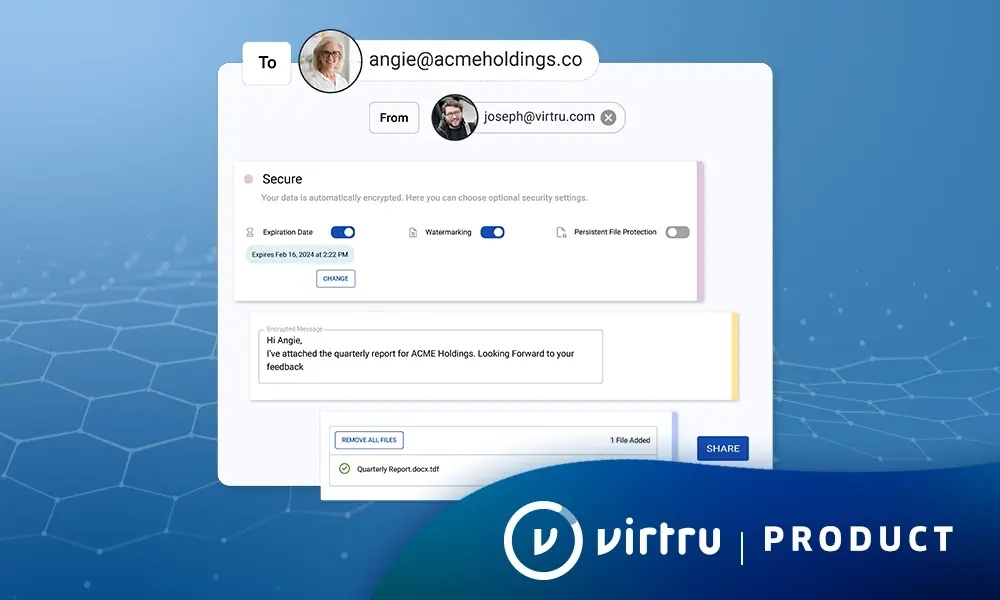
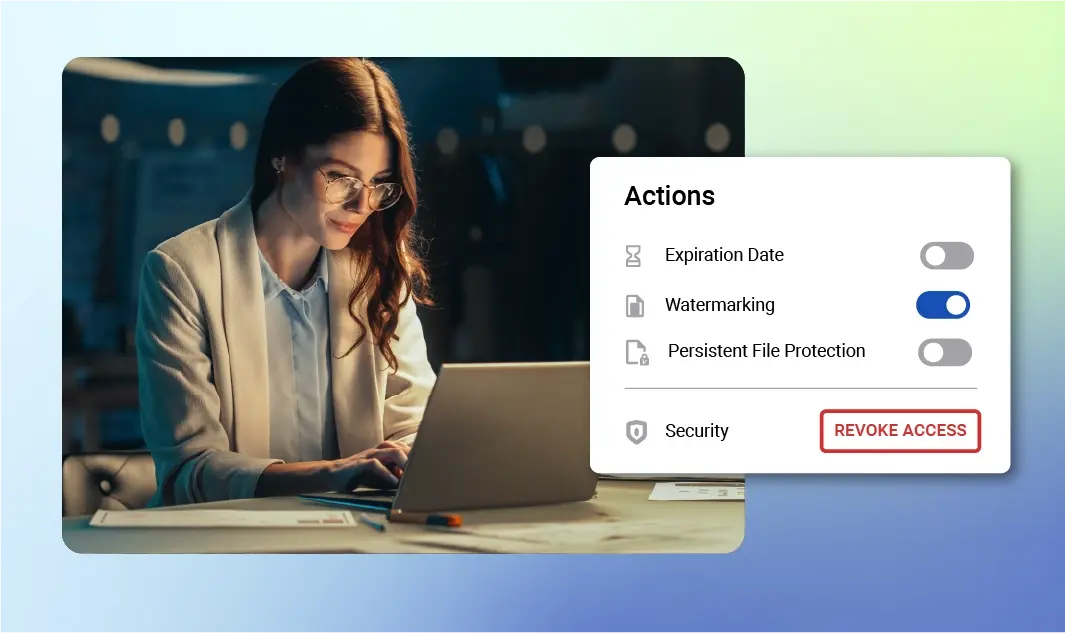
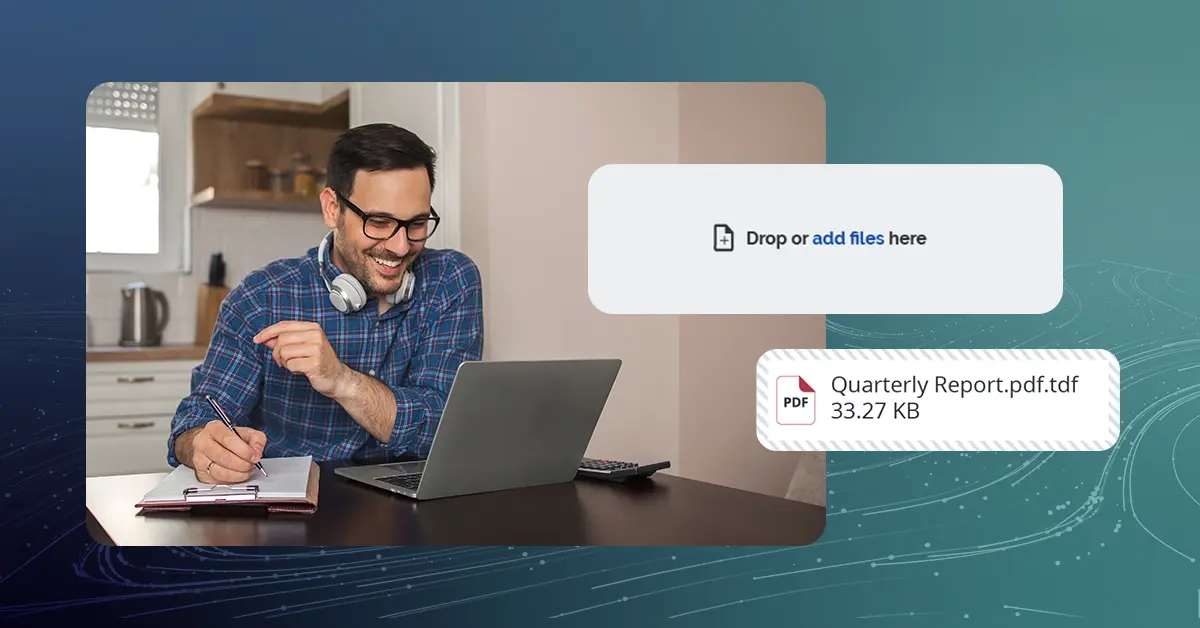
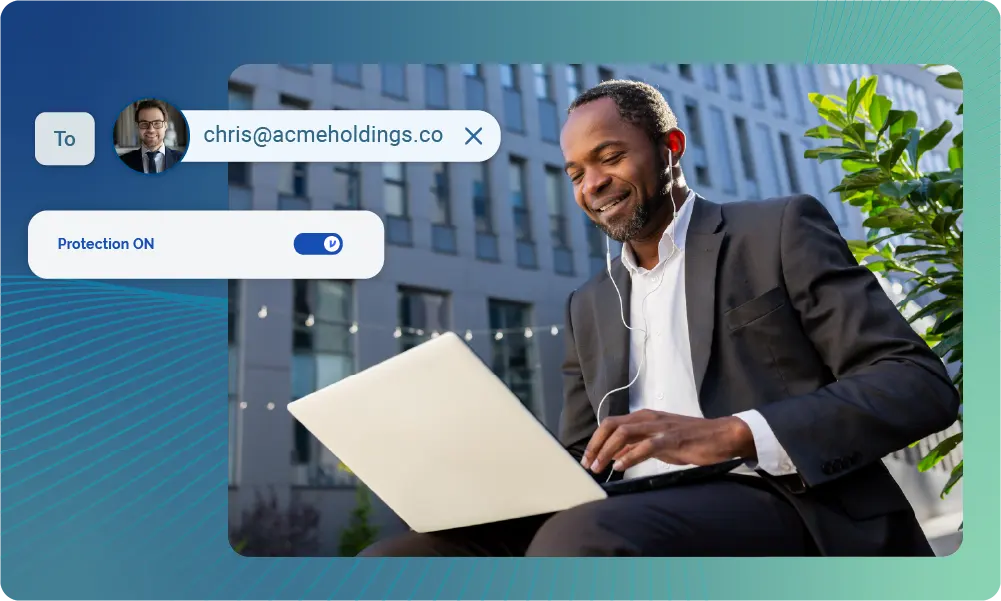
Decrypted
The Virtru Blog
Tips, takes, and expertise for the data-centric security practitioner

XChat's Launch and Why End-to-End Encryption Remains the Gold Standard
X's recent rollout of XChat, its revamped direct messaging feature, has sparked an important conversation about privacy, ...
Read Post
Popular Posts

Education
The Secured Academy: EDUCAUSE Panel Reveals How CMMC is Transforming Research

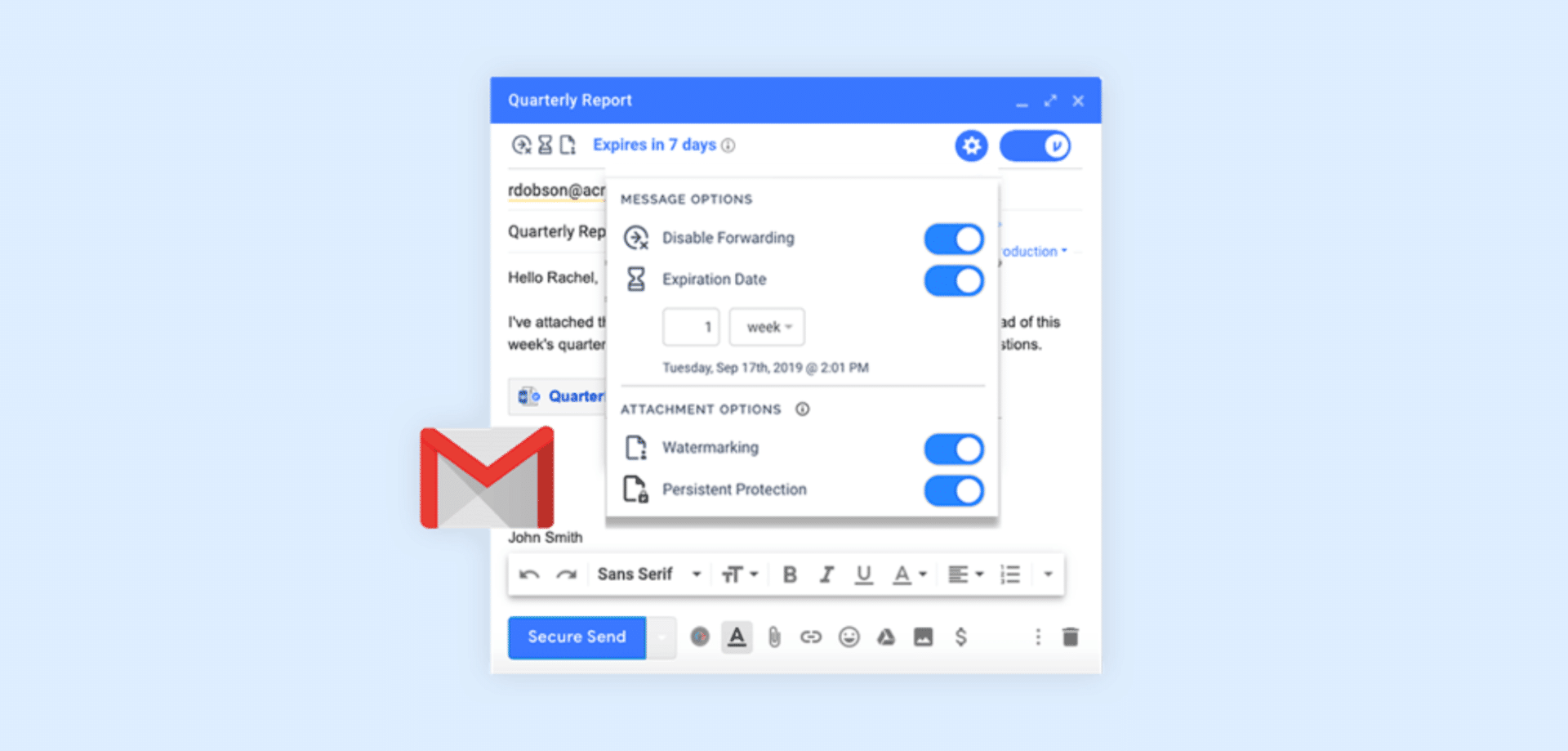
Virtru Private Keystore
Technology & Telecom
What Is a Blind Subpoena, and How Can You Protect Your Data?

Virtru for Outlook
HIPAA
Healthcare
Virtru for Gmail