easy. Contact Virtru's team of email encryption experts to get started.

Megan Leader
Megan is the Director of Brand and Content at Virtru. With a background in journalism and editorial content, she loves telling good stories and making complex subjects approachable. Over the past 15 years, her career has followed her curiosity — from the travel industry, to payments technology, to cybersecurity.
View more posts by Megan LeaderSee Virtru In Action
Sign Up for the Virtru Newsletter
/blog%20-%20metadata%20on%20data/metadata-on-data.webp)

/blog%20-%20Ravenna%20Hub/ravenna-hub.webp)




/blog%20-%20HIO%20Maya%20HTT/Maya-HTT-Level-2-lessons%20copy.webp)

/blog%20-%20cmmc%20level%203/CMMC-LEVEL-3.webp)
