CJIS Compliance and Data Encryption — Here’s What You Need to Know


Each day, criminal justice and law enforcement agencies on the local, state and federal levels access the Criminal Justice Information Services (CJIS) databases for information necessary to catch lawbreakers, perform background checks, and track criminal activity. Obviously, it’s important that this data not fall into the wrong hands — while the loss of business intelligence can mean a major financial hit, the security of CJIS data could mean the difference between thwarting a criminal operation and allowing another to occur. It could also jeopardize the privacy and safety of the individuals whose records are being accessed and shared.
CJIS compliance keeps networks on the same page when it comes to data security and encryption, and ensures that sensitive criminal justice data is locked down. But, before we dig into the checklist of rules to follow to become CJIS compliant, let’s take a closer look at the CJIS.
CJIS — What It Is and How to Stay CJIS Compliant
Established in 1992, CJIS is the largest division of the FBI, and comprises several departments, including the National Crime Information Center (NCIC), Integrated Automated Fingerprint Identification System (IAFIS) and the National Instant Criminal Background Check System (NICS). CJIS monitors criminal activities in local and international communities using analytics and statistics provided by law enforcement, and their databases provide a centralized source of criminal justice information (CJI) to agencies around the country.
The world has changed a lot since 1992, and the proliferation of the Internet and the cloud, combined with the growing rate and sophistication of cyber security threats, have made protecting CJIS data more complicated than ever. Because of this growing concern, CJIS developed a set of security standards for organizations, cloud vendors, local agencies and corporate networks.
The policies set forth by CJIS cover best practices in wireless networking, remote access, data encryption and multiple authentication. Some basic rules include:
- A limit of 5 unsuccessful login attempts by a user accessing CJIS
- Event logging various login activities, including password changes
- Weekly audit reviews
- Active account management moderation
- Session lock after 30 minutes of inactivity
- Access restriction based on physical location, job assignment, time of day, and network address
The CJIS Advanced Authentication Requirement
FBI Security Policy section 5.6.2.2.1, or the Advanced Authentication Requirement, compels agencies to use multi-factor authentication when accessing CJI. Multi-factor authentication, or MFA, is a best practice for accounts that contain sensitive information, such as your bank accounts or email. It requires an additional level of authentication to ensure you are who you say you are, beyond just having your password.
One common type of multi-factor authentication involves a software application or physical device that generates a unique, one-time password at timed intervals. This wildcard password (what you have) adds a second level of complexity to your password (what you know), providing multiple barriers of entry to potential data thieves.
CJIS Compliance and Data Encryption
The CJIS has also established requirements for the use of data encryption when storing and using sensitive data, as well as including CJI in communications. A minimum of 128 bit encryption is required, and keys used to decrypt data must be adequately complex (at least 10 characters long, a mix of upper and lowercase letters, numbers and special characters) and changed as soon as authorized personnel no longer need access.
Like multi-factor authentication, data encryption adds an extra layer of security to your data — if a criminal gains access to an encrypted file or communication, that information is useless without the key to decrypt it.
Email presents its own CJIS compliance challenges. A tremendous amount of criminal justice information is exchanged via email and standard email services do not offer the encryption required by CJIS. Most third-party encryption services are either difficult to use, expensive, or both. Many also require senders or receivers to establish new accounts to view CJIS-compliant emails. Virtru offers an alternative: cost effective, easy-to-use email encryption that integrates directly with Outlook and Gmail.
CJIS Requirements for File Sharing
In addition to email workflows, file sharing workflows also present a challenge for CJIS compliance: state, local, and federal agencies often need the ability to securely share sensitive records and files — whether internally within their agency, or externally with other law enforcement partners.
Virtru Secure Share can be a vital tool for law enforcement agencies and other CJIS-bound organizations to securely collect, share, and protect CJI data to get their jobs done. It's a simple, streamlined way to share encrypted files that are too large for email (think surveillance footage, photos, or large case files). Virtru Secure Share supports files up to 15 GB.
Unlike legacy file-sharing protocols like SFTP, Virtru Secure Share is a highly secure and highly simple workflow that makes it easy for senders and recipients both: There's no software to install, and no new accounts to create. As with Virtru email encryption, Secure Share users and recipients authenticate with their existing credentials: No new accounts, no new passwords to remember.
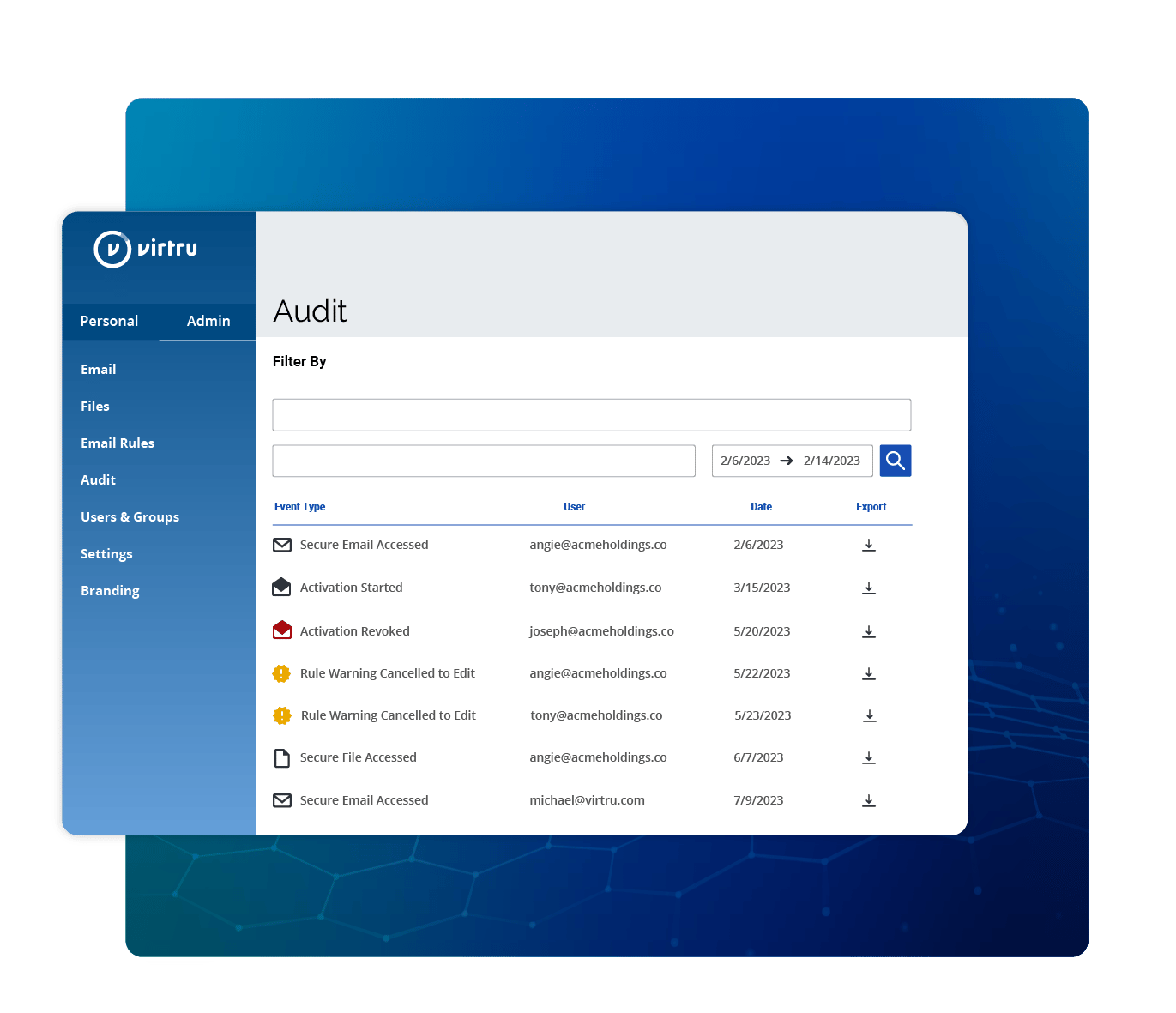
CJIS Audit Trail and Persistent Data Control
Virtru provides a clear and consistent audit trail for CJIS audit and compliance support. Admins can view the organization's entire scope of secure data sharing in the Virtru Control Center. This allows for full transparency of encrypted emails and files, all in one place.
One feature that admins and users love about Virtru is the ability to revoke or change access permissions at any time: If someone accidentally sends CJI to the wrong person, for example, either the admin or the user can revoke access at any time, and they can also see whether that person opened the email or file. This provides peace of mind in a world where human error is all too common.
Personnel and Training Considerations
Knowing what your agency needs to maintain CJIS compliance is one thing, but putting it into practice is another. It’s critical that you provide frequent staff training on CJIS best practices, make sure there’s ample documentation and knowledge sharing and implement agency-wide security protocols and password requirements.
Organizations can hire IT consultants, devote a department strictly for CJIS compliance and build the necessary infrastructure required to support the official policies. Alternatively, they can outsource their data protection services to companies that specialize in CJIS compliance. This may be a good long-term solution for agencies and contractors that want to streamline their CJIS compliance efforts without making huge investments in staffing and infrastructure.
At the end of the day, a security solution is only as good as its usability: You'll want to select easy tools that don't disrupt employee workflows or impede their ability to get their jobs done. This means prioritizing tools that:
- Integrate with the apps people already use every day
- Facilitate collaboration instead of limiting it
- Are easy for senders and recipients alike
- Provide strong visibility and control for administrators
The Impacts of CJI Data Loss
Loss of access to CJI can cripple an agency’s ability to do its job — not to mention jeopardize public safety. If CJI access is part of your agency’s operations, always err on the side of caution when it comes to data security, and stay on top of your compliance audits. Security investment, however hard on your budget, is always preferable to a leak or loss of critical criminal justice intelligence.
Thankfully, there are tools out there — like Virtru — that make it easy to safeguard this vital intelligence, while supporting compliance and providing transparency into, and control over, sensitive data at all times.
Strengthen CJIS Compliance with Virtru
Virtru is a robust data encryption and access control service for secure email communications and file transfer. The security company offers client-side encryption that helps organizations comply with CJIS, HIPAA and FERPA regulatory requirements for encrypted email and secure collaboration.
Ready to start the conversation? Contact our team for a demo.

Editorial Team
The editorial team consists of Virtru brand experts, content editors, and vetted field authorities. We ensure quality, accuracy, and integrity through robust editorial oversight, review, and optimization of content from trusted sources, including use of generative AI tools.
View more posts by Editorial TeamSee Virtru In Action
Sign Up for the Virtru Newsletter




/blog%20-%20HIO%20Maya%20HTT/Maya-HTT-Level-2-lessons%20copy.webp)

/blog%20-%20cmmc%20level%203/CMMC-LEVEL-3.webp)

/blog%20-%207%20Healthcare%20Vulnerabilities/7-hipaa-vulns.webp)
/blog%20-%20please%20delete%20that%20email.%20domain%20wide%20protection/please-delete-that-email.webp)
/blog%20-%20next%20breakfast/next-breakfast-2.png)