The Struggle is Real: Overcoming Email Encryption Difficulties


Encryption. It’s an age-old solution used to conceal our most sensitive information from unwelcome eyes as it travels, and even while in our possession. When email came around, there was a quick realization that we need to encrypt our digital messages, too.
But if email encryption is the obvious security solution in our modern age, why is everything about it so difficult? Or, why do we think it’s so difficult?
Franklin Veaux sums it up well on Quora: "Right now, it’s a huge pain in the ass. It’s clumsy, it’s clunky, it’s anything but transparent, and most users have no idea how to do it, or what to do with an encrypted email.” Despite our growing need for it, many users still struggle with the concept due to its perceived complexity and difficulty — on top of the technical difficulties that cryptographers face daily.
We saw it with the initial apprehension around computers in the '80s, cell phones in the early '00s, and two-factor authentication in the '10s. But once all of these things became more accessible, affordable, understood, and easier to use, they slowly — then all at once — integrated into our daily lives.
In this blog, we’ll go into detail about why email encryption is so important, why it’s so difficult, and how we can overcome those difficulties.
What's email encryption?
Why is email encryption necessary?
Why is email encryption hard?
How can email encryption be made easier?
Easy, fast, and secure email encryption
Conclusion
What’s Email Encryption?
Email encryption is the process of scrambling the contents of an email to conceal it as it travels or is stored. Only the intended recipient, the person with the encryption key, has the ability to decrypt the email and access the data within.
Email encryption typically uses public key cryptography, which is accomplished through a combination of public and private keys, both generated by the sender. The sender uses a public key to encrypt the message, and the receiver uses the private key to decrypt it. Khan Academy uses the analogy of a mailbox. Anyone can access the deposit slot and submit a letter. But only the intended recipient of the mail will have the key to open the mailbox and receive the mail.
There are two primary categories of email encryption: transport-layer security (TLS) and end-to-end (E2E) encryption. Transport-layer security encrypts and protects the email as it’s transmitted from the sender to the receiver, but end-to-end encryption is encrypted both while in transit and while the data is at rest before and after it’s sent. E2E is the more secure category of email encryption.
Why Is Email Encryption Necessary?
Take a day to analyze the info you share through email. Would you broadcast any of it to the rest of the world? Emails typically contain sensitive data like business strategies, personal information, access credentials, files, or finances. With this information on a wider scale, hackers can wreak havoc on finances, reputations, infrastructures, and even national safety.
You can probably recall a few major email hacks—like the DNC's 2016 email leak, Microsoft’s 2022 email server hack, Sony’s 2014 data breach, Uber’s 2022 social engineering hack that exposed emails, and many more. All attacks played out with major financial, political, and emotional consequences on not only the immediate targets, but also their customers or constituents. In addition to high-profile data breaches, small businesses, individuals, and even K-12 schools are becoming increased targets, and more data is at risk.
According to Statista, the third quarter of 2022 saw approximately 15 million data records exposed worldwide through data breaches, a 37 percent increase from the previous quarter. The initial loss of data is just half the story: Data breaches are pricey to clean up. The average cost of a data breach is $4.35 million globally, and that figure is nearly double for businesses in the U.S. — $9.44 million, according to IBM.
Email encryption directly combats these consequences — particularly end-to-end encrypted email. Email encryption protects the data within your email so that even if a hacker is able to obtain possession of it, they don’t have the keys to decrypt and access the data. It’s a proven solution that governments and industries at large are taking note of.
American regulations like HIPAA, ITAR, CMMC, FTC Safeguards, and more mandate encryption for sensitive information both at rest and in transit. Regulations in Europe like General Data Protection Regulation (GDPR) do the same—while not explicitly mandating email encryption, it’s regarded as an industry-standard method of protecting sensitive information exchanged in emails.
Why is Email Encryption Hard?
So, we know that we have an overgrown need for email encryption—and there are many regulations in every industry that require the use of it. What makes it so hard?
One reason is that legacy, portal-based encryption providers have made the user experience painfully difficult. This is because a seamless encryption and decryption experience is tough to get right.
Encrypting a message is relatively easy with the right setup. The hardest part of encryption is really decryption: making sure that the right people can easily decrypt the message, and making sure the wrong people cannot.
It's Complex On The Technical Side
From a CISO’s perspective, there are a lot of challenges with implementing encryption that go deeper than it mostly being hard to use.
1. Compatibility issues: Some methods of mail encryption require both the sender and recipient to use the same encryption technology, which can be a challenge when different email systems are used or when recipients have older software that doesn't support decryption.
Take S/MIME for example — this highly regarded dual encryption protocol requires an S/MIME certificate installed on both the sender and receivers’ sides. For businesses working frequently with external contractors, clients, or the everyday customer, this method of encryption may not be feasible.
2. Key management: Whoever has the keys to your data, has the ability to decrypt the emails you’ve protected. So in addition to encrypting the data itself, it’s vital to keep all public and privately generated keys in a safe place, away from hackers.
There are two primary ways to store encryption keys: through a cloud service provider (Google, Microsoft, or Amazon), or on an on-premises server. Storing encryption keys in the cloud is largely more convenient, user-friendly, and generally cheaper. But in many cases, it can present legal or compliance issues — particularly for businesses based in the EU, even if they're using a private cloud.
Say a France-based business is using Microsoft to store all of its encryption keys for encrypted Outlook messages, as well as all of the business' sensitive content. If the Microsoft server containing the French business’ keys and content is located on United States soil, it's therefore liable to subpoenas and warrants by the United States government. In the case of a blind subpoena, neither Microsoft nor the U.S. government has to notify the French business of the request for their data/keys — but still has the ability to access the data stored on the American-based server. This presents a challenge for the French company, as now their data could potentially be exposed to a foreign government.
So their options are to:
-
-
Use an on-premises server or private cloud within the country to store their keys (potentially with the support of a key management partner), or
-
-
-
Forego using Microsoft and find an in-country cloud provider to store their keys.
-
This leads us to our next technical challenge, which is infrastructure limitations.
3. Infrastructure limitations: Using an on-premises server to generate and store encryption keys requires time, money, and resources that many businesses don’t have. Or, using a small cloud provider instead of industry-standard platforms like Google or Microsoft could introduce hurdles to workflow and collaboration. This can be challenging for small businesses or organizations that don't have the resources to implement robust security measures—but still have growth and collaboration metrics that need to be met.
User Experience and Adoption of Email Encryption are Generally Poor
“Anytime you’re trying to get people to adopt new technology, the greater the ease of use, the greater the adoption,” says David Bowden, Zwift’s Vice President of Information Security, Data Privacy, Compliance, and IT. And it's true: People are busy trying to get their jobs done, and if their security tools are difficult to use — or will be difficult for their customers to use — they simply won't use them.
So many email encryption services are hard to use on the front end, making life difficult for the average end user. Portal-based encryption solutions require users to log in and out every time they want to receive an encrypted email. Some encryption services, like S/MIME and PGP, aren’t integrated into all operating systems and therefore are unable to exchange certain encrypted messages between sender and recipient.
Some even force the end users themselves to manage their public-private encryption key exchange workflows — PGP (Pretty Good Privacy) encryption is highly secure, but relies on an exchange of private keys that requires the user to store and manage their own keys individually.
Aside from the encryption protocols used, it’s all too common for email encryption providers to de-emphasize user interface and end-user experience. The product ultimately becomes useless, as frequent users have to travel outside of their Microsoft or Google tabs to decrypt and view messages. The workflow of encrypting and decrypting messages is complex with too many steps. All of these technicalities disrupt workflows and even inspire end users to look for insecure workarounds just to get the job done in a timely fashion.
Even in the presence of user-friendly email encryption, human error will sometimes prevail. Client-side encryption, meaning the sender activates the encryption of the message as opposed to automatically encrypting on the server side, could result in users forgetting to encrypt their message, exposing sensitive information by accident. Sometimes, ease of use can be so seamless that users can forget that it’s there; it’s possible for the receiver of an encrypted message to reply without encrypting — exposing details of the communication.
How Can Email Encryption and Decryption Be Made Easier?
There’s no shortage of challenges when it comes to email encryption and decryption — but it takes a certain shift in perspective that will make a true impact.
Adoption is Everything: Prioritize User Experience
Email encryption and decryption should be as easy as one or two clicks, without the hassle of extra logins, account creation, or questions of external compatibility. Too often, security tools are deployed without taking into account the daily life and workflows of employees on the ground.
If email encryption is hard to use, it’s a toss-up of what will be sacrificed first: productivity, or security. Investing in a solution that can make the front end as sleek as possible for both senders and receivers is the key to rapid, widespread adoption.
Consider External Collaboration
Methods like portal-based email encryption, S/MIME, only work when collaborators have the same infrastructure on both ends. Email encryption and decryption can be streamlined by adapting protocols to be more flexible in more environments. Solutions like allowing decryption through a browser and authenticating identity by verifying email can simplify the experience of secure, external collaboration in unfamiliar environments.
Shift to Data-Centricity
Before securing email servers, users, devices, platforms, apps, and networks, we need to remember what’s really being protected here: the data itself. When administrators are tasked with applying sweeping rules for email encryption, it limits the precision, collaboration, and productivity that email communications were created for. Tying access controls to the encrypted emails themselves can provide the nuanced, situation-specific control that users need to protect emails and keep collaboration moving.
Virtru Email Encryption: Easy, Fast, Secure
The solution to overcomplicated email encryption is a tool that doesn’t treat user experience as an afterthought and prioritizes data-centric security to allow end users more control than ever.
Integrated, User-Friendly UX
Virtru works like a plugin that integrates into your workflow, instead of uprooting it. All it takes is one click to encrypt your sensitive emails both at rest and in transit. For external receivers, decrypting an email is also easy; they don’t even need to have Virtru installed, nor do they need to create an account to decrypt. Recipients can decrypt Virtru emails through their browser, and authenticate their identity by verifying their existing email. Recipients can send encrypted replies through the Secure Reader in their browser, still without installing the Virtru plugin.
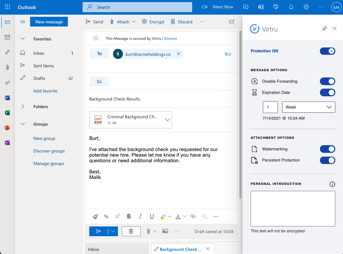
.png?width=303&height=270&name=togglezoom-quarterlyreport@2x%20(1).png)
Screenshots Pictured: Virtru for Outlook | Virtru for Gmail
Granular Access Controls That Increase Control and Undo Mistakes
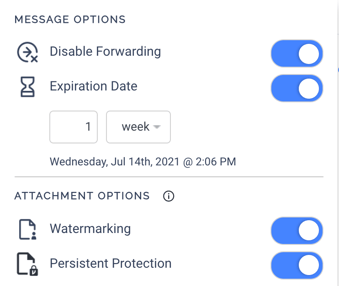
Virtru uses the Trusted Data Format (TDF) to protect individual emails with encrypted wrappers, and imbue them with features and controls that the sender has complete domain over. TDF binds the encrypted data with the policies using public-based signatures, ensuring policies cannot be tampered with. Only the data owner (or the organization's Virtru admin) can adjust control policies, maintaining the integrity of the data itself and its final destination. Only the intended recipients have the ability to decrypt the data, as their identity is tied to the email itself before it is sent. Once received, Access-Based Access Controls (ABAC) mandate what recipients can do with the emails once received.
ABAC policies include the ability to revoke access to the email at any point in time, set expiration dates, enable or disable forwarding, prevent file downloading, and even watermark files within emails. All of this is possible to the end user with minimal effort.
Email Encryption Key Management for Data Sovereignty
Virtru enables you to easily host your own decryption keys, allowing you to benefit from industry-standard tools without fear of key exposure. Through Virtru Private Keystore, you have the option to choose where to store your private keys: in a public or private cloud, a private or co-hosted data center, or a hardware security module (HSM).
In simple terms, Virtru encrypts your emails with TDF. Then, enables you to wrap it again using a private key that remains in your environment and will never be exposed to us or your cloud provider. Virtru manages the intricacies of policies, storage, and key exchanges on your behalf, and the double-key encryption guarantees that we never have access to your sensitive data. Virtru Private Keystore provides an extra layer of protection, whether you're using PGP, S/MIME, or one of Virtru's email encryption solutions.
Data Loss Prevention for Backup
Virtru email encryption empowers administrators to tailor robust DLP policies to align with an organization's data security and compliance prerequisites. Virtru can implement automatic protection using custom logic by scanning various email fields such as subject line, body, and attachments. For those who regularly transmit confidential information, personalized DLP policies can further decrease the likelihood of data loss or breaches.
Learn more about Virtru Email Encryption for Outlook and Gmail
Conclusion: The Struggle Is Real, But So Are the Solutions
Email encryption might seem hard to use — and judging by the current landscape of email encryption providers, it often is. The constant hassle of poor user experience and low adoption, paired with technical issues like key management, infrastructure, and inconsistent compatibility make email encryption appear, understandably, difficult.
But with hardship comes innovation. Cyber threats aren’t going anywhere, and as the demand for easy, clean, and streamlined email encryption increases — innovations in encryption protocols, user experience, and accessibility are blooming.
It’s happening at places like Virtru, where our team is constantly raising the bar to make email encryption easier than it’s ever been. To learn more about Virtru for Microsoft 365 and Google Workspace, or to learn about our other security solutions like secure file transfer, automated data protection gateway, app encryption, or key management, book a demo with us today.

Shelby Imes
Shelby is the Manager of Content Strategy at Virtru with a specialty in SEO, social media, and digital campaigns. She has produced content for major players in healthcare, home services, broadcast media, and now data security.
View more posts by Shelby ImesSee Virtru In Action
Sign Up for the Virtru Newsletter
/blog%20-%20metadata%20on%20data/metadata-on-data.webp)

/blog%20-%20Ravenna%20Hub/ravenna-hub.webp)




/blog%20-%20HIO%20Maya%20HTT/Maya-HTT-Level-2-lessons%20copy.webp)

/blog%20-%20cmmc%20level%203/CMMC-LEVEL-3.webp)
