Decrypted
The Virtru Blog
Tips, takes, and expertise for the data-centric security practitioner

Virtru Private Keystore
Technology & Telecom
May 27, 2025
What Is a Blind Subpoena, and How Can You Protect Your Data?
It’s always been tough for security leaders to stay ahead of the curve, but the pace has ratcheted up in 2025: Data security ...
Read Post
Popular Posts

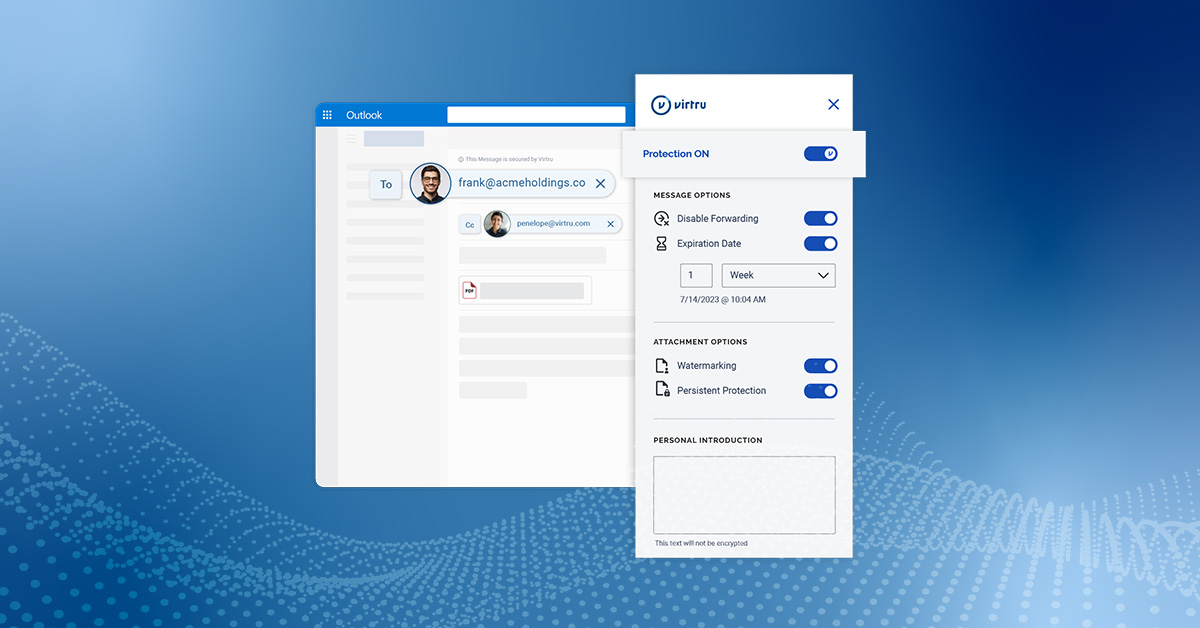
Virtru for Outlook
HIPAA
Healthcare
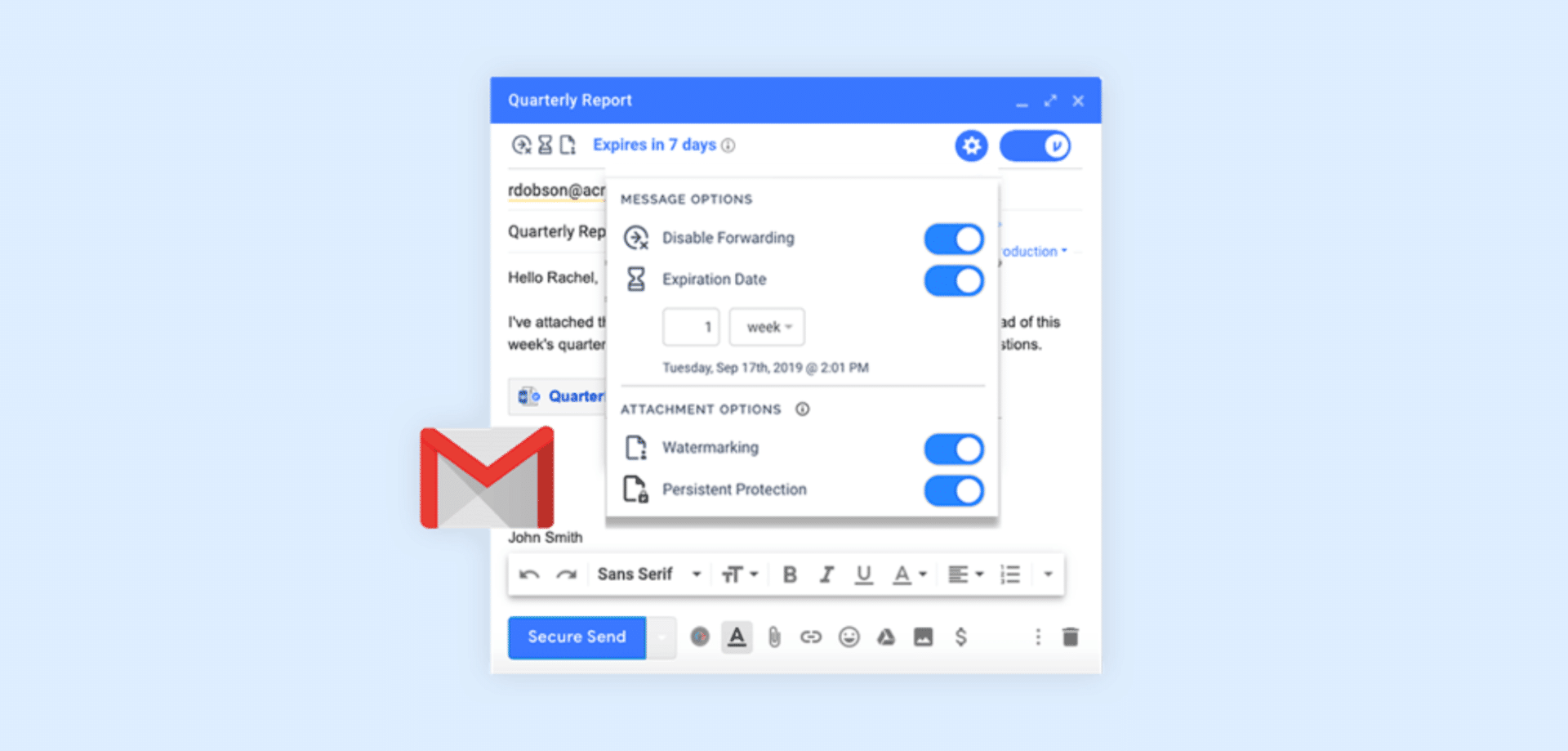
Virtru for Gmail
HIPAA Breach Response: How to Prevent, Mitigate, or Resolve Leaked PHI

Club FedRAMP: Varonis joins Virtru as an Authorized Data Security Platform Provider