Virtru SKO: Accelerating Data-Centric Security, Compliance, and Privacy for All


We're only one month into the 2023 new year, and the world has already witnessed numerous high-profile security breaches and data leaks including incidents at T-Mobile, PayPal, Chick-Fil-A, and Twitter.
Make no mistake: These organizations are NOT mom-and-pop shops with limited IT resources. They are global brands with sizable cybersecurity teams making significant investments in people, processes, and tools to minimize risk. So why, then, do so many sophisticated enterprises continue to suffer cyber attacks and loss of sensitive data?
In my humble opinion, there are three simple reasons:
1. It's impossible for any organization to be perfect.
Even the largest engineering teams in the world, equipped with the largest security budgets, regularly find themselves on the losing end of the cyber game. Anyone responsible for managing cyber risk at a company of any size commonly finds themselves frantically competing on a playing field that is constantly changing against an adversary that is increasingly sophisticated. It's whack-a-mole gone wild. It's an easy game to lose, and impossible to win 100% of the time.
2. Too many organizations over-index on perimeter-centric security.
Breaches are often the result of too much emphasis on perimeter-centric security initiatives. Specifically, bad things tend to happen when cyber teams become myopically focused on conventional controls. These controls, while important, are aimed at governing how identities and endpoints are authenticating and using networks to access apps and sensitive data that organizations possess internally. But that's just a fraction of the data that needs protecting.
3. Too many organizations under-index on data-centric security.
Breaches and compliance missteps also tend to happen when organizations fail to focus enough attention on data-centric security, and specifically on protecting massive amounts of sensitive information which employees intentionally share externally via email, files, and application workflows.
Where should you focus your cybersecurity strategy in 2023?
Against this backdrop, my colleagues and I hosted Virtru's annual Sales Kickoff (SKO) last week in Washington, DC. During the event we had the privilege of hearing from dozens of Virtru customers, including the world's largest bank, a multi-billion dollar defense contractor, and one of the world's largest NGOs.
In every instance, these customers happily shared how Virtru products have helped them improve data-centric security, compliance, and privacy on a very specific part of the cyber risk landscape. What part of the landscape? It's NOT the part that pertains to "pipeline-centric security" or "perimeter-centric security." Instead, it's the portion highlighted in the lower right corner of the graphic below, which involves employees intentionally sharing massive amounts of sensitive data externally with third parties to get business done.
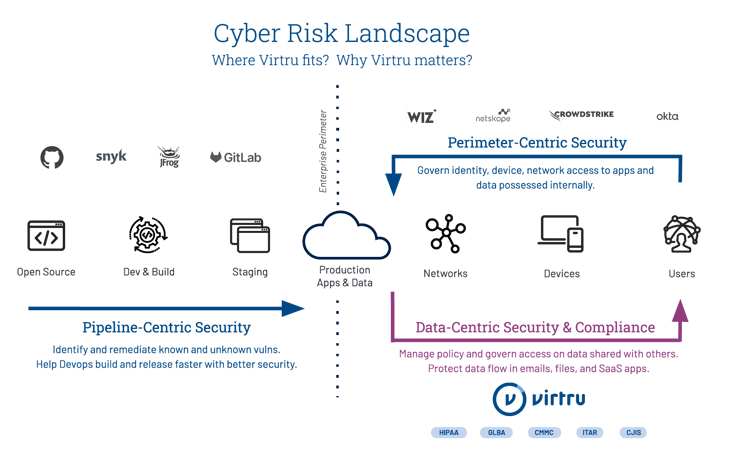
So, as we prepare to execute our sales and marketing plan in 2023, we've developed a very simple narrative that is based entirely on the success that we've already had helping 7,500 customers adopt data-centric security. TL;DR: Our customer-driven messaging goes like this:
- Git-R-Done: Employees in every business, in every industry, intentionally share tons of sensitive data externally via email, files, and SaaS application workflows. Simply stated, sharing data with others is how business gets done. But, often times, companies don't do enough to protect such data.
- Data Conundrum: This reality leads directly to a "conundrum" whereby companies, despite lacking appropriate data-centric security controls, intentionally share their most sensitive data externally in order to get work done. The result is a collection of complicated security and compliance risks that are fundamentally ignored by conventional perimeter-centric security tools.
- One Piece, Big Puzzle: Today's cyber risk landscape is broad and getting broader by the day. From pipeline-centric security, to perimeter-centric security, to data-centric security, the cyber risk landscape has evolved into a big and complicated puzzle. Minimizing risk across the entire spectrum requires organizations to assemble the right puzzle pieces together.
- Proof is in the Pudding: From Gartner, to NIST, to NATO — industry leaders everywhere understand the growing importance of data-centric security as a unique complement to traditional security controls. Furthermore, more than 7,000 customers already trust Virtru to deliver affordable and easy-to-implement solutions that work as advertised.
- Open Platform Enabling Multiple Apps: Virtru has long been known for its industry leading end-to-end email security product, which includes a remarkably elegant experience not just for people sending encrypted data via Gmail or Microsoft Office 365, but also for people receiving encrypted data. However, what many people don't know is that Virtru's best-in-class email product, and every application we offer, is powered by a common platform consisting of an open core and a collection of innovative and proprietary services.
As shown in the image below, our stack consists of a collection of data-centric security applications built on top of a common platform, starting first with email workflows, expanding into file workflows, and then into SaaS workflows. Further, our uniquely flexible architecture enables customers to implement "client-side" and or "server-side" controls depending on specific use cases. For example, client-side controls enable true end-to-end encryption and data protection which is perfect for organizations seeking to comply with regulatory standards like CMMC 2.0, ITAR, and CJIS. Conversely, our server-side controls offer a rapid time-to-value and highly scalable solution for large enterprises seeking to implement data-centric security in support of hundreds of thousands of employees. We have also leveraged the Virtru Data Security Platform to introduce a collection of private key management services, which enable corporations to embrace privacy enhanced collaboration and computing offers from Google cloud.
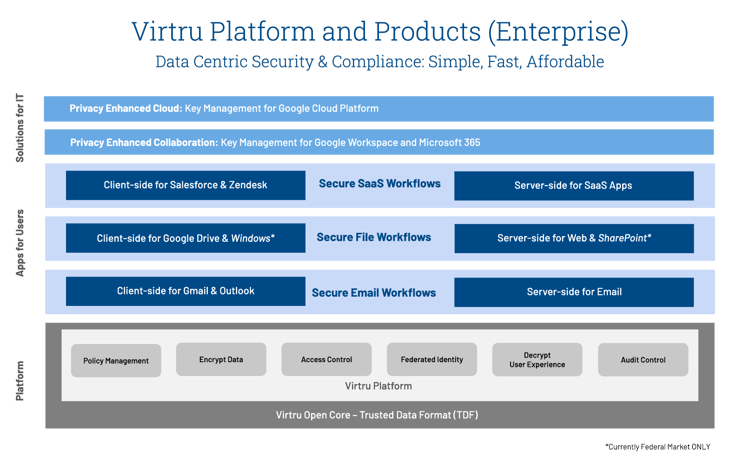
Adopting data-centric security governance requires IT teams to expand their focus beyond traditional "pipeline-centric" and "perimeter-centric" security workflows. It requires teams to implement granular security controls for the thing that matters most: The massive amount of sensitive data which your business voluntarily shares externally every single day.

Matt Howard
A proven executive and entrepreneur with over 25 years experience developing high-growth software companies, Matt serves as Virtu’s CMO and leads all aspects of the company’s go-to-market motion within the data protection and Zero Trust security ecosystems.
View more posts by Matt HowardSee Virtru In Action
Sign Up for the Virtru Newsletter










